The infamous cybercrime syndicate recognized as FIN7 has been connected to a spear-phishing marketing campaign focusing on the U.S. automotive industry to provide a identified backdoor termed Carbanak (aka Anunak).
“FIN7 recognized workforce at the company who labored in the IT office and had bigger concentrations of administrative rights,” the BlackBerry analysis and intelligence group explained in a new write-up.
“They applied the entice of a no cost IP scanning software to run their effectively-acknowledged Anunak backdoor and acquire an original foothold using living off the land binaries, scripts, and libraries (LOLBAS).”

FIN7, also identified as Carbon Spider, Elbrus, Gold Niagara, ITG14, Sangria Tempest, is a very well-regarded financially inspired e-criminal offense group that has a monitor report of placing a broad range of marketplace verticals to deliver malware capable of thieving information from level-of-sale (PoS) techniques considering that 2012.
In recent decades, the threat actor has transitioned to conducting ransomware operations, offering a variety of strains like Black Basta, Cl0p, DarkSide, and REvil. Two Ukrainian associates of the group, Fedir Hladyr and Andrii Kolpakov, have been sentenced to prison in the U.S. to date.
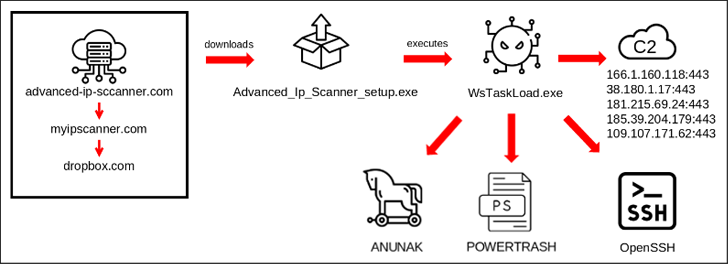
The most current marketing campaign found by BlackBerry in late 2023 starts with a spear-phishing email that embeds a booby-trapped website link pointing to a bogus web page (“state-of-the-art-ip-sccanner[.]com”) that masquerades as State-of-the-art IP Scanner.
“This fake site redirected to ‘myipscanner[.]com,’ which in transform redirected to an attacker-owned Dropbox that downloaded the destructive executable WsTaskLoad.exe on to the victim’s equipment,” the Canadian cybersecurity corporation explained.

The binary, for its component, initiates a multi-phase process that ultimately sales opportunities to the execution of Carbanak. It really is also created to produce added payloads these as POWERTRASH and create persistence by putting in OpenSSH for distant entry.
It can be currently not regarded if the risk actors have been scheduling on deploying ransomware, as the contaminated process was detected early on and removed from the network right before it could achieve the lateral movement phase.
Although the concentrate on of the attack was a “large multinational automotive manufacturer” centered in the U.S., BlackBerry mentioned it discovered numerous equivalent malicious domains on the similar service provider, indicating that it may possibly be part of a wider marketing campaign by FIN7.
To mitigate the dangers posed by these kinds of threats, it’s advised that companies be on the lookout for phishing attempts, help multi-component authentication (MFA), maintain all software program and devices up-to-day, and check for abnormal login attempts.
Uncovered this article fascinating? Adhere to us on Twitter and LinkedIn to study additional unique articles we write-up.
Some parts of this article are sourced from:
thehackernews.com


 Recover from Ransomware in 5 Minutes—We will Teach You How!
Recover from Ransomware in 5 Minutes—We will Teach You How!