Condition-sponsored danger actors from the Democratic People’s Republic of Korea (DPRK) have been uncovered focusing on blockchain engineers of an unnamed crypto exchange system through Discord with a novel macOS malware dubbed KANDYKORN.
Elastic Security Labs mentioned the activity, traced again to April 2023, exhibits overlaps with the infamous adversarial collective Lazarus Team, citing an investigation of the network infrastructure and methods made use of.
“Menace actors lured blockchain engineers with a Python application to gain original accessibility to the natural environment,” security researchers Ricardo Ungureanu, Seth Goodwin, and Andrew Pease reported in a report revealed now.
“This intrusion concerned several intricate stages that every single used deliberate defense evasion approaches.”

This is not the initial time the Lazarus Team has leveraged macOS malware in its assaults. Earlier this 12 months, the danger actor was noticed distributing a backdoored PDF application that culminated in the deployment of RustBucket, an AppleScript-primarily based backdoor capable of retrieving a second-stage payload from a distant server.
What will make the new campaign stand out is the attacker’s impersonation of blockchain engineers on a community Discord server, using social engineering lures to trick victims into downloading and executing a ZIP archive that contains destructive code.
“The target considered they were setting up an arbitrage bot, a software resource capable of profiting from cryptocurrency fee dissimilarities between platforms,” the researchers stated. But in reality, the attack chain paved the way for the shipping and delivery of KANDYKORN following a five-stage process.

“KANDYKORN is an sophisticated implant with a wide range of abilities to observe, interact with, and keep away from detection,” the researchers explained. “It utilizes reflective loading, a direct-memory variety of execution that may bypass detections.”
The starting off place is a Python script (watcher.py), which retrieves yet another Python script (testSpeed.py) hosted on Google Generate. This dropper, for its element, fetches just one much more Python file from a Google Drive URL, named FinderTools.
FinderTools also features as a dropper, downloading and executing a hidden second phase payload referred to as SUGARLOADER (/End users/shared/.sld and .log) that eventually connects to a distant server in get to retrieve KANDYKORN and execute it immediately in memory.
SUGARLOADER is also dependable for launching a Swift-based self-signed binary known as HLOADER that attempts to go off as the reputable Discord software and executes .log (i.e., SUGARLOADER) to achieve persistence using a approach termed execution circulation hijacking.
KANDYKORN, which is the final-phase payload, is a full-showcased memory resident RAT with crafted-in capabilities to enumerate files, run further malware, exfiltrate knowledge, terminate procedures, and run arbitrary instructions.

“The DPRK, via models like the LAZARUS Group, carries on to concentrate on crypto-marketplace firms with the intention of thieving cryptocurrency in purchase to circumvent international sanctions that hinder the growth of their economic climate and ambitions,” the researchers reported.
Kimsuky Resurfaces with Current FastViewer Malware
The disclosure comes as the S2W Danger Assessment team uncovered an current variant of an Android spyware named FastViewer that is employed by a North Korean threat cluster dubbed Kimsuky (aka APT43), a sister hacking outfit of the Lazarus Group.
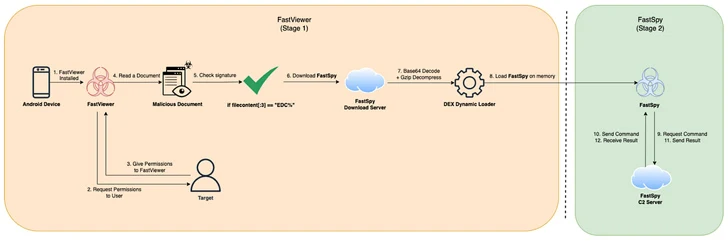
FastViewer, very first documented by the South Korean cybersecurity firm in October 2022, abuses Android’s accessibility products and services to covertly harvest sensitive data from compromised products by masquerading alone as seemingly harmless security or e-commerce applications that are propagating by using phishing or smishing.
It is also built to download a next-stage malware named FastSpy, which is primarily based on the open-supply project AndroSpy, to execute information collecting and exfiltration instructions.
“The variant has been in creation since at minimum July 2023 and, like the original version, is uncovered to induce set up by distributing repackaged APKs that involve malicious code in authentic apps,” S2W claimed.
A single noteworthy component of the new edition is the integration of FastSpy’s operation into the FastViewer, hence obviating the need to have to obtain added malware. That explained, S2W claimed “there are no regarded scenarios of this variant being distributed in the wild.”
Discovered this short article exciting? Stick to us on Twitter and LinkedIn to read much more exceptional content material we article.
Some parts of this article are sourced from:
thehackernews.com


 Turla Updates Kazuar Backdoor with Advanced Anti-Analysis to Evade Detection
Turla Updates Kazuar Backdoor with Advanced Anti-Analysis to Evade Detection