A threat actor affiliated with Iran’s Ministry of Intelligence and Security (MOIS) has been observed waging a complex cyber espionage campaign concentrating on economic, authorities, navy, and telecommunications sectors in the Middle East for at the very least a year.
Israeli cybersecurity agency Test Stage, which uncovered the marketing campaign alongside Sygnia, is tracking the actor beneath the name Scarred Manticore, which is reported to closely overlap with an emerging cluster dubbed Storm-0861, one of the four Iranian teams joined to destructive assaults on the Albanian govt past yr.
Victims of the procedure span many nations these as Saudi Arabia, the United Arab Emirates, Jordan, Kuwait, Oman, Iraq, and Israel.
Scarred Manticore also reveals some diploma of overlap with OilRig, an additional Iranian country-point out crew that was just lately attributed to an attack on an unnamed Middle East federal government among February and September 2023 as component of an eight-month-very long campaign.

One more established of tactical overlaps have been uncovered among the adversary and an intrusion set codenamed ShroudedSnooper by Cisco Talos. Attack chains orchestrated by the menace actor have singled out telecom providers in the Middle East applying a stealthy backdoor known as HTTPSnoop.
The action represented by Scarred Manticore is characterized by the use of a beforehand unknown passive malware framework referred to as LIONTAIL that’s put in on Windows servers. The danger actor is thought to be lively due to the fact at least 2019.
“Scarred Manticore has been pursuing high-price targets for yrs, using a wide variety of IIS-primarily based backdoors to attack Windows servers,” Look at Issue scientists explained in a Tuesday analysis. “These incorporate a wide range of personalized web shells, customized DLL backdoors, and driver-dependent implants.”
An innovative piece of malware, LIONTAIL is a assortment of personalized shellcode loaders and memory resident shellcode payloads. A noteworthy part of the framework is a lightweight-yet-complex implant penned in C that enables attackers to execute instructions remotely by means of HTTP requests.
The attack sequences entail infiltrating publicly going through Windows servers to kick off the malware supply course of action and systematically harvest sensitive details from infected hosts.
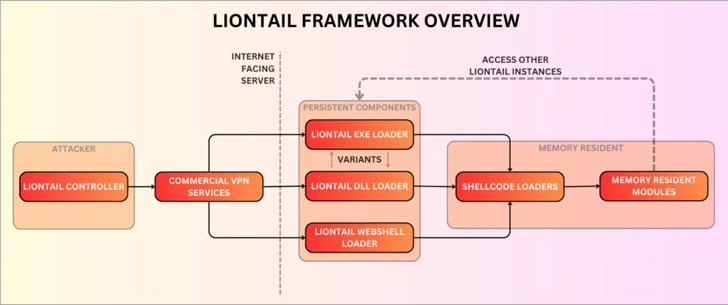
“Rather of applying the HTTP API, the malware employs IOCTLs to interact specifically with the underlying HTTP.sys driver,” the scientists claimed, detailing the command-and-command (C2) system.
“This approach is stealthier as it does not involve IIS or HTTP API, which are commonly intently monitored by security solutions, but is not a clear-cut process specified that the IOCTLs for HTTP.sys are undocumented and demand further exploration efforts by the threat actors.”
Also deployed alongside LIONTAIL incorporate various web shells and a web forwarder instrument called LIONHEAD, a web forwarder.
Historic action of Scarred Manticore indicates a ongoing evolution of the group’s malware arsenal, what with the danger actor earlier relying on web shells these types of as Tunna and a bespoke version identified as FOXSHELL for backdoor access.

Given that mid-2020, the menace actor is also said to have employed a .NET-centered passive backdoor identified as SDD that establishes C2 conversation via an HTTP listener on the contaminated machine with the best intention of executing arbitrary commands, uploading and downloading documents, and jogging extra .NET assemblies.
The progressive updates to the danger actor’s methods and tools is regular of state-of-the-art persistent risk (APT) groups and demonstrates their methods and diversified skills. This is greatest exemplified by Scarred Manticore’s use of a destructive kernel driver referred to as WINTAPIX that was uncovered by Fortinet before this Might.
In a nutshell, WinTapix.sys functions as a loader to execute the future phase of the attack, injecting an embedded shellcode into a suitable person mode approach that, in turn, executes an encrypted .NET payload precisely created to concentrate on Microsoft Internet Details Services (IIS) servers.
The focusing on of Israel comes amid the ongoing Israel-Hamas war, prompting reduced-sophistication hacktivist groups to attack numerous organizations in the nation, as well as nations like India and Kenya, suggesting nation-condition actors’ reliance on info operations aimed at influencing the international notion of the conflict.
“LIONTAIL framework parts share related obfuscation and string artifacts with FOXSHELL, SDD backdoor, and WINTAPIX drivers,” Verify Stage said.
“Inspecting the heritage of their functions, it gets obvious how considerably the threat actor has arrive in strengthening their assaults and maximizing their technique which relies on passive implants.”
Discovered this short article fascinating? Comply with us on Twitter and LinkedIn to go through more special material we put up.
Some parts of this article are sourced from:
thehackernews.com


 North Korean Hackers Tageting Crypto Experts with KANDYKORN macOS Malware
North Korean Hackers Tageting Crypto Experts with KANDYKORN macOS Malware