North Korean menace actors have been connected to two campaigns in which they masquerade as both position recruiters and seekers to distribute malware and attain unauthorized employment with businesses primarily based in the U.S. and other elements of the globe.
The activity clusters have been codenamed Contagious Interview and Wagemole, respectively, by Palo Alto Networks Device 42.
Whilst the initially set of attacks aims to “infect software package builders with malware as a result of a fictitious occupation interview,” the latter is created for fiscal acquire and espionage.
“The first campaign’s objective is probably cryptocurrency theft and utilizing compromised targets as a staging atmosphere for extra attacks,” the cybersecurity enterprise stated.
The fraudulent job-trying to find action, on the other hand, consists of the use of a GitHub repository to host resumes with solid identities that impersonate people today of numerous nationalities.
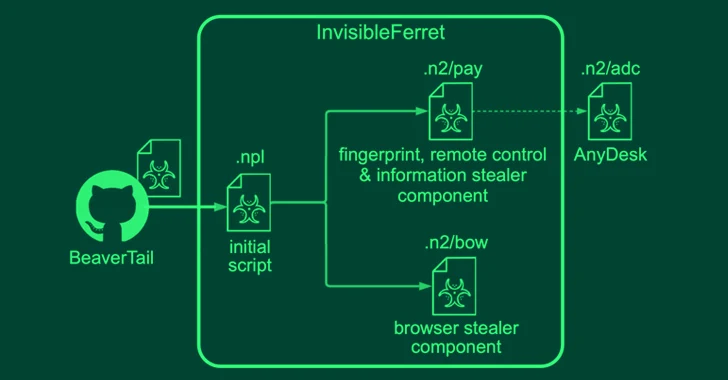
The Contagious Interview attacks pave the way for two hitherto undocumented cross-system malware named BeaverTail and InvisibleFerret that can run on Windows, Linux, and macOS devices.

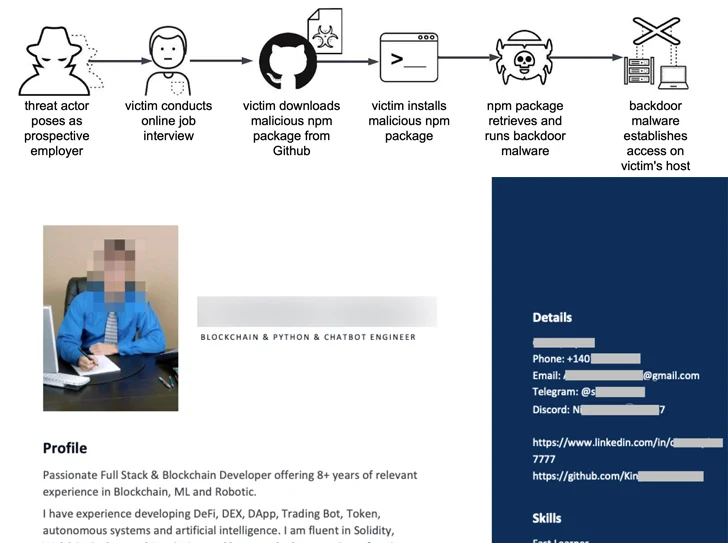
It can be value noting that the intrusion established shares tactical overlaps with earlier described North Korean risk activity dubbed Procedure Desire Job, which consists of approaching staff with opportunity occupation features and tricking them into downloading a destructive npm package deal hosted on GitHub as section of an on the web interview.
“The risk actor probable offers the deal to the victim as program to review or analyze, but it in fact consists of malicious JavaScript developed to infect the victim’s host with backdoor malware,” Unit 42 reported.
BeaverTail, the JavaScript implant, is a stealer and a loader that comes with capabilities to steal sensitive information from web browsers and crypto wallets, and provide more payloads, like InvisibleFerret, a Python-based backdoor with fingerprinting, distant control, keylogging, and info exfiltration attributes.
InvisibleFerret is also designed to download the AnyDesk shopper from an actor-managed server for remote entry.
Earlier this thirty day period, Microsoft warned that the notorious Lazarus Team sub-cluster referred to as Sapphire Sleet (aka BlueNoroff) has set up new infrastructure that impersonates skills evaluation portals as part of its social engineering strategies.
This is not the initially time North Korean menace actors have abused bogus modules in npm and PyPI. In late June and July 2023, Phylum and GitHub thorough a social engineering campaign focusing on the personalized accounts of workers functioning in technology companies with the aim of putting in a counterfeit npm offer beneath the guise of collaborating on a GitHub job.
The attacks have been attributed to a further cluster regarded as Jade Sleet, which is also named TraderTraitor and UNC4899, and has due to the fact been implicated in the JumpCloud hack that took place close to the very same time.
The discovery of Wagehole echoes a current advisory from the U.S. authorities, which disclosed North Korea’s subterfuge to defeat sanctions by dispatching an army of very-qualified IT staff who receive work in many providers globally and funnel back their wages to fund the country’s weapons applications.
“Some resumes include things like back links to a LinkedIn profile and one-way links to GitHub content,” the cybersecurity firm mentioned.

“These GitHub accounts show up nicely taken care of and have a lengthy action background. These accounts suggest regular code updates and socialization with other builders. As a consequence, these GitHub accounts are virtually indistinguishable from genuine accounts.”
“We would generate 20 to 50 faux profiles a calendar year until eventually we ended up employed,” a North Korean IT employee who a short while ago defected was quoted as indicating to Reuters, which also shared aspects of the Wagemole marketing campaign.
The advancement will come as North Korea claimed that it has properly place a military spy satellite into room, soon after two unsuccessful attempts in Could and August of this calendar year.
It also follows a new attack campaign orchestrated by the North Korea-joined Andariel team – a further subordinate factor within just Lazarus – to provide Black RAT, Lilith RAT, NukeSped, and TigerRAT by infiltrating susceptible MS-SQL servers as perfectly as by way of supply chain assaults applying a South Korean asset management program.
“Software program builders are usually the weakest backlink for supply chain assaults, and fraudulent work gives are an ongoing problem, so we hope continued exercise from Contagious Job interview,” Device 42 claimed. “Also, Wagemole represents an prospect to embed insiders in qualified providers.”
Uncovered this short article exciting? Adhere to us on Twitter and LinkedIn to examine much more exclusive articles we article.
Some parts of this article are sourced from:
thehackernews.com

 AI Solutions Are the New Shadow IT
AI Solutions Are the New Shadow IT