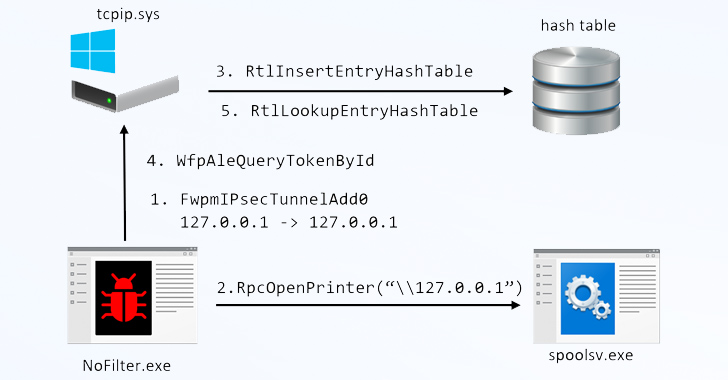
A formerly undetected attack process referred to as NoFilter has been located to abuse the Windows Filtering Platform (WFP) to realize privilege escalation in the Windows functioning method.
“If an attacker has the potential to execute code with admin privilege and the concentrate on is to execute LSASS Shtinkering, these privileges are not enough,” Ron Ben Yizhak, a security researcher at Deep Intuition, advised The Hacker Information.
“Jogging as “NT AUTHORITYSYSTEM” is essential. The strategies explained in this study can escalate from admin to Method.”
The conclusions were introduced at the DEF CON security meeting more than the weekend.

The beginning level of the investigation is an in-house tool referred to as RPC Mapper the cybersecurity company utilized to map distant procedure call (RPC) procedures, specifically those people that invoke WinAPI, primary to the discovery of a method named “BfeRpcOpenToken,” which is portion of WFP.
WFP is a established of API and technique products and services that is utilised to procedure network site visitors and allow configuring filters that permit or block communications.
“The manage desk of an additional method can be retrieved by calling NtQueryInformationProcess,” Ben Yizhak said. “This desk lists the tokens held by the course of action. The handles to people tokens can be duplicated for an additional procedure to escalate to Technique.”

Whilst obtain tokens provide to identify the person associated when a privileged activity is executed, a piece of malware working in consumer mode can entry tokens of other procedures employing certain capabilities (e.g., DuplicateToken or DuplicateHandle) and then use that token to start a little one course of action with Procedure privileges.
But the aforementioned approach, per the cybersecurity business, can be modified to perform the duplication in the kernel by means of WFP, creating it both evasive and stealthy by leaving hardly any evidence or logs.
In other words, the NoFilter can launch a new console as “NT AUTHORITYSYSTEM” or as yet another user that is logged on to the device.
“The takeaway is that new attack vectors can be uncovered by looking into constructed-in components of the OS, this sort of as the Windows Filtering Platform,” Ben Yizhak claimed, introducing the techniques “keep away from WinAPI that are monitored by security products and solutions.”
Observed this article fascinating? Stick to us on Twitter and LinkedIn to read a lot more exclusive written content we article.
Some parts of this article are sourced from:
thehackernews.com

 China-Linked Bronze Starlight Group Targeting Gambling Sector with Cobalt Strike Beacons
China-Linked Bronze Starlight Group Targeting Gambling Sector with Cobalt Strike Beacons