An lively malware campaign focusing on Latin The usa is dispensing a new variant of a banking trojan identified as BBTok, especially users in Brazil and Mexico.
“The BBTok banker has a committed functionality that replicates the interfaces of a lot more than 40 Mexican and Brazilian banking companies, and methods the victims into getting into its 2FA code to their lender accounts or into entering their payment card selection,” Check Position reported in research revealed this 7 days.
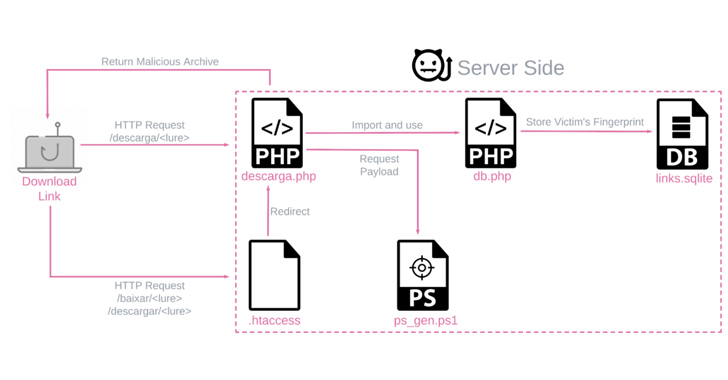
The payloads are generated by a customized server-aspect PowerShell script and are unique for each individual target primarily based on the working process and place, when becoming shipped via phishing e-mail that leverage a variety of file forms.
BBTok is a Windows-dependent banking malware that 1st surfaced in 2020. It is outfitted with characteristics that operate the common trojan gamut, allowing it to enumerate and destroy processes, issue distant commands, manipulate keyboard, and serve pretend login internet pages for banking institutions operating in the two international locations.
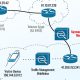
The attack chains on their own are rather simple, using bogus hyperlinks or ZIP file attachments to stealthily deploy the banker retrieved from a distant server (216.250.251[.]196) although exhibiting a decoy doc to the sufferer.

But they are also diversified for both of those Windows 7 and Windows 10 systems, primarily taking ways to evade recently applied detection mechanisms such as Antimalware Scan Interface (AMSI) that makes it possible for for scanning the machine for any threats.
Two other critical solutions to fly below the radar are the use of dwelling-off-the-land binaries (LOLBins) and geofencing checks to guarantee that the targets are only from Brazil or Mexico in advance of serving the malware by means of the PowerShell script.
The moment released, BBTok establishes connections with a remote server to obtain instructions to simulate the security verification web pages for many banking institutions.
In impersonating the interfaces of Latin American banking companies, the purpose is to harvest credential and authentication information entered by the customers to perform account takeovers of the on-line bank accounts.
“What’s noteworthy is the operator’s careful technique: all banking functions are only executed on direct command from its C2 server, and are not instantly carried out on each infected process,” the enterprise mentioned.
Check out Point’s assessment of the malware has revealed a major advancement to its obfuscation and targeting due to the fact 2020, growing outside of Mexican banking companies. The existence of Spanish and Portuguese language in the source code as effectively as in phishing e-mails features a trace as to the attackers’ origin.
Much more than 150 users are approximated to have been infected by BBTok, based mostly on an SQLite databases uncovered in the server hosting the payload technology part that information obtain to the destructive application.
The concentrating on and the language factors to the threat actors possible functioning out of Brazil, which continues to be the epicenter of strong fiscally-focused malware.
Future WEBINARAI vs. AI: Harnessing AI Defenses Towards AI-Powered Threats
Completely ready to tackle new AI-pushed cybersecurity worries? Be a part of our insightful webinar with Zscaler to deal with the expanding menace of generative AI in cybersecurity.
Supercharge Your Capabilities
“Although BBTok has been ready to keep on being less than the radar due to its elusive techniques and focusing on victims only in Mexico and Brazil, it’s evident that it is nonetheless actively deployed,” Examine Place explained.
“Because of to its several capabilities, and its unique and imaginative shipping approach involving LNK documents, SMB and MSBuild, it still poses a risk to businesses and individuals in the area.”
The advancement arrives as the Israeli cybersecurity organization comprehensive a new huge-scale phishing campaign that recently targeted about 40 popular providers throughout multiple industries in Colombia with an best goal to deploy the Remcos RAT through a multi-phase an infection sequence.
“Remcos, a innovative ‘Swiss Military Knife’ RAT, grants attackers total regulate over the infected laptop and can be utilized in a wide variety of assaults. Prevalent repercussions of a Remcos infection include things like knowledge theft, observe-up infections, and account takeover,” Check Issue explained.
Uncovered this write-up interesting? Observe us on Twitter and LinkedIn to go through a lot more special material we put up.
Some parts of this article are sourced from:
thehackernews.com


 How to Interpret the 2023 MITRE ATT&CK Evaluation Results
How to Interpret the 2023 MITRE ATT&CK Evaluation Results