The a few zero-day flaws dealt with by Apple on September 21, 2023, had been leveraged as component of an iPhone exploit chain in an attempt to supply a spyware pressure named Predator targeting previous Egyptian member of parliament Ahmed Eltantawy between Might and September 2023.
“The focusing on took put right after Eltantawy publicly said his plans to operate for President in the 2024 Egyptian elections,” the Citizen Lab said, attributing the attack with substantial self-confidence to the Egyptian governing administration owing to it being a known buyer of the commercial spying instrument.
According to a joint investigation carried out by the Canadian interdisciplinary laboratory and Google’s Risk Evaluation Team (TAG), the mercenary surveillance tool is claimed to have been delivered by way of backlinks despatched on SMS and WhatsApp.
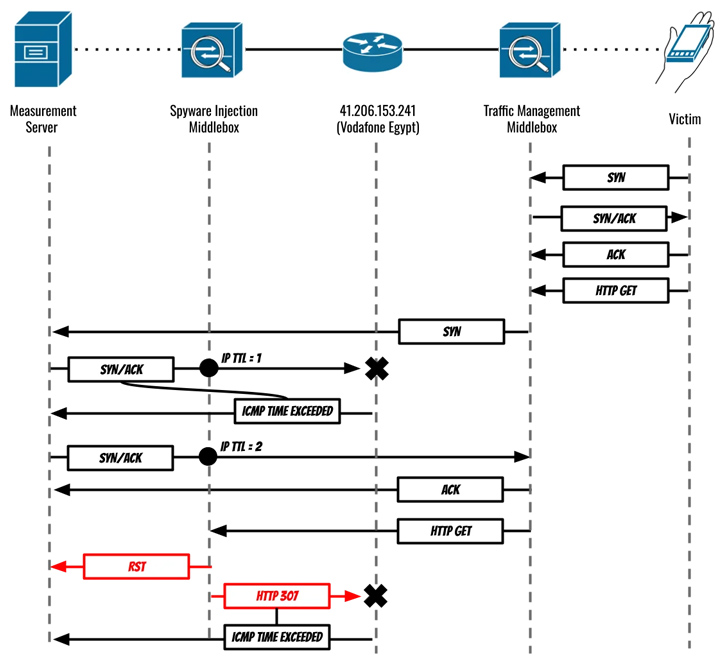
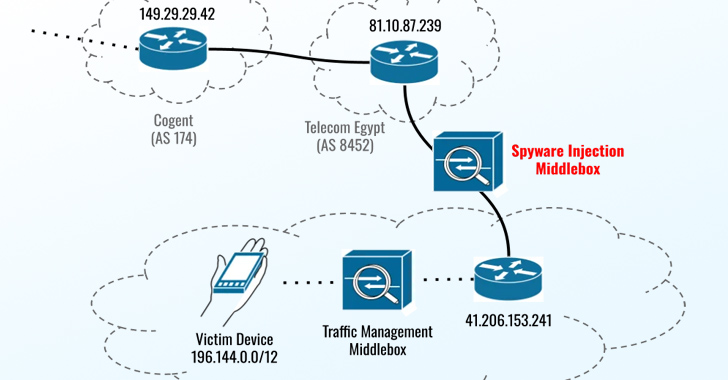
“In August and September 2023, Eltantawy’s Vodafone Egypt cellular connection was persistently selected for concentrating on through network injection when Eltantawy visited particular internet websites not employing HTTPS, a device installed at the border of Vodafone Egypt’s network routinely redirected him to a destructive web-site to infect his phone with Cytrox’s Predator spyware,” the Citizen Lab scientists claimed.

The exploit chain leveraged a set of three vulnerabilities – CVE-2023-41991, CVE-2023-41992, and CVE-2023-41993 – which could allow a destructive actor to bypass certificate validation, elevate privileges, and reach distant code execution on qualified gadgets on processing a specially crafted web articles.
Predator, designed by a firm called Cytrox, is analogous to NSO Group’s Pegasus, enabling its shoppers to surveil targets of curiosity and harvest sensitive facts from compromised equipment. Section of a consortium of spyware sellers called the Intellexa Alliance, it was blocklisted by the U.S. governing administration in July 2023 for “enabling strategies of repression and other human rights abuses.”
The exploit, hosted on a area named sec-flare[.]com, is said to have been shipped soon after Eltantawy was redirected to a web-site named c.betly[.]me by signifies of a complex network injection attack making use of Sandvine’s PacketLogic middlebox positioned on a link involving Telecom Egypt and Vodafone Egypt.
“The body of the vacation spot site integrated two iframes, ID ‘if1’ which contained seemingly benign bait content (in this case a backlink to an APK file not that contains spyware) and ID ‘if2’ which was an invisible iframe made up of a Predator an infection url hosted on sec-flare[.]com,” the Citizen Lab mentioned.
Google TAG researcher Maddie Stone characterized it as a case of an adversary-in-the-center (AitM) attack that usually takes edge of a go to to a site working with HTTP (as opposed to HTTPS) to intercept and power the victim to go to a various site operated by the threat actor.
“In the scenario of this marketing campaign, if the target went to any ‘http’ website, the attackers injected site visitors to silently redirect them to an Intellexa website, c.betly[.]me,” Stone described. “If the user was the expected targeted consumer, the internet site would then redirect the focus on to the exploit server, sec-flare[.]com.”
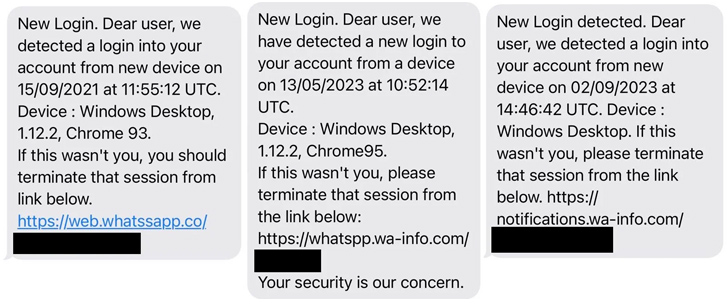
Eltantawy obtained a few SMS messages in September 2021, May well 2023, and September 2023 that masqueraded as security alerts from WhatsApp urging Eltantawy to click on a hyperlink to terminate a suspicious login session originating from a purported Windows gadget.
When these one-way links you should not match the fingerprint of the aforementioned domain, the investigation uncovered that the Predator spy ware was set up on the device somewhere around 2 minutes and 30 seconds right after Eltantawy read through the message despatched in September 2021.
Impending WEBINARAI vs. AI: Harnessing AI Defenses Towards AI-Driven Pitfalls
Completely ready to tackle new AI-driven cybersecurity difficulties? Be part of our insightful webinar with Zscaler to deal with the growing menace of generative AI in cybersecurity.
Supercharge Your Competencies
He also obtained two WhatsApp messages on June 24, 2023, and July 12, 2023, in which an specific declaring to be performing for the International Federation for Human Legal rights (FIDH) solicited his impression on an article that pointed to the website sec-flare[.]com. The messages had been still left unread.
Google TAG mentioned it also detected an exploit chain that weaponized a remote code execution flaw in the Chrome web browser (CVE-2023-4762) to produce Predator on Android devices applying two techniques: the AitM injection and through 1-time backlinks sent specifically to the concentrate on.
CVE-2023-4762, a type confusion vulnerability in the V8 engine, was anonymously documented on August 16, 2023, and patched by Google on September 5, 2023, though the internet giant assesses that Cytrox/Intellexa may have applied this vulnerability as a zero-day.
According to a brief description on the Nationwide Vulnerability Databases (NVD), CVE-2023-4762 problems a “variety confusion in V8 in Google Chrome prior to 116..5845.179 [that] authorized a remote attacker to execute arbitrary code by using a crafted HTML web site.”
The most current findings, other than highlighting the abuse of surveillance applications to concentrate on the civil modern society, underscores the blindspots in the telecom ecosystem that could be exploited to intercept network site visitors and inject malware into targets’ devices.
“Though great strides have been manufactured in modern a long time to ‘encrypt the web,’ people nonetheless often check out sites without the need of HTTPS, and a single non-HTTPS website go to can end result in spyware infection,” the Citizen Lab reported.
Customers who are at risk of spy ware threats due to the fact of “who they are or what they do” are proposed to preserve their equipment up-to-day and allow Lockdown Mode on iPhones, iPads, and Macs to stave off this kind of challenges.
Uncovered this posting appealing? Follow us on Twitter and LinkedIn to go through additional unique information we post.
Some parts of this article are sourced from:
thehackernews.com

 New Variant of Banking Trojan BBTok Targets Over 40 Latin American Banks
New Variant of Banking Trojan BBTok Targets Over 40 Latin American Banks