Cybersecurity scientists have detected a new wave of phishing attacks that aim to produce an ever-evolving details stealer referred to as StrelaStealer.
The strategies affect a lot more than 100 companies in the E.U. and the U.S., Palo Alto Networks Device 42 researchers stated in a new report printed now.
“These strategies arrive in the variety of spam email messages with attachments that at some point start the StrelaStealer’s DLL payload,” the firm stated in a report published currently.
“In an try to evade detection, attackers adjust the preliminary email attachment file structure from 1 campaign to the future, to stop detection from the earlier created signature or designs.”
Initially disclosed in November 2022, StrelaStealer is geared up to siphon email login information from effectively-acknowledged email purchasers and exfiltrate them to an attacker-managed server.
Considering the fact that then, two significant-scale strategies involving the malware have been detected in November 2023 and January 2024 focusing on substantial tech, finance, specialist and authorized, producing, federal government, energy, insurance, and design sectors in the E.U. and the U.S.

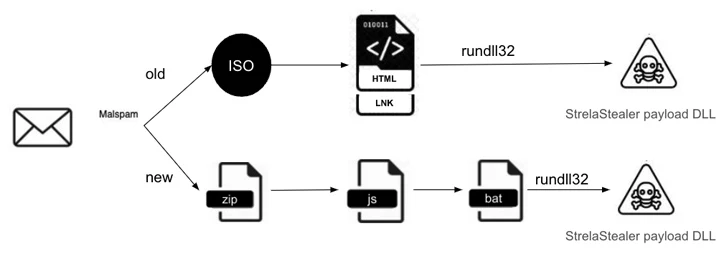
These assaults also intention to deliver a new variant of the stealer that packs in far better obfuscation and anti-examination approaches, even though staying propagated by means of invoice-themed emails bearing ZIP attachments, marking a shift from ISO data files.
Current within the ZIP archives is a JavaScript file that drops a batch file, which, in turn, launches the stealer DLL payload employing rundll32.exe, a authentic Windows element liable for working 32-little bit dynamic-connection libraries.
The stealer malware also relies on a bag of obfuscation tricks to render assessment difficult in sandboxed environments.
“With every new wave of email campaigns, menace actors update the two the email attachment, which initiates the an infection chain, and the DLL payload alone,” the researchers mentioned.
The disclosure arrives as Broadcom-owned Symantec uncovered that pretend installers for nicely identified purposes or cracked program hosted on GitHub, Mega or Dropbox are serving as a conduit for a stealer malware identified as Stealc.
Phishing campaigns have also been observed offering Revenge RAT and Remcos RAT (aka Rescoms), with the latter sent by usually means of a cryptors-as-a-services (CaaS) called AceCryptor, for every ESET.
“Throughout the second fifty percent of [2023], Rescoms became the most commonplace malware family packed by AceCryptor,” the cybersecurity firm stated, citing telemetry knowledge. “Above 50 percent of these makes an attempt occurred in Poland, adopted by Serbia, Spain, Bulgaria, and Slovakia.”
Other distinguished off-the-shelf malware packed within AceCryptor in H2 2023 include SmokeLoader, Stop ransomware, RanumBot, Vidar, RedLine, Tofsee, Fareit, Pitou, and Stealc. It really is well worth noting that numerous of these malware strains have also been disseminated by means of PrivateLoader.
Yet another social engineering rip-off noticed by Secureworks Counter Danger Device (CTU) has been uncovered to concentrate on people today trying to get details about recently deceased people on lookup engines with bogus obituary notices hosted on bogus internet websites, driving targeted visitors to the web pages by means of research motor optimization (Web optimization) poisoning in buy to ultimately drive adware and other unwelcome packages.
“Visitors to these websites are redirected to e-dating or grownup enjoyment web sites or are promptly presented with CAPTCHA prompts that set up web force notifications or popup adverts when clicked,” the organization claimed.

“The notifications screen untrue virus notify warnings from very well-identified antivirus apps like McAfee and Windows Defender, and they persist in the browser even if the target clicks a single of the buttons.”
“The buttons website link to reputable landing pages for membership-dependent antivirus computer software packages, and an affiliate ID embedded in the hyperlink rewards menace actors for new subscriptions or renewals.”
Even though the exercise is now minimal to filling fraudsters’ coffers via affiliate programs, the attack chains could be very easily repurposed to produce info stealers and other malicious plans.
The improvement also follows the discovery a new activity cluster tracked as Fluffy Wolf that’s capitalizing on phishing e-mails that contains an executable attachment to provide a cocktail of threats, this kind of as MetaStealer, Warzone RAT, XMRig miner, and a reputable remote desktop software named Remote Utilities.
The campaign is a sign that even unskilled danger actors can leverage malware-as-a-support (MaaS) techniques to carry out thriving assaults at scale and plunder sensitive data, which can then be monetized additional for profit.
“Despite the fact that mediocre in phrases of complex competencies, these risk actors obtain their ambitions by utilizing just two sets of instruments: legitimate distant access companies and cheap malware,” BI.ZONE mentioned.
Located this report interesting? Stick to us on Twitter and LinkedIn to read extra special articles we put up.
Some parts of this article are sourced from:
thehackernews.com


 AWS Patches Critical ‘FlowFixation’ Bug in Airflow Service to Prevent Session Hijacking
AWS Patches Critical ‘FlowFixation’ Bug in Airflow Service to Prevent Session Hijacking