Cybersecurity scientists have shared particulars of a now-patched security vulnerability in Amazon Web Expert services (AWS) Managed Workflows for Apache Airflow (MWAA) that could be probably exploited by a malicious actor to hijack victims’ classes and reach distant code execution on fundamental situations.
The vulnerability, now addressed by AWS, has been codenamed FlowFixation by Tenable.
“On getting in excess of the victim’s account, the attacker could have carried out responsibilities such as reading through connection strings, including configurations and triggering directed acyclic graphs (DAGS),” senior security researcher Liv Matan said in a specialized assessment.
“Under sure circumstances these types of actions can end result in RCE on the instance that underlies the MWAA, and in lateral movement to other services.”

The root lead to of the vulnerability, for each the cybersecurity agency, is a mixture of session fixation on the web management panel of AWS MWAA and an AWS area misconfiguration that effects in a cross-internet site scripting (XSS) attack.
Session fixation is a web attack strategy that occurs when a user is authenticated to a provider devoid of invalidating any current session identifiers. This permits the adversary to pressure (aka fixate) a recognised session identifier on a consumer so that, as soon as the person authenticates, the attacker has entry to the authenticated session.
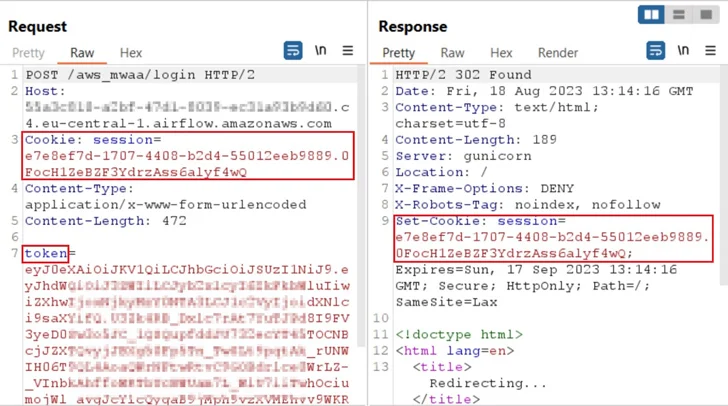
By abusing the shortcoming, a menace actor could have forced victims to use and authenticate the attacker’s acknowledged session and ultimately consider about the victim’s web administration panel.
“FlowFixation highlights a broader issue with the current point out of cloud providers’ domain architecture and administration as it relates to the Public Suffix Listing (PSL) and shared-parent domains: identical-website attacks,” Matan said, introducing the misconfiguration also impacts Microsoft Azure and Google Cloud.
Tenable also pointed out that the shared architecture – in which several shoppers have the same guardian domain – could be a goldmine for attackers looking to exploit vulnerabilities like same-web-site attacks, cross-origin issues, and cookie tossing, properly foremost to unauthorized obtain, knowledge leaks, and code execution.

The shortcoming has been addressed by both equally AWS and Azure including the misconfigured domains to PSL, therefore causing web browsers to recognize the added domains as a public suffix. Google Cloud, on the other hand, has described the issue as not “extreme sufficient” to advantage a deal with.
“In the case of identical-web site assaults, the security effects of the stated domain architecture is significant, with heightened risk of these attacks in cloud environments,” Matan defined.
“Amongst these, cookie-tossing assaults and similar-web page attribute cookie security bypass are notably regarding as each can circumvent CSRF protection. Cookie-tossing attacks can also abuse session-fixation issues.”
Observed this short article intriguing? Comply with us on Twitter and LinkedIn to read more special content we write-up.
Some parts of this article are sourced from:
thehackernews.com


 China-Linked Group Breaches Networks via Connectwise, F5 Software Flaws
China-Linked Group Breaches Networks via Connectwise, F5 Software Flaws