Vietnamese general public providers have been focused as section of an ongoing marketing campaign that deploys a novel backdoor termed SPECTRALVIPER.
“SPECTRALVIPER is a intensely obfuscated, previously undisclosed, x64 backdoor that delivers PE loading and injection, file add and down load, file and listing manipulation, and token impersonation abilities,” Elastic Security Labs said in a Friday report.
The assaults have been attributed to an actor it tracks as REF2754, which overlaps with a Vietnamese threat group identified as APT32, Canvas Cyclone (previously Bismuth), Cobalt Kitty, and OceanLotus.
Meta, in December 2020, connected the actions of the hacking crew to a cybersecurity company named CyberOne Team.

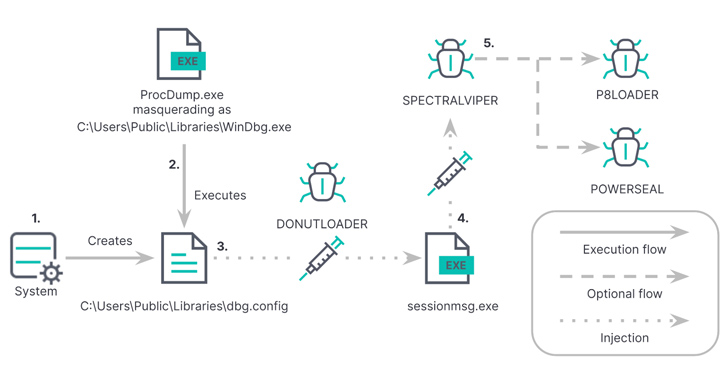
In the latest an infection circulation unearthed by Elastic, the SysInternals ProcDump utility is leveraged to load an unsigned DLL file that includes DONUTLOADER, which, in turn, is configured to load SPECTRALVIPER and other malware this kind of as P8LOADER or POWERSEAL.
SPECTRALVIPER is intended to contact an actor-controlled server and awaits more instructions when also adopting obfuscation methods like command move flattening to resist assessment.
P8LOADER, published in C++, is capable of launching arbitrary payloads from a file or from memory. Also applied is a function-created PowerShell runner named POWERSEAL that is geared up to run provided PowerShell scripts or instructions.
REF2754 is reported to share tactical commonalities with an additional team dubbed REF4322, which is recognized to generally focus on Vietnamese entities to deploy a put up-exploitation implant referred to as PHOREAL (aka Rizzo).
The connections have raised the possibility that “the two REF4322 and REF2754 action groups characterize strategies prepared and executed by a Vietnamese point out-affiliated menace.”
Future WEBINAR🔐 Mastering API Security: Understanding Your Legitimate Attack Surface area
Learn the untapped vulnerabilities in your API ecosystem and take proactive steps towards ironclad security. Be part of our insightful webinar!
Be part of the Session.wn-button,.wn-label,.wn-label:followingshow:inline-block.check_two_webinarmargin:20px 10px 30px 0background:#f9fbffcolor:#160755padding: 5%border:2px reliable #d9deffborder-radius:10pxtext-align:leftbox-shadow:10px 10px #e2ebff-webkit-border-prime-still left-radius:25px-moz-border-radius-topleft:25px-webkit-border-base-proper-radius:25px-moz-border-radius-bottomright:25px.wn-labelfont-sizing:13pxmargin:20px 0font-body weight:600letter-spacing:.6pxcolor:#596cec.wn-label:just afterwidth:50pxheight:6pxcontent:”border-prime:2px reliable #d9deffmargin: 8px.wn-titlefont-measurement:21pxpadding:10px 0font-fat:900text-align:leftline-height:33px.wn-descriptiontextual content-align:leftfont-dimensions:15.6pxline-height:26pxmargin:5px !importantcolor:#4e6a8d.wn-buttonpadding:6px 12pxborder-radius:5pxbackground-coloration:#4469f5font-measurement:15pxcolor:#fff!importantborder:0line-height:inherittext-decoration:none!importantcursor:pointermargin:15px 20pxfloat:leftfont-excess weight:500letter-spacing:.2px
The results occur as the intrusion set dubbed REF2924 has been tied to however a different piece of malware known as SOMNIRECORD that employs DNS queries to communicate with a remote server and bypass network security controls.
SOMNIRECORD, like NAPLISTENER, would make use of current open supply tasks to hone its capabilities, enabling it to retrieve details about the infected device, checklist all working procedures, deploy a web shell, and start any executable by now existing in the procedure.
“The use of open supply jobs by the attacker indicates that they are taking actions to customize current equipment for their distinct desires and might be making an attempt to counter attribution attempts,” the corporation claimed.
Observed this article attention-grabbing? Comply with us on Twitter and LinkedIn to examine much more exceptional written content we publish.
Some parts of this article are sourced from:
thehackernews.com

 New Critical MOVEit Transfer SQL Injection Vulnerabilities Discovered – Patch Now!
New Critical MOVEit Transfer SQL Injection Vulnerabilities Discovered – Patch Now!