Apple is introducing significant updates to Safari Non-public Browsing, supplying buyers superior protections against 3rd-celebration trackers as they search the web.
“Superior tracking and fingerprinting protections go even further to assistance protect against web-sites from employing the latest procedures to track or detect a user’s device,” the iPhone maker claimed.
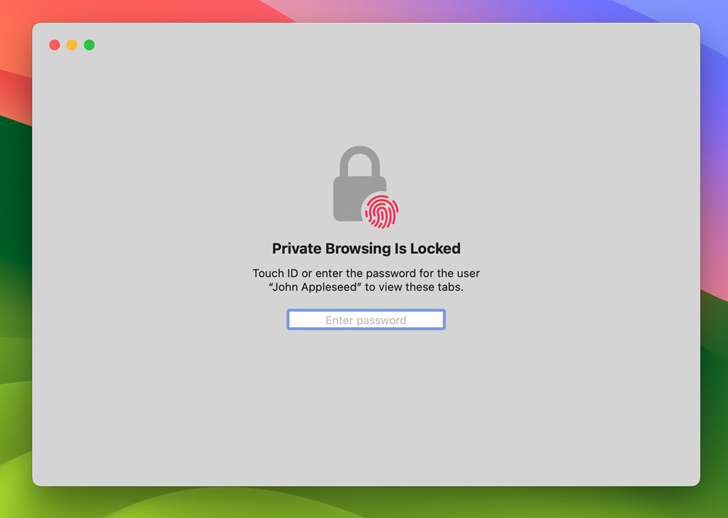
“Personal Browsing now locks when not in use, allowing a consumer to maintain tabs open even when stepping away from the gadget.”
The privateness advancements were previewed at Apple’s yearly All over the world Builders Convention (WWDC) past week. They are expected to be rolled out to buyers as component of iOS 17, iPadOS 17, and macOS Sonoma later this year.

An additional essential modify involves Website link Tracking Security in Mail, Messages, and Safari’s non-public mode to mechanically take out monitoring parameters in URLs, which are generally applied to track facts about a simply click.
“Safari has been a relatively unheralded pioneer of personal searching, and so many privateness and security features, and this 12 months it really is just a tour de drive,” Apple’s Craig Federighi was quoted as expressing to Quick Enterprise. “Searching the internet is a person of the important privateness danger vectors.”
Also coming to iOS is a new embedded Photos picker that allows customers to share unique photographs with other apps when preserving the rest of their library private.
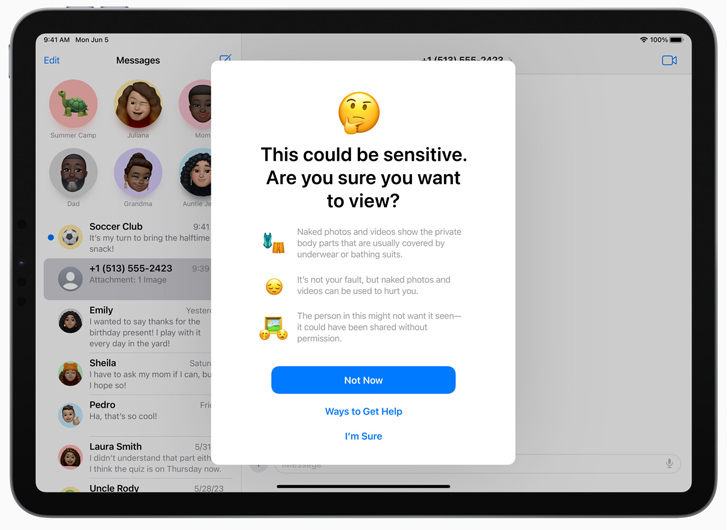
Apple is further strengthening Conversation Protection, which warns youngsters when receiving or sending explicit pictures in Messages, to encompass video clip material. On leading of that, the feature is becoming prolonged to AirDrop, FaceTime video messages, and the Pics picker.
The privateness-preserving technology that underpins Conversation Basic safety is also predicted to power Sensitive Information Warning, an optional location that will help adult users stay clear of receiving unsolicited nude visuals and videos through Messages, AirDrop, or FaceTime video clip messages.
Future WEBINAR🔐 Mastering API Security: Understanding Your Real Attack Floor
Learn the untapped vulnerabilities in your API ecosystem and get proactive techniques to ironclad security. Be a part of our insightful webinar!
Sign up for the Session.wn-button,.wn-label,.wn-label:right afterscreen:inline-block.check_two_webinarmargin:20px 10px 30px 0background:#f9fbffcolor:#160755padding: 5%border:2px good #d9deffborder-radius:10pxtext-align:leftbox-shadow:10px 10px #e2ebff-webkit-border-major-remaining-radius:25px-moz-border-radius-topleft:25px-webkit-border-base-right-radius:25px-moz-border-radius-bottomright:25px.wn-labelfont-sizing:13pxmargin:20px 0font-weight:600letter-spacing:.6pxcolor:#596cec.wn-label:immediately afterwidth:50pxheight:6pxcontent:”border-top rated:2px good #d9deffmargin: 8px.wn-titlefont-measurement:21pxpadding:10px 0font-excess weight:900text-align:leftline-top:33px.wn-descriptiontext-align:leftfont-dimensions:15.6pxline-top:26pxmargin:5px !importantcolor:#4e6a8d.wn-buttonpadding:6px 12pxborder-radius:5pxbackground-colour:#4469f5font-size:15pxcolor:#fff!importantborder:0line-top:inherittext-decoration:none!importantcursor:pointermargin:15px 20pxfloat:leftfont-excess weight:500letter-spacing:.2px
People will also be able to share a set of passwords and passkeys securely with other individuals about iCloud Keychain by generating a team. Each individual person in the group can insert and edit passwords to guarantee that they are up to date.
And finally, Apple is bringing new abilities to Lockdown Method, which includes “safer wireless connectivity defaults, media managing, media sharing defaults, sandboxing, and network security optimizations.” The increased security setting is also getting expanded to assist watchOS.
“Turning on Lockdown Mode more hardens unit defenses and strictly limitations particular functionalities, sharply lowering the attack surface for these who have to have added protections,” Apple reported.
“Lockdown Mode expands to present even extra protections for these who may well be qualified by mercenary adware simply because of who they are or what they do.”
Observed this post attention-grabbing? Adhere to us on Twitter and LinkedIn to go through more exceptional articles we article.
Some parts of this article are sourced from:
thehackernews.com


 New SPECTRALVIPER Backdoor Targeting Vietnamese Public Companies
New SPECTRALVIPER Backdoor Targeting Vietnamese Public Companies