An unnamed Southeast Asian authorities has been targeted by numerous China-nexus menace actors as component of espionage campaigns concentrating on the location above extended periods of time.
“Even though this action occurred all around the same time and in some instances even simultaneously on the same victims’ machines, every cluster is characterized by distinctive instruments, modus operandi and infrastructure,” Palo Alto Networks Unit 42 researchers Lior Rochberger, Tom Fakterman, and Robert Falcone mentioned in an exhaustive three-part report.
The attacks, which specific unique governmental entities these types of as critical infrastructure, public healthcare establishments, community economic administrators and ministries, have been attributed with reasonable confidence to a few disparate clusters tracked as Stately Taurus (aka Mustang Panda), Alloy Taurus (aka Granite Typhoon), and Gelsemium.
Mustang Panda works by using TONESHELL variant and ShadowPad
“The attackers carried out a cyberespionage operation that concentrated on gathering intelligence as nicely as stealing sensitive documents and information and facts, even though keeping a persistent and clandestine foothold,” the researchers reported, describing it as “highly-qualified and intelligence-pushed.”
The action spanned from the 2nd quarter of 2021 to the third quarter of 2023, leveraging an assortment of applications to conduct reconnaissance, steal credentials, keep access, and perform submit-compromise actions.

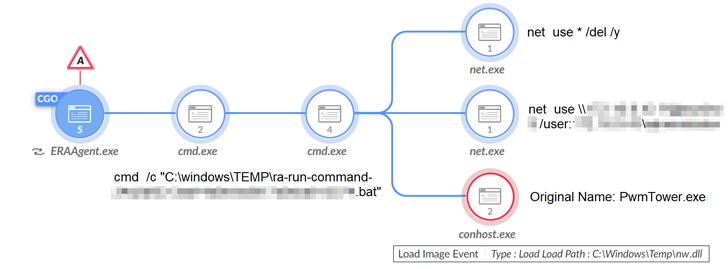
Some of the notable software program utilized to attain these targets comprise the LadonGo open up-source scanning framework, AdFind, Mimikatz, Impacket, China Chopper web shells, Cobalt Strike, ShadowPad, and a new model of the TONESHELL backdoor.
The malware eschews the use of shellcode in favor of a few DLL-dependent elements to established up persistence on the endpoint, establish command-and-management communications with a distant server, and carry out information-gathering functions, together with command execution, file process interaction, keylogging, and display capture.
“During the procedure, the threat actor slowly took command of the victims’ environments, concentrating on maintaining control for a extensive-term operation,” the researchers observed. “The intent of the threat actor’s endeavours seems to be the constant collecting and exfiltration of delicate documents and intelligence.”
Alloy Taurus Aims to Fly Less than the Radar
The intrusion established connected to Alloy Taurus is explained to have commenced in early 2022 and ongoing through 2023, leveraging uncommon strategies and bypassing security items for long-phrase persistence and reconnaissance.
These attacks, taking place in six distinctive waves, weaponize security flaws in Microsoft Trade Servers to deploy web shells, which then serves as a conduit to produce additional payloads, counting two previously unidentified .NET backdoors Zapoa and ReShell to execute arbitrary instructions remotely and harvest sensitive details.
Zapoa also incorporates capabilities to extract process facts, run shellcode, enumerate managing procedures, load a lot more .NET assembly data files to augment its capabilities, and timestamp documents and artifacts with a equipped date, a method termed timestomping.

“The menace actor guiding this cluster used a experienced tactic, using multiwave intrusions and exploiting vulnerabilities in Exchange Servers as their major penetration vector,” the researchers claimed.
In some cases, Alloy Taurus has also been observed carrying out credential theft to facilitate lateral movement by abusing the remote administration resource AnyDesk previously current in the infiltrated surroundings.
Future WEBINARAI vs. AI: Harnessing AI Defenses Towards AI-Powered Dangers
Prepared to tackle new AI-pushed cybersecurity issues? Be part of our insightful webinar with Zscaler to address the increasing menace of generative AI in cybersecurity.
Supercharge Your Abilities
Some of the other program put in by the threat actor involve Cobalt Strike, Quasar RAT, HDoor (a backdoor beforehand made use of by Chinese groups like Naikon and Goblin Panda), a Gh0st RAT variant recognized as Gh0stCringe, and Winnti, a multi-functional implant capable of granting distant management to an infected machine.
Gelsemium Singles Out Vulnerable IIS Servers
“This one of a kind cluster had exercise spanning more than six months amongst 2022-2023,” the scientists pointed out.
“It showcased a blend of uncommon tools and approaches that the risk actor leveraged to get a clandestine foothold and collect intelligence from delicate IIS servers belonging to a authorities entity in Southeast Asia.”
The attack chains capitalize on vulnerable web servers to put in web shells and distribute backdoors like OwlProxy and SessionManager, although concurrently making use of other instruments this kind of as Cobalt Strike, Meterpreter, Earthworm, and SpoolFool for put up-exploitation, tunneling command-and-regulate traffic, and privilege escalation.
OwlProxy is an HTTP proxy with backdoor operation that to start with arrived to light in April 2020. SessionManager, specific by Kaspersky last July, is a customized backdoor created to parse the Cookie industry in inbound HTTP requests to extract the commands issued by the attacker.
“The menace actor obtained obtain by way of the use of quite a few web shells, following the attempted installation of various styles of proxy malware and an IIS backdoor,” the researchers reported. “As some of the danger actor’s tries to install malware had been unsuccessful, they held delivering new instruments, displaying their skill to adapt to the mitigation system.”
Uncovered this report intriguing? Observe us on Twitter and LinkedIn to go through additional unique content we article.
Some parts of this article are sourced from:
thehackernews.com

 Deadglyph: New Advanced Backdoor with Distinctive Malware Tactics
Deadglyph: New Advanced Backdoor with Distinctive Malware Tactics