Tibetan, Uyghur, and Taiwanese people and companies are the targets of a persistent marketing campaign orchestrated by a threat actor codenamed EvilBamboo to assemble sensitive facts.
“The attacker has designed pretend Tibetan web sites, together with social media profiles, probably utilised to deploy browser-dependent exploits against specific end users,” Volexity security scientists Callum Roxan, Paul Rascagneres, and Thomas Lancaster explained in a report revealed final 7 days.
“Partly as a result of impersonating current common communities, the attacker has developed communities on on the internet platforms, these as Telegram, to assist in distribution of their malware.”
EvilBamboo, previously tracked by the cybersecurity firm under the title Evil Eye, has been joined to several attack waves considering that at least 2019, with the threat actor leveraging watering hole assaults to deliver spy ware targeting Android and iOS products. It can be also recognized as Earth Empusa and POISON CARP.

The intrusions directed in opposition to the Apple mobile functioning method leveraged a then-zero-day vulnerability in the WebKit browser motor that was patched by Apple in early 2019 to supply a spy ware pressure termed Insomnia. Meta, in March 2021, explained it detected the threat actor abusing its platforms to distribute malicious internet sites hosting the malware.
The group is also acknowledged to use Android malware these as ActionSpy and PluginPhantom to harvest important data from compromised units less than the guise of dictionary, keyboard, and prayer apps created offered on third-celebration application retailers.
The newest results from Volexity attribute to EvilBamboo three new Android espionage instruments, specifically BADBAZAAR, BADSIGNAL, and BADSOLAR, the initial of which was documented by Lookout in November 2022.
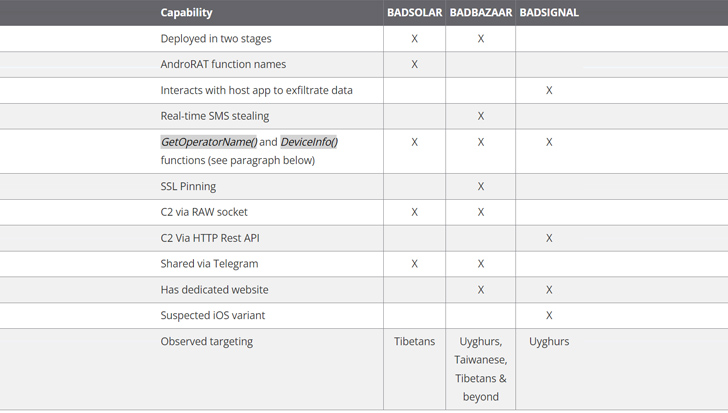
A subsequent report from ESET very last month in-depth two trojanized applications masquerading as Signal and Telegram on the Google Perform Retail outlet to entice buyers into setting up BADSIGNAL. Though the Slovak cybersecurity firm assigned the bogus to the BADBAZAAR family, citing code similarities, Volexity claimed, “they also surface to be divergent in their improvement and operation.”
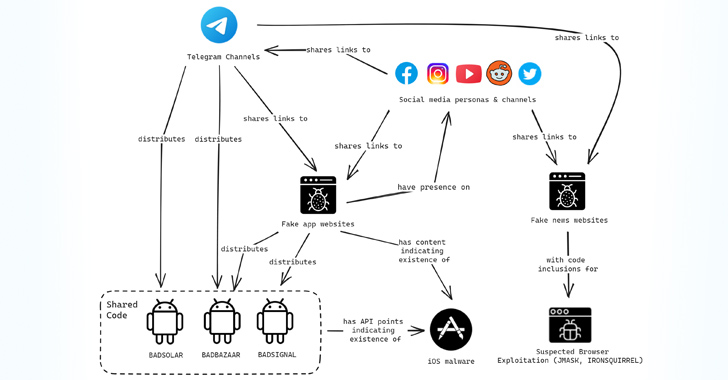
Attack chains utilised to distribute the malware households entail the use of APK sharing message boards, pretend web sites advertising and marketing Signal, Telegram, and WhatsApp, Telegram channels devoted to sharing Android applications, and a set of bogus profiles on Fb, Instagram, Reddit, X (previously Twitter), and YouTube.
“The Telegram variants apply the similar API endpoints as the Signal variants to gather information from the unit and they employ a proxy,” the scientists mentioned, incorporating it identified endpoints indicating the existence of an iOS model of BADSIGNAL.
1 of the Telegram channels is also reported to have contained a backlink to an iOS application named TibetOne that’s no longer obtainable in the Apple Application Retail outlet.
Upcoming WEBINARAI vs. AI: Harnessing AI Defenses Against AI-Powered Threats
Completely ready to tackle new AI-pushed cybersecurity problems? Be part of our insightful webinar with Zscaler to handle the escalating danger of generative AI in cybersecurity.
Supercharge Your Expertise
Messages shared by means of the Telegram teams have also been used to distribute programs backdoored with the BADSOLAR malware as perfectly as booby-trapped one-way links that, when frequented, run malicious JavaScript to profile and fingerprint the process.
Even though BADBAZAAR is mostly made use of to target Uyghur and other folks of the Muslim religion, BADSOLAR appears to be utilised primarily with applications that are Tibetan-themed. However, each strains integrate their destructive abilities in the variety of a second phase that is retrieved from a remote server.
BADSOLAR’s next-phase malware is also a fork of an open up-resource Android distant accessibility trojan referred to as AndroRAT. BADSIGNAL, in distinction, packs all of its details-collecting functions in the primary package alone.
“These strategies largely depend on users setting up backdoored applications, which highlights the two the value of only setting up apps from trusted authors and the deficiency of efficient security mechanisms to quit backdoored apps generating their way on to formal app stores,” the scientists claimed.
“EvilBamboo’s creation of pretend internet sites, and the personas tailored to the unique groups they target, has been a vital element of their operations, enabling them to establish dependable communities that provide even further avenues to concentrate on individuals with their adware or for other exploitation.”
Found this write-up appealing? Adhere to us on Twitter and LinkedIn to study far more distinctive written content we article.
Some parts of this article are sourced from:
thehackernews.com

 New Report Uncovers Three Distinct Clusters of China-Nexus Attacks on Southeast Asian Government
New Report Uncovers Three Distinct Clusters of China-Nexus Attacks on Southeast Asian Government