An emerging ransomware-as-a-assistance (RaaS) procedure known as Eldorado will come with locker variants to encrypt documents on Windows and Linux techniques.
Eldorado 1st appeared on March 16, 2024, when an ad for the affiliate method was posted on the ransomware forum RAMP, Singapore-headquartered Team-IB claimed.
The cybersecurity business, which infiltrated the ransomware group, famous that its agent is a Russian speaker and that the malware does not overlap with earlier leaked strains these kinds of as LockBit or Babuk.
“The Eldorado ransomware employs Golang for cross-platform abilities, using Chacha20 for file encryption and Rivest Shamir Adleman-Best Asymmetric Encryption Padding (RSA-OAEP) for critical encryption,” scientists Nikolay Kichatov and Sharmine Very low claimed. “It can encrypt files on shared networks making use of Server Message Block (SMB) protocol.”
The encryptor for Eldorado will come in 4 formats, particularly esxi, esxi_64, acquire, and gain_64, with its details leak site previously listing 16 victims of June 2024. Thirteen of the targets are located in the U.S., two in Italy, and just one in Croatia.
These providers span different sector verticals such as real estate, schooling, expert companies, healthcare, and production, between many others.

Further investigation of the Windows variation of artifacts has revealed the use of a PowerShell command to overwrite the locker with random bytes right before deleting the file in an try to clean up up the traces.
Eldorado is the most current in the listing of new double-extortion ransomware players that have sprung up in new moments, which include Arcus Media, AzzaSec, dan0n, Limpopo (aka SOCOTRA, FORMOSA, SEXi), LukaLocker, Shinra, and Space Bears at the time all over again highlighting the enduring and persistent character of the danger.

LukaLocker, joined to an operator dubbed Volcano Demon by Halcyon, is noteworthy for the actuality that it does not make use of a information leak web page and instead calls the target about the phone to extort and negotiate payment immediately after encrypting Windows workstations and servers.
The development coincides with the discovery of new Linux variants of Mallox (aka Fargo, TargetCompany, Mawahelper) ransomware as effectively as decryptors connected with 7 diverse builds.
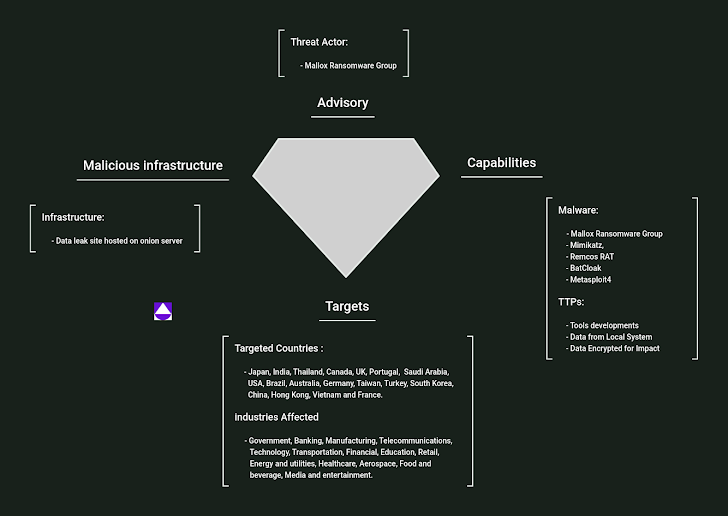
Mallox is recognised to be propagated by brute-forcing Microsoft SQL servers and phishing emails to concentrate on Windows techniques, with modern intrusions also producing use of a .NET-centered loader named PureCrypter.
“The attackers are employing custom python scripts for the reason of payload shipping and delivery and victim’s details exfiltration,” Uptycs researchers Tejaswini Sandapolla and Shilpesh Trivedi reported. “The malware encrypts person info and appends .locked extension to the encrypted files.”

A decryptor has also been made out there for DoNex and its predecessors (Muse, pretend LockBit 3., and DarkRace) by Avast by taking gain of a flaw in the cryptographic scheme. The Czech cybersecurity firm said it has been “silently supplying the decryptor” to victims due to the fact March 2024 in partnership with legislation enforcement organizations.
“Irrespective of law enforcement attempts and greater security steps, ransomware groups go on to adapt and thrive,” Group-IB said.
Information shared by Malwarebytes and NCC Team centered on victims shown on the leak web sites demonstrate that 470 ransomware attacks ended up recorded in May 2024, up from 356 in April. A vast majority of the assaults were being claimed by LockBit, Play, Medusa, Akira, 8Foundation, Qilin, RansomHub.
“The ongoing progress of new ransomware strains and the emergence of sophisticated affiliate packages demonstrate that the menace is considerably from remaining contained,” Team-IB observed. “Corporations should keep on being vigilant and proactive in their cybersecurity endeavours to mitigate the risks posed by these at any time-evolving threats.”
Identified this article fascinating? Abide by us on Twitter and LinkedIn to study far more special material we submit.
Some parts of this article are sourced from:
thehackernews.com


 5 Key Questions CISOs Must Ask Themselves About Their Cybersecurity Strategy
5 Key Questions CISOs Must Ask Themselves About Their Cybersecurity Strategy