An investigation of facts-stealing malware logs revealed on the dark web has led to the discovery of countless numbers of consumers of baby sexual abuse product (CSAM), indicating how this kind of information and facts could be utilised to combat really serious crimes.
“About 3,300 special users ended up uncovered with accounts on known CSAM resources,” Recorded Long run reported in a evidence-of-notion (PoC) report revealed previous 7 days. “A noteworthy 4.2% had qualifications for many resources, suggesting a increased probability of felony habits.”
Over the previous few yrs, off-the-shelf information-stealer variants have come to be a pervasive and ubiquitous threat focusing on several functioning techniques with an intention to siphon delicate information and facts these types of as credentials, cryptocurrency wallets, payment card information, and screenshots.

This is evidenced in the increase of new stealer malware strains this sort of as Kematian Stealer, Neptune Stealer, 0bj3ctivity, Poseidon (previously RodStealer), Satanstealer, and StrelaStealer.
Distributed by using phishing, spam campaigns, cracked computer software, pretend update web sites, Seo poisoning, and malvertising, info harvested applying these kinds of plans generally uncover their way onto the dark web in the variety of stealer logs from wherever they are procured by other cybercriminals to even further their strategies.
“Staff on a regular basis help save company qualifications on particular products or entry individual assets on organizational devices, growing the risk of infection,” Flare observed in a report final July.
“A elaborate ecosystem exists in which malware-as-a-assistance (MaaS) vendors market info-stealer malware on illicit Telegram channels, danger actors distribute it via faux cracked software program or phishing emails, and they then offer infected system logs on specialized dark web marketplaces.”
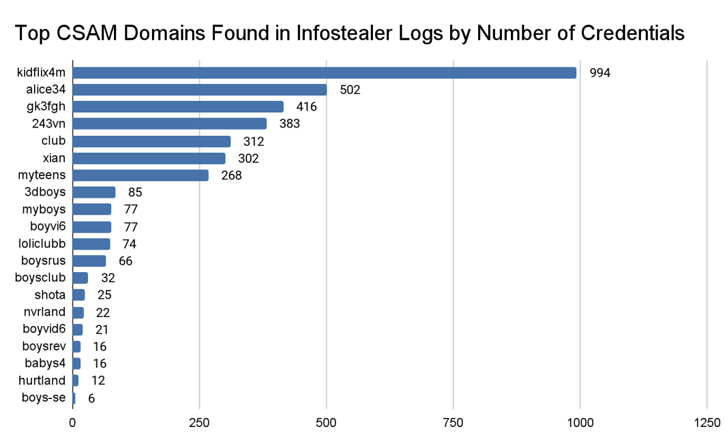
Recorded Future’s Insikt Group stated it was in a position to determine 3,324 distinctive credentials applied to entry regarded CSAM domains concerning February 2021 and February 2024, utilizing them to unmask three men and women who have been discovered to preserve accounts at no significantly less than four websites.

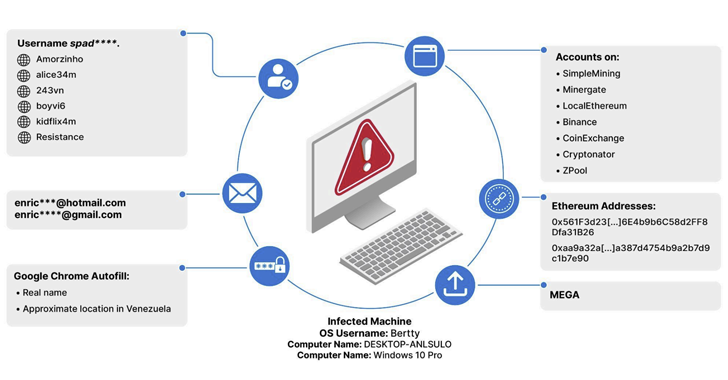
The simple fact that stealer logs also comprise cryptocurrency wallet addresses implies it could be used to decide if the addresses have been utilised to procure CSAM and other dangerous product.
Furthermore, nations around the world like Brazil, India, and the U.S. experienced the greatest counts of users with qualifications to regarded CSAM communities, whilst the company said that it could be due to an “overrepresentation owing to dataset sourcing.”
“Facts-stealer malware and stolen qualifications are projected to keep on being a cornerstone of the cybercriminal economic system thanks to the large need by risk actors looking for original accessibility to targets,” it stated, introducing it has shared its findings with law enforcement.
“Information-stealer logs can be utilised by investigators and regulation enforcement partners to monitor child exploitation on the dark web and offer perception into a portion of the dark web that is specially hard to trace.”
Uncovered this report exciting? Stick to us on Twitter and LinkedIn to go through a lot more unique content material we article.
Some parts of this article are sourced from:
thehackernews.com

 New Ransomware-as-a-Service ‘Eldorado’ Targets Windows and Linux Systems
New Ransomware-as-a-Service ‘Eldorado’ Targets Windows and Linux Systems