A new collection of 8 procedure injection approaches, collectively dubbed PoolParty, could be exploited to realize code execution in Windows devices while evading endpoint detection and response (EDR) programs.
SafeBreach researcher Alon Leviev reported the methods are “able of functioning throughout all procedures devoid of any limits, earning them extra versatile than present approach injection procedures.”
The results ended up very first offered at the Black Hat Europe 2023 meeting previous 7 days.
Future WEBINAR Cracking the Code: Discover How Cyber Attackers Exploit Human Psychology
Ever puzzled why social engineering is so helpful? Dive deep into the psychology of cyber attackers in our approaching webinar.
Join Now
Approach injection refers to an evasion approach applied to operate arbitrary code in a concentrate on process. A extensive vary of process injection procedures exists, these as dynamic hyperlink library (DLL) injection, transportable executable injection, thread execution hijacking, approach hollowing, and process doppelgänging.
PoolParty is so named mainly because it’s rooted in a ingredient known as Windows person-mode thread pool, leveraging it to insert any variety of perform merchandise into a concentrate on system on the procedure.
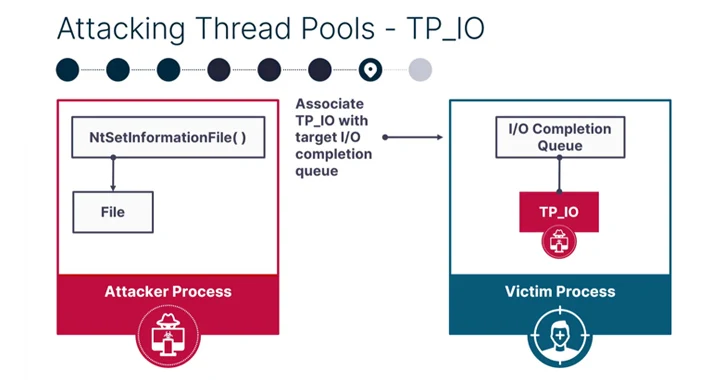
It is effective by concentrating on worker factories – which refer to Windows objects that are dependable for taking care of thread pool employee threads – and overwriting the start plan with malicious shellcode for subsequent execution by the employee threads.
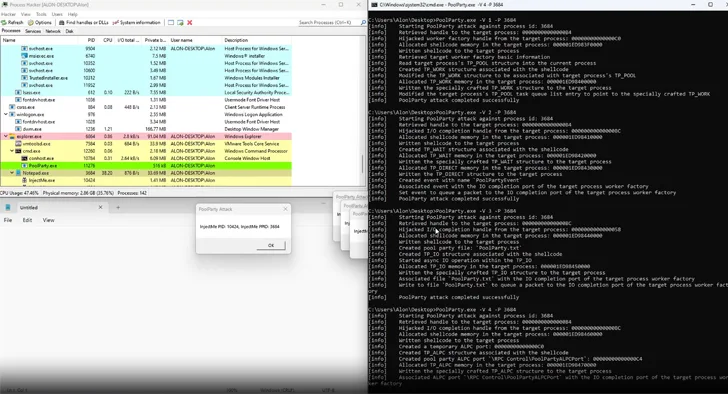
“Other than the queues, the employee manufacturing facility that serves as the worker threads manager may be used to just take in excess of the employee threads,” Leviev famous.
SafeBreach stated it was ready to devise 7 other process injection procedures employing the job queue (standard work merchandise), I/O completion queue (asynchronous work things), and the timer queue (timer perform merchandise) primarily based on the supported perform merchandise.
PoolParty has been found to realize 100% achievement rate towards common EDR options, which includes all those from CrowdStrike, Cybereason, Microsoft, Palo Alto Networks, and SentinelOne.

The disclosure arrives just about six months following Security Joes disclosed a different method injection technique dubbed Mockingjay could be exploited by menace actors to bypass security options to execute malicious code on compromised programs.
“However modern-day EDRs have developed to detect recognised method injection procedures, our investigation has established that it is continue to achievable to develop novel methods that are undetectable and have the potential to make a devastating impact,” Leviev concluded.
“Sophisticated threat actors will keep on to take a look at new and impressive strategies for method injection, and security software sellers and practitioners must be proactive in their protection towards them.”
Identified this post exciting? Observe us on Twitter and LinkedIn to examine much more exceptional information we post.
Some parts of this article are sourced from:
thehackernews.com

 SLAM Attack: New Spectre-based Vulnerability Impacts Intel, AMD, and Arm CPUs
SLAM Attack: New Spectre-based Vulnerability Impacts Intel, AMD, and Arm CPUs