Cybersecurity scientists have unearthed a Python variant of a stealer malware NodeStealer which is geared up to fully just take above Fb company accounts as perfectly as siphon cryptocurrency.
Palo Alto Network Device 42 claimed it detected the previously undocumented strain as aspect of a campaign that commenced in December 2022.
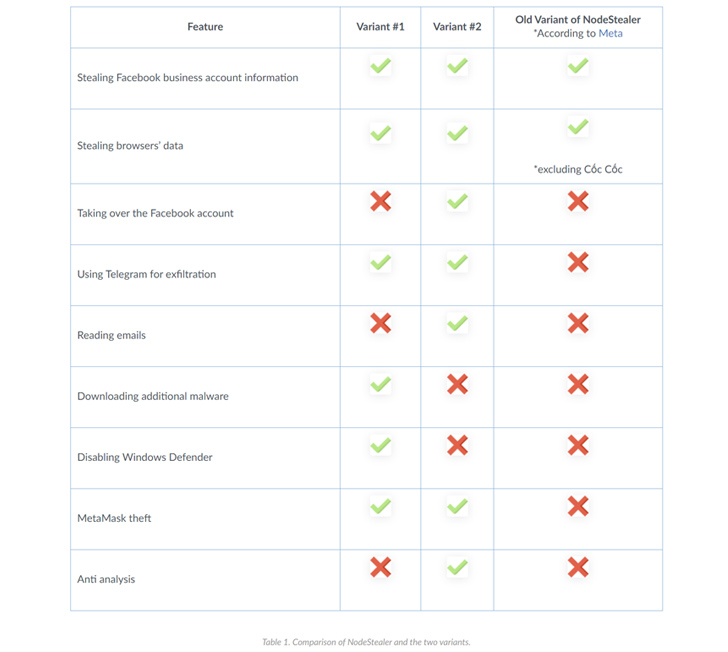
NodeStealer was first exposed by Meta in Might 2023, describing it as a stealer able of harvesting cookies and passwords from web browsers to compromise Facebook, Gmail, and Outlook accounts. Whilst the prior samples were being penned in JavaScript, the latest variations are coded in Python.
“NodeStealer poses terrific risk for equally persons and businesses,” Device 42 researcher Lior Rochberger explained. “Moreover the direct influence on Fb organization accounts, which is largely financial, the malware also steals qualifications from browsers, which can be utilised for additional assaults.”
The assaults get started with bogus messages on Fb that purportedly claim to give no cost “qualified” funds monitoring Microsoft Excel and Google Sheets templates, tricking victims to obtain a ZIP archive file hosted on Google Generate.

The ZIP file embeds in just it the stealer executable that, aside from capturing Facebook company account information and facts, is designed to download extra malware this sort of as BitRAT and XWorm in the type of ZIP data files, disable Microsoft Defender Antivirus, and have out crypto theft by applying MetaMask qualifications from Google Chrome, Cốc Cốc, and Courageous web browsers.
The downloads are accomplished by implies of a Consumer Account Manage (UAC) bypass technique that employs the fodhelper.exe to execute PowerShell scripts that retrieve the ZIP data files from a distant server.
It is worth noting that the FodHelper UAC bypass approach has also been adopted by fiscally motivated menace actors behind the Casbaneiro banking malware to receive elevated privileges in excess of infected hosts.
Device 42 explained it further noticed an upgraded Python variant of NodeStealer that goes further than credential and crypto theft by employing anti-investigation features, parsing emails from Microsoft Outlook, and even trying to take in excess of the connected Facebook account.
As soon as the important information is collected, the documents are exfiltrated via the Telegram API, immediately after which they are deleted from the machine to erase the path.

NodeStealer also joins the likes of malware like Ducktail that are element of a escalating development of Vietnamese danger actors on the lookout to crack into Facebook business enterprise accounts for marketing fraud and propagating malware to other consumers on the social media platform.
The progress arrives as danger actors have been observed leveraging WebDAV servers to deploy BATLOADER, which is then utilised to distribute XWorm as section of a multi-stage phishing attack.
“Fb business enterprise account entrepreneurs are encouraged to use sturdy passwords and allow multi-issue authentication,” Rochberger mentioned. “Take the time to present schooling for your business on phishing tactics, specially modern-day, targeted techniques that participate in off current occasions, company wants and other interesting subjects.”
Identified this post attention-grabbing? Comply with us on Twitter and LinkedIn to browse extra distinctive material we put up.
Some parts of this article are sourced from:
thehackernews.com

 European Bank Customers Targeted in SpyNote Android Trojan Campaign
European Bank Customers Targeted in SpyNote Android Trojan Campaign