Different European prospects of unique banking institutions are getting focused by an Android banking trojan called SpyNote as portion of an aggressive campaign detected in June and July 2023.
“The spyware is distributed through email phishing or smishing strategies and the fraudulent actions are executed with a blend of remote entry trojan (RAT) capabilities and vishing attack,” Italian cybersecurity organization Cleafy mentioned in a specialized evaluation introduced Monday.
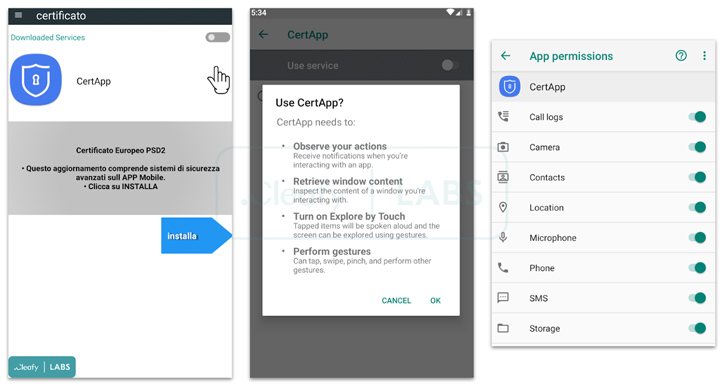
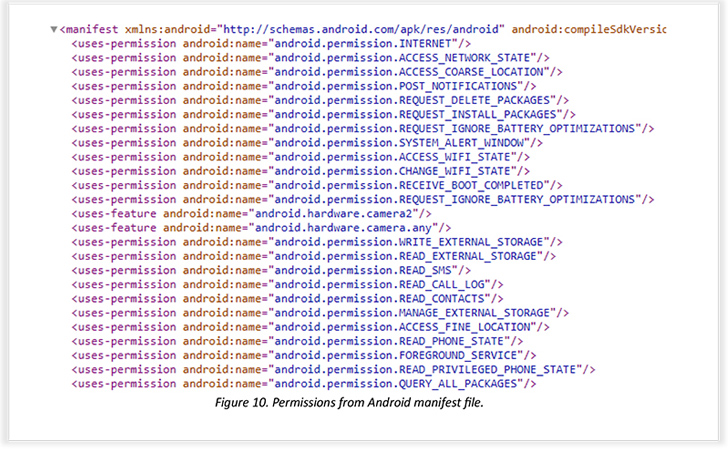
SpyNote, also called SpyMax, is identical to other Android banking Trojans in that it necessitates Android’s accessibility permissions in order to grant alone other required permissions and obtain delicate data from contaminated products. What will make the malware strain noteworthy is its twin capabilities as spy ware and complete lender fraud.

The attack chains start with a bogus SMS message urging people to put in a banking application by clicking on the accompanying link, redirecting the sufferer to the respectable TeamViewer QuickSupport app out there on the Google Engage in Retail store.
“TeamViewer has been adopted by various [threat actors] to execute fraud functions through social engineering attacks,” security researcher Francesco Iubatti reported. “In particular, the attacker phone calls the victim, impersonating financial institution operators, and performs fraudulent transactions immediately on the victim’s machine.”
The idea is to use TeamViewer as a conduit to obtain remote access to the victim’s phone, and stealthily install the malware. The different types of info harvested by SpyNote consist of geolocation knowledge, keystrokes, display recordings, and SMS messages to bypass SMS-dependent two-aspect authentication (2FA).
The disclosure arrives as the hack-for-employ procedure regarded as Bahamut has been joined to a new campaign focusing on individuals in the Center East and South Asia regions with the purpose of installing a dummy chat application named SafeChat that conceals an Android malware dubbed CoverIm.
Sent to victims by means of WhatsApp, the app homes equivalent options as that of SpyNote, requesting for accessibility permissions and other individuals to gather get in touch with logs, contacts, files, place, SMS messages, as well as set up further apps and steal details from Fb Messenger, imo, Sign, Telegram, Viber, and WhatsApp.

Cyfirma, which uncovered the hottest exercise, reported the methods employed by this threat actor overlap with yet another country-condition actor acknowledged as the DoNot Workforce, which was lately noticed employing rogue Android applications revealed to the Participate in Retail outlet to infect people located in Pakistan.
Although the correct details of the social engineering component of the attack is unclear, Bahamut is identified to depend on fictitious personas on Fb and Instagram, pretending to be tech recruiters at large tech providers, journalists, students, and activists to trick unwitting customers into downloading malware on their devices.
“Bahamut employed a range of strategies to host and distribute malware, like working a network of destructive domains purporting to offer protected chat, file-sharing, connectivity expert services, or news purposes,” Meta exposed in Could 2023. “Some of them spoofed the domains of regional media retailers, political corporations, or legit app outlets, very likely to make their inbound links look extra legitimate.”
Identified this write-up intriguing? Follow us on Twitter and LinkedIn to read a lot more special content material we submit.
Some parts of this article are sourced from:
thehackernews.com


 What is Data Security Posture Management (DSPM)?
What is Data Security Posture Management (DSPM)?