A new, monetarily enthusiastic procedure dubbed LABRAT has been noticed weaponizing a now-patched critical flaw in GitLab as portion of a cryptojacking and proxyjacking campaign.
“The attacker used undetected signature-centered instruments, refined and stealthy cross-system malware, command-and-manage (C2) resources which bypassed firewalls, and kernel-dependent rootkits to conceal their existence,” Sysdig claimed in a report shared with The Hacker News.
“Also, the attacker abused a reputable services, TryCloudflare, to obfuscate their C2 network.”
Proxyjacking will allow the attacker to hire the compromised host out to a proxy network, making it probable to monetize the unused bandwidth. Cryptojacking, on the other hand, refers to the abuse of the technique methods to mine cryptocurrency.
A notable aspect of the campaign is the use of compiled binaries published in Go and .NET to fly under the radar, with LABRAT also supplying backdoor entry to the contaminated systems. This could in the long run pave the way for follow-on attack, facts theft, and ransomware.

The attack chains start with the exploitation of CVE-2021-22205 (CVSS score: 10.), a remote code execution vulnerability that has been exploited in the wild by Indonesian-origin actors in the earlier to deploy crypto miners.
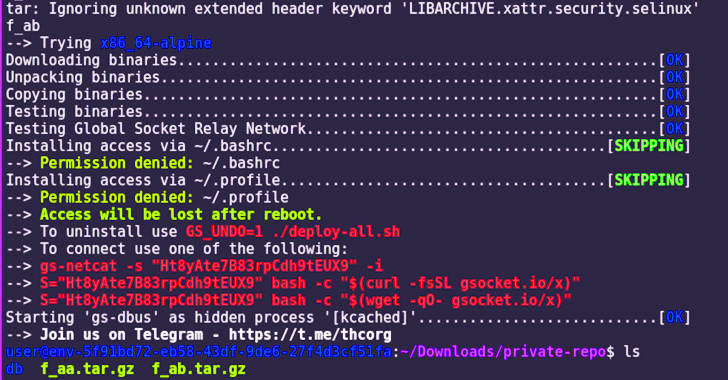
A productive split-in is followed by the retrieval of a dropper shell script from a C2 server that sets up persistence, conducts lateral motion using SSH qualifications identified in the system, and downloads added binaries from a private GitLab repository.
“During the LABRAT operation, TryCloudflare was used to redirect connections to a password-shielded web server that hosted a destructive shell script,” Miguel Hernández said. “Making use of the authentic TryCloudFlare infrastructure can make it tough for defenders to determine subdomains as malicious, particularly if it is applied in normal operations much too.”
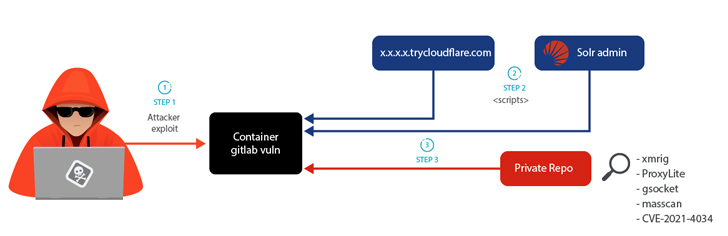
TryCloudflare is a totally free resource that can be made use of to make a Cloudflare Tunnel without having adding a web-site to Cloudflare’s DNS. It launches a system that generates a random subdomain on trycloudflare.com, thereby permitting inside means to be uncovered to the community internet.

The advancement adds to the abuse of cloudflared to set up covert conversation channels from compromised hosts and major obtain to sufferer networks.
In a second variant of the attack, the adversary is reported to have used a Solr server as an alternative of TryCloudflare to download an exploit for the PwnKit (CVE-2021-4034) from the very same GitLab repository to elevate privileges, alongside with a different file which is no lengthier available.
Some of the payloads retrieved by the dropper script contain an open-supply utility identified as World-wide Socket (gsocket) for remote access and binaries to carry out cryptojacking and proxyjacking by means of identified expert services this sort of as IPRoyal and ProxyLite. The mining approach is concealed utilizing a kernel-dependent rootkit identified as hiding-cryptominers-linux-rootkit.
Also delivered is a Go-based executable intended to be certain persistence and get rid of competing mining procedures or older versions of alone in purchase to fully harness the machine’s assets and maximize their earnings.
“Given that the purpose of the LABRAT operation is fiscal, time is revenue,” Hernández claimed. “The lengthier a compromise goes undetected, the far more money the attacker tends to make and the a lot more it will cost the victim.”
Identified this posting attention-grabbing? Follow us on Twitter and LinkedIn to read far more exclusive content material we put up.
Some parts of this article are sourced from:
thehackernews.com

 Why You Need Continuous Network Monitoring?
Why You Need Continuous Network Monitoring?