Ukrainian entities centered in Finland have been targeted as element of a destructive marketing campaign distributing a professional remote entry trojan acknowledged as Remcos RAT making use of a malware loader called IDAT Loader.
The attack has been attributed to a risk actor tracked by the Personal computer Unexpected emergency Response Workforce of Ukraine (CERT-UA) underneath the moniker UAC-0184.
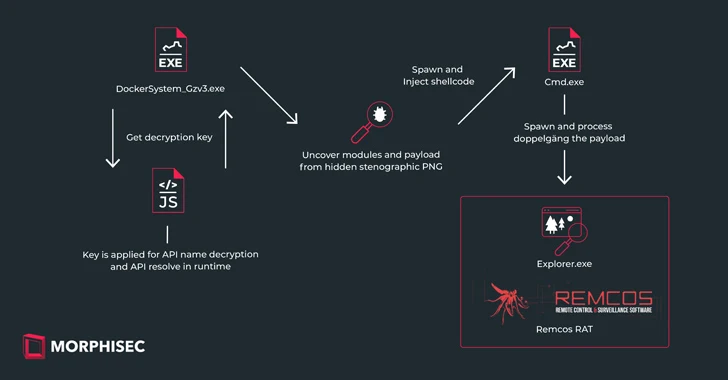
“The attack, as part of the IDAT Loader, used steganography as a method,” Morphisec researcher Michael Dereviashkin reported in a report shared with The Hacker Information. “When steganographic, or ‘Stego’ procedures are effectively-identified, it is crucial to recognize their roles in defense evasion, to greater recognize how to protect towards these kinds of ways.”

IDAT Loader, which overlaps with an additional loader family called Hijack Loader, has been utilised to provide additional payloads like DanaBot, SystemBC, and RedLine Stealer in recent months. It has also been applied by a threat actor tracked as TA544 to distribute Remcos RAT and SystemBC through phishing attacks.
The phishing marketing campaign – initially disclosed by CERT-UA in early January 2024 – entail using war-themed lures as a starting point to kick-start an infection chain that leads to the deployment of IDAT Loader, which, in convert, employs an embedded steganographic PNG to locate and extract Remcos RAT.
The development comes as CERT-UA revealed that protection forces in the state have been focused through the Sign fast messaging app to distribute a booby-trapped Microsoft Excel document that executes COOKBOX, a PowerShell-primarily based malware which is able of loading and executing cmdlets. CERT-UA has attributed the activity to a cluster dubbed UAC-0149.

It also follows the resurgence of malware campaigns propagating PikaBot malware considering that February 8, 2024, making use of an updated variant that appears to be at the moment underneath energetic advancement.
“This model of the PIKABOT loader makes use of a new unpacking technique and heavy obfuscation,” Elastic Security Labs explained. “The main module has extra a new string decryption implementation, changes to obfuscation functionality, and several other modifications.”
Discovered this short article intriguing? This posting is a contributed piece from just one of our valued companions. Comply with us on Twitter and LinkedIn to read more exclusive information we submit.
Some parts of this article are sourced from:
thehackernews.com

 8,000+ Subdomains of Trusted Brands Hijacked for Massive Spam Operation
8,000+ Subdomains of Trusted Brands Hijacked for Massive Spam Operation