Additional than 8,000 subdomains belonging to reputable models and establishments have been hijacked as component of a subtle distribution architecture for spam proliferation and simply click monetization.
Guardio Labs is monitoring the coordinated destructive exercise, which has been ongoing considering that at the very least September 2022, underneath the identify SubdoMailing. The e-mail selection from “counterfeit package deal delivery alerts to outright phishing for account qualifications.”
The Israeli security enterprise attributed the marketing campaign to a threat actor it calls ResurrecAds, which is recognised to resuscitate lifeless domains of or affiliated with large brand names with the stop of manipulating the digital promoting ecosystem for nefarious gains.
“‘ResurrecAds’ manages an in depth infrastructure encompassing a large array of hosts, SMTP servers, IP addresses, and even non-public household ISP connections, alongside quite a few more owned area names,” security scientists Nati Tal and Oleg Zaytsev said in a report shared with The Hacker Information.
In distinct, the marketing campaign “leverages the belief affiliated with these domains to circulate spam and malicious phishing emails by the thousands and thousands each working day, cunningly working with their credibility and stolen methods to slip previous security measures.”
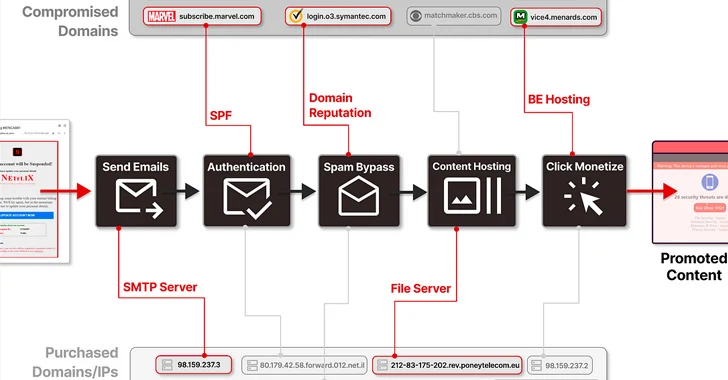
These subdomains belong to or are affiliated with large brands and organizations these types of as ACLU, eBay, Lacoste, Marvel, McAfee, MSN, Pearson, PwC, Symantec, The Economist, UNICEF, and VMware among some others.
The marketing campaign is notable for its capacity to bypass typical security blocks, with the complete human body conceived as an graphic to evade textual content-dependent spam filters, clicking which initiates a sequence of redirections by distinct domains.

“These redirects test your system style and geographic place, primary to material personalized to improve revenue,” the scientists spelled out.
“This could be anything at all from an frustrating advertisement or affiliate backlink to far more deceptive practices like quiz cons, phishing web-sites, or even a malware obtain aimed at swindling you out of your revenue far more immediately.”

An additional very important aspect of these email messages is that they are also able of circumventing Sender Coverage Framework (SPF), an email authentication technique which is created to prevent spoofing by making certain a mail server is authorized to deliver email for a given area.
It’s not just SPF, as the emails also go DomainKeys Determined Mail (DKIM) and Area-based Message Authentication, Reporting and Conformance (DMARC) checks that help stop messages from currently being marked as spam.
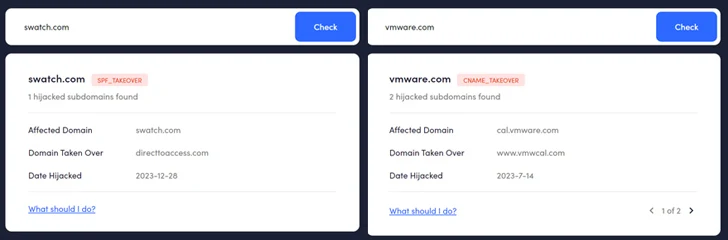
In one particular instance of a deceptive cloud storage warning email highlighted by Guardio, the concept originated from an SMTP server in Kyiv, nonetheless was flagged as getting despatched from [email protected].
A nearer assessment of the DNS file for marthastewart.msn.com discovered that the subdomain is joined to another area (msnmarthastewartsweeps[.]com) with that CNAME file, an aliasing procedure that has been earlier weaponized by advertising and marketing technology corporations to get all-around third-bash cookie blocking.
“This signifies that the subdomain inherits the complete actions of msnmarthastewartsweeps[.]com , which includes its SPF plan,” the researchers mentioned. “In this case, the actor can ship email messages to any person they wish as if msn[.]com and their authorized mailers sent those people e-mail!”

It can be worthy of pointing out right here that each the domains have been legit and briefly lively at some place in 2001, just before they had been remaining in an abandoned state for 21 many years. It wasn’t right up until September 2022 when msnmarthastewartsweeps[.]com was privately registered with Namecheap.
In other the hijacking scheme entails the threat actors frequently scanning for prolonged-forgotten subdomains with dangling CNAME records of abandoned domains and then registering them to choose regulate of them.

CNAME-takeover can also have serious repercussions when these reputed subdomains are seized to host bogus phishing landing web pages developed to harvest users’ qualifications. That said, there is no proof that any of the hijacked subdomains have been applied for this intent.
Guardio stated it also uncovered situations the place the DNS SPF history of a identified domain holds deserted domains related with defunct email- or marketing-connected services, thus making it possible for attackers to get possession of these types of domains, inject their own IP addresses into the file, and in the long run mail e-mails on behalf of the main domain name.
In an exertion to counter the menace and dismantle the infrastructure, Guardio has built out there a SubdoMailing Checker, a web page that enables domain administrators and web site entrepreneurs to appear for symptoms of compromise.
“This procedure is meticulously made to misuse these assets for distributing numerous malevolent ‘Advertisements,’ aiming to produce as numerous clicks as possible for these ‘ad network’ purchasers,” the scientists explained.
“Armed with a wide selection of compromised reputable domains, servers, and IP addresses, this advertisement network deftly navigates by way of the destructive email propagation approach, seamlessly switching and hopping among the its belongings at will.”
Observed this post interesting? Abide by us on Twitter and LinkedIn to go through much more exclusive information we submit.
Some parts of this article are sourced from:
thehackernews.com

 North Korean Hackers Targeting Developers with Malicious npm Packages
North Korean Hackers Targeting Developers with Malicious npm Packages