The China-linked threat actor recognized as Sharp Panda has expanded their focusing on to incorporate governmental corporations in Africa and the Caribbean as aspect of an ongoing cyber espionage marketing campaign.
“The marketing campaign adopts Cobalt Strike Beacon as the payload, enabling backdoor functionalities like C2 communication and command execution although reducing the exposure of their custom made equipment,” Test Place reported in a report shared with The Hacker Information. “This refined tactic implies a deeper comprehension of their targets.”
The Israeli cybersecurity business is tracking the activity under a new name Sharp Dragon, describing the adversary as watchful in its concentrating on, although at the exact same time broadening its reconnaissance initiatives.
The adversary 1st arrived to gentle in June 2021, when it was detected targeting a Southeast Asian governing administration to deploy a backdoor on Windows techniques dubbed VictoryDLL.
Subsequent attacks mounted by Sharp Dragon have established their sights on superior-profile government entities in Southeast Asia to deliver the Soul modular malware framework, which is then applied to obtain further components from an actor-controlled server to aid info gathering.

Evidence indicates the Soul backdoor has been in the will work considering the fact that October 2017, adopting options from Gh0st RAT – malware frequently connected with a diverse range of Chinese threat actors – and other publicly offered resources.
A different established of attacks attributed to the menace actors has qualified large-level govt officers from G20 nations as not long ago as June 2023, indicating continued concentration on governmental bodies for information gathering.
Critical to Sharp Panda’s functions is the exploitation of 1-day security flaws (e.g., CVE-2023-0669) to infiltrate infrastructure for later on use as command-and-handle (C2) servers. Yet another noteworthy factor is the use of the legit adversary simulation framework Cobalt Strike above custom backdoors.
What’s a lot more, the hottest set of assaults aimed at governments in Africa and the Caribbean exhibit an enlargement of their authentic attack plans, with the modus operandi involving using compromised higher-profile email accounts in Southeast Asia to send out phishing email messages to infect new targets in the two regions.
These messages bear destructive attachments that leverage the Royal Highway Prosperous Textual content Format (RTF) weaponizer to fall a downloader named 5.t that’s liable for conducting reconnaissance and launching Cobalt Strike, letting the attackers to obtain info about the focus on environment.
The use of Cobalt Strike as a backdoor not only minimizes the exposure of personalized resources but also implies a “refined solution to concentrate on assessment,” Verify Level additional.
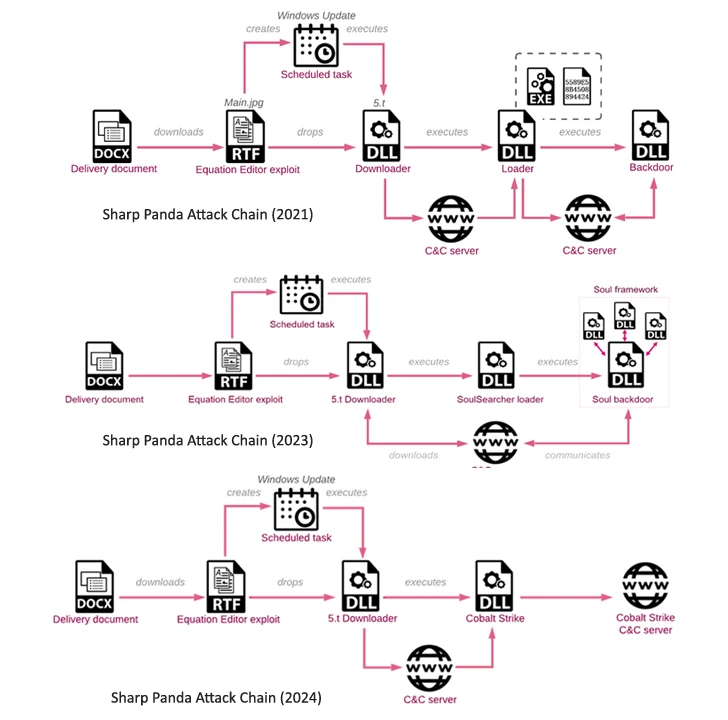
In a sign that the threat actor is constantly refining its practices, the latest attack sequences have been noticed utilizing executables disguised as files to kick-off the an infection, as opposed to relying on a Word document using a remote template to download an RTF file weaponized with Royal Street.
“Sharp Dragon’s strategic expansion in direction of Africa and the Caribbean signifies a broader effort by Chinese cyber actors to boost their presence and affect in these locations.”
The results arrive the same working day Palo Alto Networks uncovered facts of a marketing campaign codenamed Operation Diplomatic Specter that has been focusing on diplomatic missions and governments in the Middle East, Africa, and Asia due to the fact at least late 2022. The attacks have been linked to a Chinese menace actor dubbed TGR-STA-0043 (previously CL-STA-0043).
The change in Sharp Dragon’s functions towards Africa is portion of larger initiatives produced by China to extend its impact throughout the continent.

“These attacks conspicuously align with China’s broader soft electricity and technological agenda in the region, focusing on critical areas these as the telecommunication sector, economic establishments, and governmental bodies,” SentinelOne security researcher Tom Hegel earlier pointed out in September 2023.
The enhancement also follows a report from Google-owned Mandiant that highlighted China’s use of proxy networks referred to as operational relay box networks (ORBs) to obscure their origins when carrying out espionage operations and accomplish increased achievement charges in attaining and protecting accessibility to substantial-value networks.
“Making networks of compromised products enables ORB network directors to effortlessly mature the size of their ORB network with very little effort and produce a frequently evolving mesh network that can be employed to conceal espionage functions,” Mandiant researcher Michael Raggi reported.
One this sort of network ORB3 (aka SPACEHOP) is stated to have been leveraged by numerous China-nexus threat actors, including APT5 and APT15, while a further network named FLORAHOX – which contains products recruited by the router implant FLOWERWATER – has been put to use by APT31.
“Use of ORB networks to proxy traffic in a compromised network is not a new tactic, nor is it special to China-nexus cyber espionage actors,” Raggi stated. “We have tracked China-nexus cyber espionage using these tactics as portion of a broader evolution toward additional purposeful, stealthy, and productive functions.”
Discovered this short article fascinating? Follow us on Twitter and LinkedIn to browse much more unique articles we submit.
Some parts of this article are sourced from:
thehackernews.com


 Inside Operation Diplomatic Specter: Chinese APT Group’s Stealthy Tactics Exposed
Inside Operation Diplomatic Specter: Chinese APT Group’s Stealthy Tactics Exposed