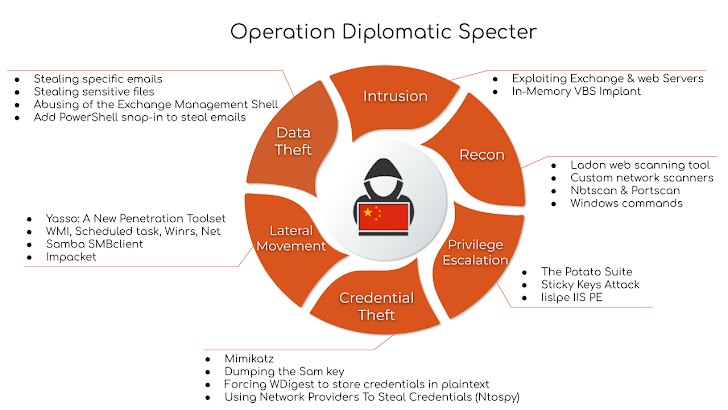
Governmental entities in the Middle East, Africa, and Asia are the goal of a Chinese sophisticated persistent threat (APT) team as element of an ongoing cyber espionage campaign dubbed Operation Diplomatic Specter considering that at minimum late 2022.
“An evaluation of this threat actor’s exercise reveals extensive-phrase espionage operations versus at minimum seven governmental entities,” Palo Alto Networks Unit 42 researchers Lior Rochberger and Daniel Frank said in a report shared with The Hacker News.
“The menace actor executed intelligence assortment initiatives at a large scale, leveraging exceptional email exfiltration tactics from compromised servers.”
The cybersecurity firm, which formerly tracked the action cluster underneath the identify CL-STA-0043, claimed it truly is graduating it to a non permanent actor team codenamed TGR-STA-0043 owing to its assessment that the intrusion set is the get the job done of a one actor functioning on behalf of Chinese state-aligned pursuits.
Targets of the attacks include things like diplomatic and economic missions, embassies, military operations, political conferences, ministries of targeted countries, and large-position officers.

CL-STA-0043 was to start with documented in June 2023 as focusing on authorities companies in the Middle East and Africa utilizing rare credential theft and Trade email exfiltration tactics.
A subsequent investigation from Device 42 in the direction of the finish of last calendar year uncovered overlaps concerning CL-STA-0043 and CL-STA-0002 arising from the use of a program termed Ntospy (aka NPPSpy) for credential theft functions.
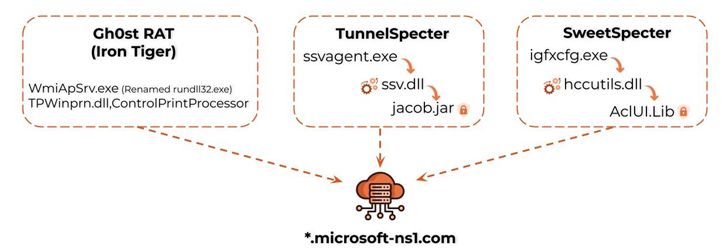
Attack chains orchestrated by the group have associated a set of beforehand undocumented backdoors these types of as TunnelSpecter and SweetSpecter, which are the two variants of the infamous Gh0st RAT, a resource used profusely in espionage campaigns orchestrated by Beijing authorities hackers.
TunnelSpecter receives its title from the use of DNS tunneling for data exfiltration, offering it an extra layer of stealth. SweetSpecter, on the other hand, is so named for its similarities to SugarGh0st RAT, a different custom variant of Gh0st RAT that has been put to use by a suspected Chinese-speaking threat actor considering the fact that August 2023.
Each the backdoors enable the adversary to manage stealthy accessibility to their targets networks, together with the capability to execute arbitrary commands, exfiltrate details, and deploy further more malware and equipment on the infected hosts.
“The danger actor appears to closely watch modern geopolitical developments, making an attempt to exfiltrate facts day by day,” the researchers mentioned.
This is realized via targeted endeavours to infiltrate targets’ mail servers and to look for them for information and facts of curiosity, in some conditions continuously attempting to regain entry when the attackers’ routines were being detected and disrupted. Initial accessibility is achieved by the exploitation of recognised Trade server flaws these kinds of as ProxyLogon and ProxyShell.

“The risk actor searched for certain key phrases and exfiltrated anything at all they could obtain associated to them, these types of as full archived inboxes belonging to particular diplomatic missions or people today,” the researchers pointed out. “The risk actor also exfiltrated information related to topics they were looking for.”
The Chinese links to Operation Diplomatic Specter even further stem from the use of operational infrastructure solely employed by China-nexus groups like APT27, Mustang Panda, and Winnti, not to mention equipment like the China Chopper web shell and PlugX.
“The exfiltration techniques observed as part of Procedure Diplomatic Specter supply a distinct window into the attainable strategic goals of the threat actor powering the assaults,” the researchers concluded.
“The menace actor searched for highly sensitive information and facts, encompassing facts about navy operations, diplomatic missions and embassies and foreign affairs ministries.”
Identified this posting appealing? Adhere to us on Twitter and LinkedIn to go through much more unique information we article.
Some parts of this article are sourced from:
thehackernews.com


 Ivanti Patches Critical Remote Code Execution Flaws in Endpoint Manager
Ivanti Patches Critical Remote Code Execution Flaws in Endpoint Manager