Internet-struggling with Linux units and Internet of Things (IoT) products are currently being targeted as element of a new marketing campaign intended to illicitly mine cryptocurrency.
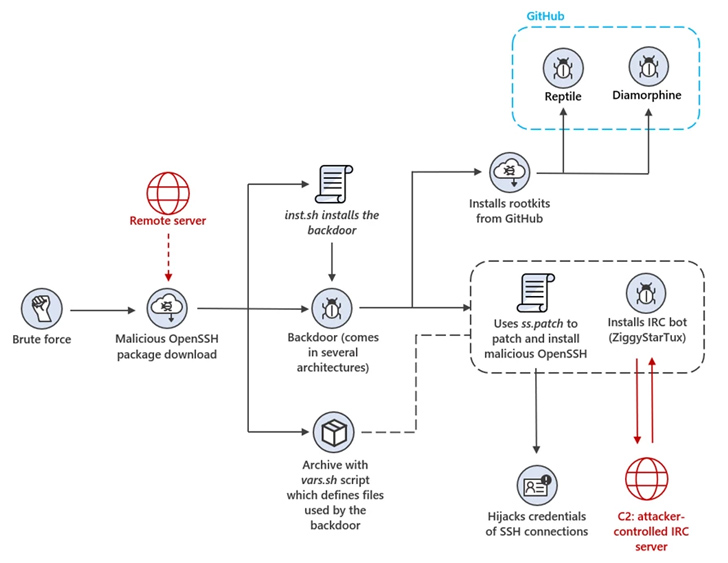
“The risk actors behind the attack use a backdoor that deploys a broad array of resources and factors such as rootkits and an IRC bot to steal unit methods for mining operations,” Microsoft threat intelligence researcher Rotem Sde-Or stated.
“The backdoor also installs a patched version of OpenSSH on impacted gadgets, allowing for danger actors to hijack SSH qualifications, move laterally in just the network, and conceal destructive SSH connections.”
To pull off the plan, misconfigured Linux hosts are brute-compelled to obtain initial obtain, adhering to which the danger actors shift to disable shell historical past and fetch a trojanized version of OpenSSH from a remote server.
The rogue OpenSSH package is configured to put in and start the backdoor, a shell script that makes it possible for the attackers to distribute extra payloads and carry out other publish-exploitation actions.

This contains exfiltrating information and facts about the product, installing open-resource rootkits called Diamorphine and Reptile from GitHub, and getting techniques to obscure its action by clearing logs that could alert its presence.
“To assure persistent SSH entry to the unit, the backdoor appends two public keys to the approved_keys configuration information of all people on the method,” the Windows maker mentioned.
The implant also seeks to monopolize the infected system’s means by reducing competing crypto mining processes that might be now running on it prior to launching its miner.
Moreover, it runs a modified version of ZiggyStarTux, an IRC-dependent distributed denial-of-company (DDoS) shopper which is capable of executing bash instructions issued from the command-and-control (C2) server. It really is centered on one more botnet malware termed Kaiten (aka Tsunami).
The assaults, the tech giant mentioned, leverage an unnamed Southeast Asian economical institution’s subdomain for C2 communications in an endeavor to disguise the destructive targeted visitors.
It is truly worth pointing out that the modus operandi detailed by Microsoft overlaps with a current report from the AhnLab Security Unexpected emergency Response Centre (ASEC), which in-depth attacks focusing on exposed Linux servers with crypto mining malware and a Tsunami botnet variant dubbed Ziggy.
The procedure has been traced back again to an actor named asterzeu, who has made available the toolkit for sale on the malware-as-a-support sector. “The complexity and scope of this attack are indicative of the initiatives attackers make to evade detection,” Sde-Or mentioned.
The progress comes as many known security flaws in routers, electronic video clip recorders, and other network program are currently being actively exploited by risk actors to deploy the Mirai botnet malware, according to Akamai and Palo Alto Networks Unit 42.
“The Mirai botnet, identified again in 2016, is however energetic today,” Uni 42 scientists explained. “A considerable part of the rationale for its attractiveness among danger actors lies in the security flaws of IoT products.”
“These distant code execution vulnerabilities concentrating on IoT units exhibit a blend of reduced complexity and large impact, building them an irresistible target for risk actors.”
Observed this report appealing? Adhere to us on Twitter and LinkedIn to read through a lot more special material we put up.
Some parts of this article are sourced from:
thehackernews.com


 MULTI#STORM Campaign Targets India and U.S. with Remote Access Trojans
MULTI#STORM Campaign Targets India and U.S. with Remote Access Trojans