Cybersecurity researchers have documented a novel article-exploit persistence approach on iOS 16 that could be abused to fly beneath the radar and most important entry to an Apple unit even when the sufferer thinks it is offline.
The technique “tricks the target into thinking their device’s Plane Manner works when in truth the attacker (following successful system exploit) has planted an synthetic Airplane Mode which edits the UI to screen Airplane Manner icon and cuts internet link to all applications besides the attacker application,” Jamf Threat Labs researchers Hu Ke and Nir Avraham mentioned in a report shared with The Hacker Information.
Plane Mode, as the identify implies, will allow end users to convert off wi-fi functions in their devices, effectively stopping them from connecting to Wi-Fi networks, cellular knowledge, and Bluetooth as very well as sending or getting phone calls and text messages.

The solution devised by Jamf, in a nutshell, provides an illusion to the person that the Airplane Manner is on when enabling a malicious actor to stealthily maintain a mobile network connection for a rogue software.
“When the user turns on Plane Mode, the network interface pdp_ip0 (cellular knowledge) will no lengthier display ipv4/ipv6 ip addresses,” the scientists described. “The cellular network is disconnected and unusable, at minimum to the person space level.”
Although the underlying alterations are carried out by CommCenter, the consumer interface (UI) modifications, this sort of as the icon transitions are taken care of by the SpringBoard.
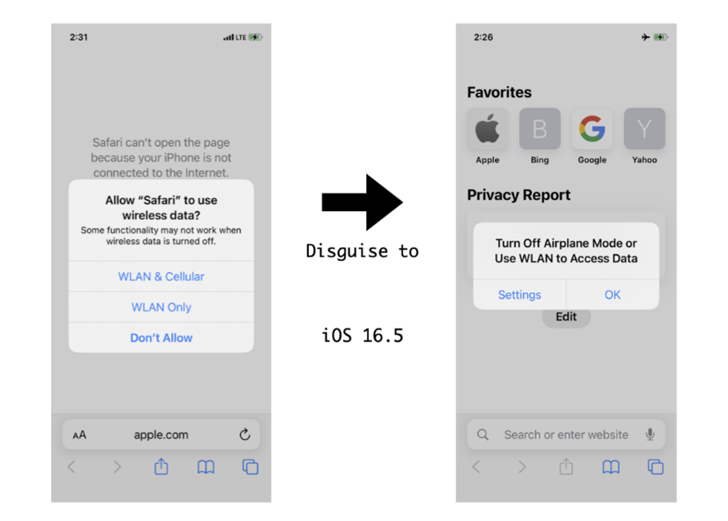
The intention of the attack, then, is to devise an artificial Airplane Mode that keeps the UI alterations intact but retains mobile connectivity for a destructive payload mounted on the unit by other signifies.
“After enabling Airplane Manner with out a Wi-Fi relationship, end users would assume that opening Safari would result in no link to the internet,” the scientists said. “The regular expertise is a notification window that prompts a person to ‘Turn Off Plane Mode.'”

To pull off the ruse, the CommCenter daemon is used to block cellular info entry for distinct apps and disguise it as Airplane Manner by signifies of a hooked perform that alters the warn window to appear like the environment has been turned on.
It really is truly worth noting that the functioning process kernel notifies the CommCenter through a callback plan, which, in flip, notifies the SpringBoard to screen the pop-up.
A closer evaluation of the CommCenter daemon has also uncovered the existence of an SQL databases that’s utilised to document the mobile facts entry standing of every app (aka bundle ID), with a flag established to the worth “8” if an application is blocked from accessing it.
“Applying this databases of put in application bundle IDs we can now selectively block or let an app to accessibility Wi-Fi or cellular information employing the following code,” the researchers mentioned.
“When put together with the other strategies outlined earlier mentioned, the fake Plane Manner now seems to act just as the real one, besides that the internet ban does not use to non-application procedures these types of as a backdoor trojan.”
Identified this report attention-grabbing? Observe us on Twitter and LinkedIn to examine additional distinctive content material we publish.
Some parts of this article are sourced from:
thehackernews.com


 Why You Need Continuous Network Monitoring?
Why You Need Continuous Network Monitoring?