The distributed denial-of-provider (DDoS) botnet acknowledged as Muhstik has been observed leveraging a now-patched security flaw impacting Apache RocketMQ to co-decide vulnerable servers and extend its scale.
“Muhstik is a perfectly-known menace focusing on IoT units and Linux-centered servers, infamous for its ability to infect gadgets and make use of them for cryptocurrency mining and launching Distributed Denial of Assistance (DDoS) attacks,” Cloud security company Aqua reported in a report published this 7 days.
Very first documented in 2018, attack campaigns involving the malware have a background of exploiting identified security flaws, specially individuals relating to web apps, for propagation.
The hottest addition to the record of exploited vulnerabilities is CVE-2023-33246 (CVSS score: 9.8), a critical security flaw impacting Apache RocketMQ that will allow a remote and unauthenticated attacker to complete distant code execution by forging the RocketMQ protocol written content or making use of the update configuration operate.

When the shortcoming is effectively abused to obtain preliminary access, the threat actor proceeds to execute a shell script hosted on a distant IP deal with, which is then liable for retrieving the Muhstik binary (“pty3”) from another server.
“After gaining the ability to upload the malicious payload by exploiting the RocketMQ vulnerability, the attacker is equipped to execute their destructive code, which downloads the Muhstik malware,” security researcher Nitzan Yaakov reported.
Persistence on the host is accomplished by usually means of copying the malware binary to a number of directories and editing the /etc/inittab file — which controls what processes to start during the booting of a Linux server — to mechanically restart the system.
What’s additional, the naming of the binary as “pty3” is likely an try to masquerade as a pseudoterminal (“pty”) and evade detection. One more evasion method is that the malware is copied to directories these kinds of as /dev/shm, /var/tmp, /run/lock, and /operate for the duration of the persistence period, which allows it to be executed specifically from memory and stay clear of leaving traces on the technique.
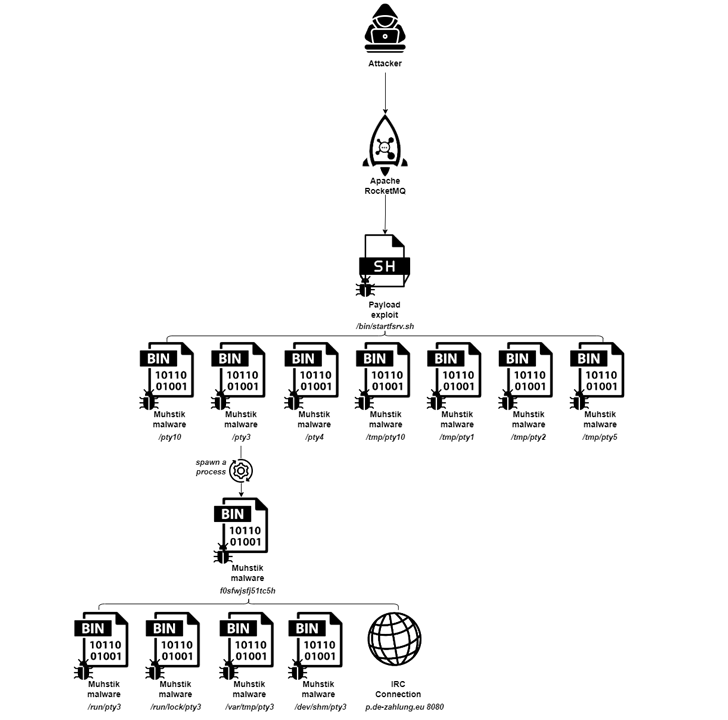
Muhstik will come outfitted with features to obtain program metadata, laterally go to other gadgets about a protected shell (SSH), and in the long run create call with a command-and-management (C2) area to get further more guidance utilizing the Internet Relay Chat (IRC) protocol.
The stop aim of the malware is to weaponize the compromised devices to complete different styles of flooding assaults in opposition to targets of curiosity, effectively overwhelming their network sources and triggering a denial-of-services affliction.
With 5,216 vulnerable cases of Apache RocketMQ nonetheless exposed to the internet following much more than a calendar year of general public disclosure of the flaw, it can be essential that corporations acquire actions to update to the most up-to-date edition in get to mitigate prospective threats.

“Furthermore, in previous strategies, cryptomining exercise was detected following the execution of the Muhstik malware,” Yaakov explained. “These aims go hand in hand, as the attackers strive to distribute and infect more machines, which will help them in their mission to mine much more cryptocurrency using the electrical power of the compromised devices.”
The disclosure arrives as the AhnLab Security Intelligence Middle (ASEC) unveiled that improperly secured MS-SQL servers are getting qualified by threat actors to a variety of types of malware, ranging from ransomware and distant accessibility trojans to Proxyware.
“Directors need to use passwords that are tricky to guess for their accounts and transform them periodically to secure the databases server from brute-pressure attacks and dictionary assaults,” ASEC claimed. “They have to also implement the most recent patches to prevent vulnerability assaults.”
Located this posting appealing? Observe us on Twitter and LinkedIn to read through more exclusive material we submit.
Some parts of this article are sourced from:
thehackernews.com


 Third-Party Cyber Attacks: The Threat No One Sees Coming – Here’s How to Stop Them
Third-Party Cyber Attacks: The Threat No One Sees Coming – Here’s How to Stop Them