The menace actor known as Commando Cat has been connected to an ongoing cryptojacking attack marketing campaign that leverages improperly secured Docker scenarios to deploy cryptocurrency miners for money attain.
“The attackers made use of the cmd.cat/chattr docker graphic container that retrieves the payload from their very own command-and-handle (C&C) infrastructure,” Craze Micro scientists Sunil Bharti and Shubham Singh mentioned in a Thursday investigation.
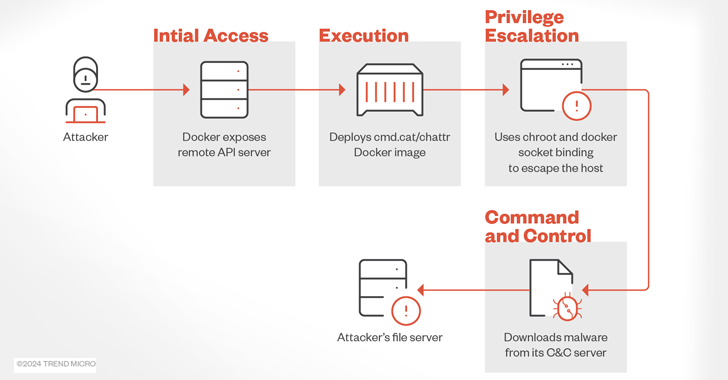
Commando Cat, so named for its use of the open-resource Commando challenge to produce a benign container, was 1st documented before this year by Cado Security.

The attacks are characterized by the concentrating on of misconfigured Docker remote API servers to deploy a Docker graphic named cmd.cat/chattr, which is then utilized as a foundation to instantiate a container and break out of its confines applying the chroot command, and achieve entry to the host functioning technique.
The final action entails retrieving the malicious miner binary using a curl or wget command from a C&C server (“leetdbs.anondns[.]net/z”) by means of a shell script. The binary is suspected to be ZiggyStarTux, an open-source IRC bot dependent on the Kaiten (aka Tsunami) malware.
“The importance of this attack campaign lies in its use of Docker photos to deploy cryptojacking scripts on compromised devices,” the scientists claimed. “This tactic allows attackers to exploit vulnerabilities in Docker configurations even though evading detection by security software package.”
The disclosure will come as Akamai revealed that decades-previous security flaws in ThinkPHP programs (e.g., CVE-2018-20062 and CVE-2019-9082) are becoming exploited by a suspected Chinese-talking risk actor to supply a web shell dubbed Dama as section of a campaign that has been underway considering that October 17, 2023.

“The exploit makes an attempt to retrieve more obfuscated code from a further compromised ThinkPHP server to attain first foothold,” Akamai scientists Ron Mankivsky and Maxim Zavodchik mentioned. “Immediately after correctly exploiting the program, the attackers will put in a Chinese language web shell named Dama to keep persistent obtain to the server.”

The web shell is geared up with quite a few advanced capabilities to obtain process knowledge, upload information, scan network ports, escalate privileges, and navigate the file technique, the latter of which permits threat actors to conduct functions like file enhancing, deletion, and timestamp modification for obfuscation applications.
“The recent attacks originated by a Chinese-speaking adversary highlight an ongoing craze of attackers applying a absolutely fledged web shell, designed for state-of-the-art victim handle,” the scientists noted. “Apparently, not all qualified clients ended up using ThinkPHP, which suggests that the attackers may possibly be indiscriminately concentrating on a broad assortment of programs.”
Discovered this article appealing? Follow us on Twitter and LinkedIn to browse more distinctive content we article.
Some parts of this article are sourced from:
thehackernews.com


 Muhstik Botnet Exploiting Apache RocketMQ Flaw to Expand DDoS Attacks
Muhstik Botnet Exploiting Apache RocketMQ Flaw to Expand DDoS Attacks