An unfamiliar risk actor is exploiting recognised security flaws in Microsoft Exchange Server to deploy a keylogger malware in assaults targeting entities in Africa and the Center East.
Russian cybersecurity organization Beneficial Technologies explained it identified more than 30 victims spanning govt businesses, financial institutions, IT businesses, and educational institutions. The initial-at any time compromise dates back again to 2021.
“This keylogger was gathering account qualifications into a file obtainable through a exclusive path from the internet,” the business claimed in a report released very last week.
Nations specific by the intrusion established involve Russia, the U.A.E., Kuwait, Oman, Niger, Nigeria, Ethiopia, Mauritius, Jordan, and Lebanon.

The attack chains begin with the exploitation of ProxyShell flaws (CVE-2021-34473, CVE-2021-34523, and CVE-2021-31207) that have been originally patched by Microsoft in May 2021.
Profitable exploitation of the vulnerabilities could let an attacker to bypass authentication, elevate their privileges, and have out unauthenticated, distant code execution. The exploitation chain was learned and printed by Orange Tsai from the DEVCORE Analysis Workforce.
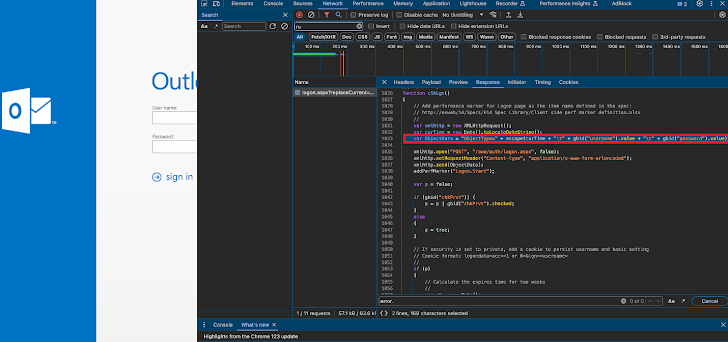
The ProxyShell exploitation is adopted by the risk actors including the keylogger to the server principal web site (“logon.aspx”), in addition to injecting code liable for capturing the qualifications to a file obtainable from the internet on clicking the signal in button.
Beneficial Technologies stated it can not attribute the attacks to a acknowledged risk actor or team at this phase with no additional facts.

Beside updating their Microsoft Trade Server scenarios to the most up-to-date edition, organizations are urged to glance for likely indications of compromise in the Exchange Server’s principal webpage, like the clkLgn() purpose exactly where the keylogger is inserted.
“If your server has been compromised, recognize the account info that has been stolen and delete the file where this data is stored by hackers,” the company explained. “You can find the route to this file in the logon.aspx file.”
Uncovered this write-up attention-grabbing? Comply with us on Twitter and LinkedIn to read through much more exceptional material we submit.
Some parts of this article are sourced from:
thehackernews.com


 QNAP Patches New Flaws in QTS and QuTS hero Impacting NAS Appliances
QNAP Patches New Flaws in QTS and QuTS hero Impacting NAS Appliances