Handling vulnerabilities in the consistently evolving technological landscape is a difficult task. Although vulnerabilities arise on a regular basis, not all vulnerabilities present the exact same stage of risk. Standard metrics this sort of as CVSS rating or the number of vulnerabilities are inadequate for helpful vulnerability management as they deficiency company context, prioritization, and being familiar with of attackers’ chances. Vulnerabilities only signify a small section of the attack floor that attackers can leverage.
To begin with, businesses made use of handbook solutions to address recognised security weaknesses, but as technology and cyber threats developed, a more automated and complete tactic turned essential. On the other hand, legacy vulnerability administration equipment were created principally for compliance and contemporary resources nevertheless confront troubles in prioritization and constrained resources, specifically in dynamic and agile cloud environments.
Modern day vulnerability management integrates security resources this kind of as scanners, danger intelligence, and remediation workflows to give a a lot more successful and powerful option. Nonetheless, companies carry on to face problems these as:
- A developing checklist of vulnerabilities
- Inaccurate prioritization
- Missing organization context
- Misalignment of priorities and means concerning IT and security groups
- Absence of protection and a unified see of risk
Exposures are broader than a regular CVE and can encompass a lot more than just vulnerabilities. Exposures can consequence from many aspects, such as human mistake, improperly outlined security controls, and inadequately designed and unsecured architecture. Several security instruments are inclined to aim on unique styles of exposures, these types of as vulnerabilities, misconfigurations, or identities, and deal with every single one in isolation. Nevertheless, this solution fails to consider how attackers check out networks and systems. Attackers don’t glance at the specific publicity – alternatively, they leverage the toxic mixture of vulnerabilities, misconfigurations, overly permissive identities, and other security gaps to transfer throughout methods and get to sensitive assets. This route is known as an attack route and this kind of lateral motion can go undetected for months or months, enabling attackers to induce sizeable and ongoing injury although hiding within networks.
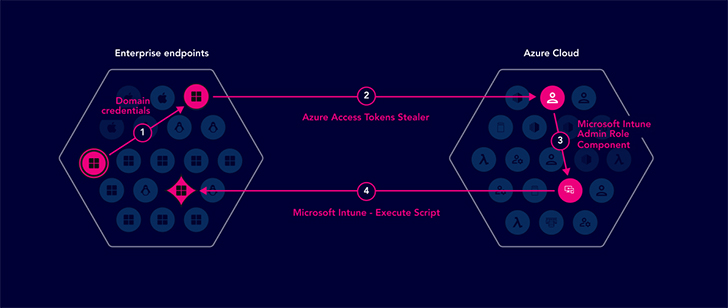
A modern exposure administration system entails combining multiple exposures on to an attack graph to fully grasp the connection and context of risk in direction of critical assets. This will allow for qualified remediation that lowers risk in the most expense-effective fashion. To make a modern-day publicity management application, organizations should identify the evolution of threat actors and their methods, build an operational course of action for making sure constant security posture improvement, and implement a plan consisting of remediation setting up, remediation review, risk mitigation and mitigation verification.
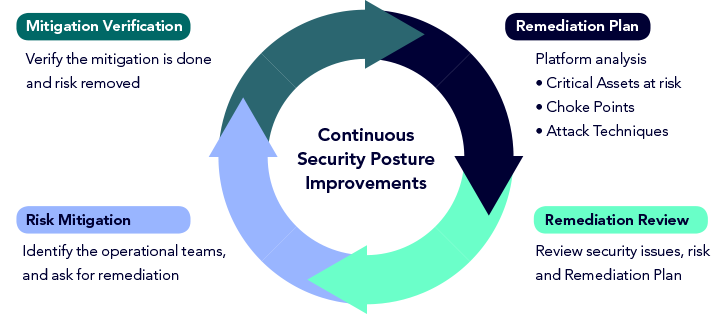
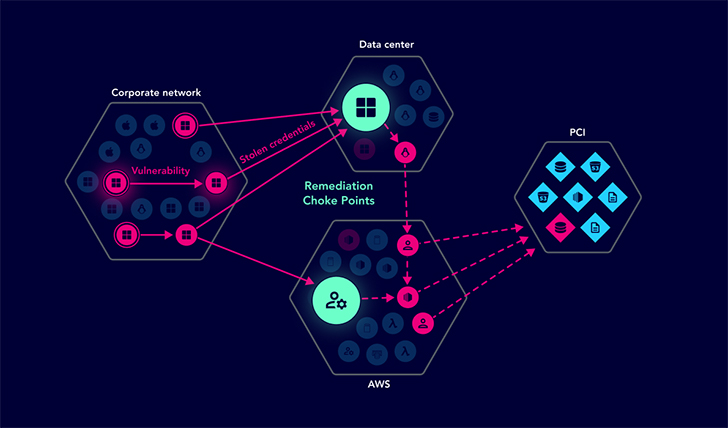
At XM Cyber, we believe that only by combining many exposures alongside one another onto an attack graph that visualizes all achievable attack paths, can we understand the relationship and context of risk towards critical assets. And by being familiar with context, we can properly prioritize issues to concentration on the exposures that have to have remediating where they converge on choke points. This permits for effective remediation that lessens risk in the most charge-efficient manner.
The a few key pillars to constructing a modern-day exposure administration program are:
- Being familiar with exposure insights – repeatedly identify and monitor prospective dangers to critical belongings, as nicely as determining any gaps in security controls or deviations from compliance criteria.
- Examining attack paths – generate an attack graph watch that visualizes all doable attack paths to critical property.
- Prioritizing remediation initiatives – concentrate on the most critical issues and choke factors that demand speedy interest to cut down risk exposure in a expense-productive manner.
By combining these a few pillars, businesses can build a extensive and powerful publicity management program that can help to protect critical assets and minimize general risk exposure. This enables for productive remediation that cuts down risk in the most price tag-productive fashion. By consistently examining and checking exposures, corporations can construct a sustainable and scalable course of action for running risk in excess of time.
Take note: This post is written and contributed by Michael A. Greenberg, Director of Item Marketing at XM Cyber.
Uncovered this posting fascinating? Stick to us on Twitter and LinkedIn to browse a lot more special content material we put up.
Some parts of this article are sourced from:
thehackernews.com


 Lazarus Subgroup Targeting Apple Devices with New RustBucket macOS Malware
Lazarus Subgroup Targeting Apple Devices with New RustBucket macOS Malware