A beforehand undocumented Android banking trojan dubbed MMRat has been observed targeting cell users in Southeast Asia since late June 2023 to remotely commandeer the products and carry out financial fraud.
“The malware, named just after its distinctive offer title com.mm.person, can seize consumer input and screen articles, and can also remotely regulate target products by means of a variety of strategies, enabling its operators to carry out lender fraud on the victim’s gadget,” Craze Micro claimed.
What can make MMRat stand apart from other folks of its type is the use of a custom-made command-and-manage (C2) protocol based on protocol buffers (aka protobuf) to efficiently transfer huge volumes of knowledge from compromised handsets, demonstrating the rising sophistication of Android malware.
Doable targets primarily based on the language utilised in the phishing internet pages contain Indonesia, Vietnam, Singapore, and the Philippines.

The entry place of the attacks is a network of phishing sites that mimic official application suppliers, even though how victims are directed to these back links is presently unidentified. MMRat generally masquerades as an formal government or a relationship app.
After set up, the app leans heavily on Android accessibility company and MediaProjection API, both equally of which have been leveraged by yet another Android economical trojan known as SpyNote, to have out its functions. The malware is also capable of abusing its accessibility permissions to grant itself other permissions and modify configurations.
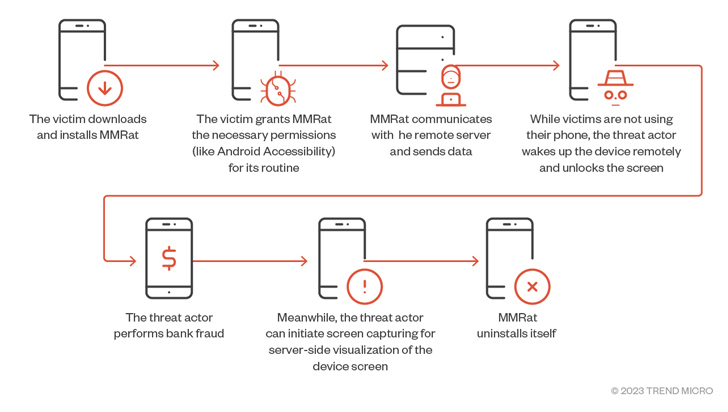
It more sets up persistence to survive among reboots and initiates communications with a remote server to await guidance and exfiltrate the outcomes of the execution of all those commands back again to it. The trojan employs different mixtures of ports and protocols for features this kind of as info exfiltration, video streaming, and C2 management.
MMRat possesses the means to accumulate a wide selection of machine details and own information, which includes sign energy, monitor status, and battery stats, put in purposes, and speak to lists. It really is suspected that the threat actor makes use of the specifics to carry out some kind of sufferer profiling ahead of going to the next stage.
Some of the other options of MMRat encompass recording true-time display material and capturing the lock display sample so as to make it possible for the threat actor to remotely obtain access to the victim’s gadget when it is locked and not actively in use.

“The MMRat malware abuses the Accessibility support to remotely control the victim’s unit, performing actions these as gestures, unlocking screens, and inputting text, among the some others,” Craze Micro said.
“This can be made use of by threat actors — in conjunction with stolen qualifications — to complete bank fraud.”
The assaults close with MMRat deleting itself upon getting the C2 command UNINSTALL_Application, which typically can take position soon after a productive fraudulent transaction, proficiently taking away all traces of an infection from the product.
To mitigate threats posed by these kinds of potent malware, it’s advisable that end users only obtain applications from official resources, scrutinize application assessments, and look at the permissions an application requests for obtain to before usage.
Found this write-up exciting? Abide by us on Twitter and LinkedIn to study far more special material we write-up.
Some parts of this article are sourced from:
thehackernews.com


 China-Linked BadBazaar Android Spyware Targeting Signal and Telegram Users
China-Linked BadBazaar Android Spyware Targeting Signal and Telegram Users