Cybersecurity researchers have identified malicious Android applications for Signal and Telegram dispersed by way of the Google Enjoy Store and Samsung Galaxy Retail outlet that are engineered to produce the BadBazaar spy ware on contaminated devices.
Slovakian firm ESET attributed the campaign to a China-joined actor termed GREF.
“Most very likely energetic considering the fact that July 2020 and since July 2022, respectively, the strategies have dispersed the Android BadBazaar espionage code by the Google Engage in retail outlet, Samsung Galaxy Keep, and committed sites symbolizing the malicious apps Signal As well as Messenger and FlyGram,” security researcher Lukáš Štefanko reported in a new report shared with The Hacker News.
Victims have been mainly detected in Germany, Poland, and the U.S., adopted by Ukraine, Australia, Brazil, Denmark, Congo-Kinshasa, Hong Kong, Hungary, Lithuania, the Netherlands, Portugal, Singapore, Spain, and Yemen.
BadBazaar was first documented by Lookout in November 2022 as targeting the Uyghur group in China with seemingly benign Android and iOS apps that, the moment set up, harvests a wide selection of facts, including simply call logs, SMS messages, destinations, and other folks.
The before marketing campaign, lively considering that at minimum 2018, is also noteworthy for the simple fact that the rogue Android apps had been never posted to the Play Shop. The two the apps have considering that been taken down from google’s app storefront, but they proceed to be out there on the Samsung Galaxy Retailer.

The specifics of the apps are as follows –
- Sign Furthermore Messenger (org.thoughtcrime.securesmsplus) – 100+ downloads since July 2022, also available via signalplus[.]org
- FlyGram (org.telegram.FlyGram) – 5,000+ downloads due to the fact June 2020, also accessible by means of flygram[.]org
Further than these distribution mechanisms, it really is claimed that probable victims have also been probably tricked into installing the applications from a Uyghur Telegram team targeted on sharing Android apps. The group has about 1,300 customers.
The two Signal Moreover Messenger and FlyGram are designed to collect and exfiltrate delicate user knowledge, with each and every app dedicated to also amassing info from the respective applications they mimic: Signal and Telegram.
This includes the means to obtain Sign PIN and Telegram chat backups really should the target help a Cloud Sync attribute from the trojanized app.
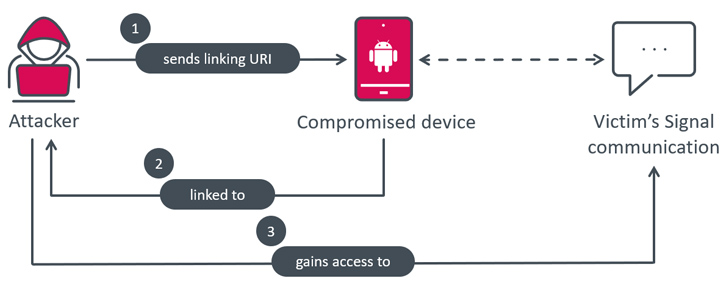
In what is actually a novel twist, Signal In addition Messenger represents the initially documented circumstance of surveillance of a victim’s Signal communications by covertly linking the compromised device to the attacker’s Sign account without demanding any user conversation.
“BadBazaar, the malware responsible for the spying, bypasses the regular QR code scan and user simply click system by getting the required URI from its [command-and-control] server, and instantly triggering the important action when the Hyperlink gadget button is clicked,” Štefanko spelled out.

“This enables the malware to secretly website link the victim’s smartphone to the attacker’s product, making it possible for them to spy on Sign communications without having the victim’s expertise.”
FlyGram, for its element, also implements a function named SSL pinning to evade evaluation by embedding the certification within just the APK file these that only encrypted interaction with the predefined certification is authorized, thereby making it complicated to intercept and evaluate the network targeted traffic between the app and its server.
An evaluation of the application Cloud Sync feature has further uncovered that every consumer who registers for the service is assigned a distinct ID that’s sequentially incremented. It is estimated that 13,953 people (such as ESET) set up FlyGram and activated the Cloud Sync attribute.
ESET mentioned it’s continuing to monitor GREF as a separate cluster irrespective of prior open up-source reporting connecting the team to APT15, citing deficiency of definitive evidence.
“BadBazaar’s key intent is to exfiltrate device facts, the call listing, contact logs, and the checklist of mounted apps, and to carry out espionage on Signal messages by secretly linking the victim’s Signal Furthermore Messenger app to the attacker’s gadget,” Štefanko stated.
Discovered this article attention-grabbing? Adhere to us on Twitter and LinkedIn to examine additional distinctive content we write-up.
Some parts of this article are sourced from:
thehackernews.com

 How to Prevent ChatGPT From Stealing Your Content & Traffic
How to Prevent ChatGPT From Stealing Your Content & Traffic