Microsoft has warned that adversaries are utilizing OAuth programs as an automation software to deploy virtual equipment (VMs) for cryptocurrency mining and launch phishing assaults.
“Menace actors compromise user accounts to produce, modify, and grant large privileges to OAuth programs that they can misuse to conceal malicious activity,” the Microsoft Danger Intelligence crew stated in an investigation.
“The misuse of OAuth also enables menace actors to manage accessibility to purposes even if they eliminate entry to the in the beginning compromised account.”
Forthcoming WEBINAR Beat AI-Powered Threats with Zero Have confidence in – Webinar for Security Pros
Common security steps would not reduce it in today’s entire world. It really is time for Zero Have faith in Security. Secure your info like hardly ever ahead of.
Be a part of Now
OAuth, brief for Open up Authorization, is an authorization and delegation framework (as opposed to authentication) that supplies apps the ability to securely accessibility data from other internet sites without handing more than passwords.
In the assaults detailed by Microsoft, threat actors have been observed launching phishing or password-spraying assaults versus inadequately secured accounts with permissions to develop or modify OAuth programs.
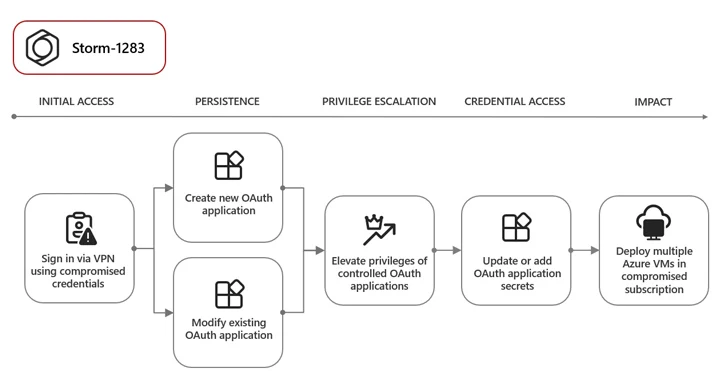
A person such adversary is Storm-1283, which has leveraged a compromised user account to generate an OAuth application and deploy VMs for cryptomining. On top of that, the attackers modified present OAuth applications to the account experienced obtain to by adding an excess set of credentials to facilitate the same goals.
In a further occasion, an unidentified actor compromised consumer accounts and created OAuth programs to retain persistence and to launch email phishing assaults that employ an adversary-in-the-middle (AiTM) phishing package to plunder session cookies from their targets and bypass authentication steps.

“In some cases, pursuing the stolen session cookie replay exercise, the actor leveraged the compromised person account to perform BEC economic fraud reconnaissance by opening email attachments in Microsoft Outlook Web Application (OWA) that include particular key terms these kinds of as ‘payment’ and ‘invoice,” Microsoft mentioned.
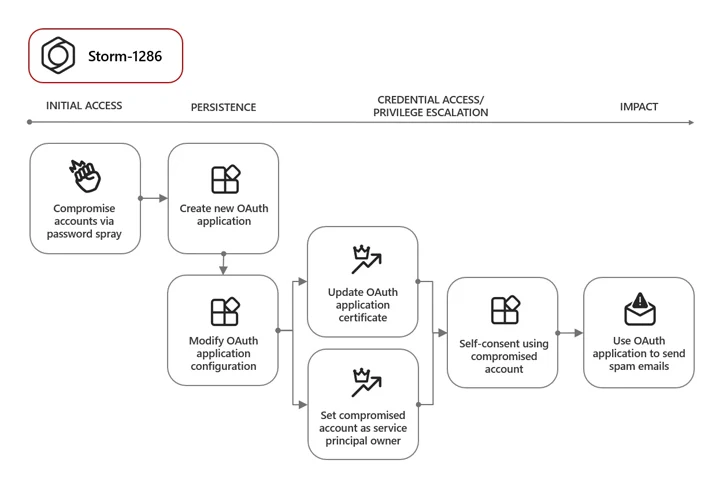
Other situations detected by the tech big subsequent the theft of session cookies involve the development of OAuth programs to distribute phishing email messages and perform significant-scale spamming activity. Microsoft is monitoring the latter as Storm-1286.
To mitigate the risks connected with these types of assaults, it’s suggested that organizations enforce multi-factor authentication (MFA), permit conditional accessibility policies, and routinely audit apps and consented permissions.
Identified this article interesting? Follow us on Twitter and LinkedIn to browse far more distinctive written content we article.
Some parts of this article are sourced from:
thehackernews.com

 Major Cyber Attack Paralyzes Kyivstar – Ukraine’s Largest Telecom Operator
Major Cyber Attack Paralyzes Kyivstar – Ukraine’s Largest Telecom Operator