Malware investigation encompasses a broad vary of things to do, which include inspecting the malware’s network visitors. To be powerful at it, it can be crucial to understand the widespread troubles and how to overcome them. Here are three common issues you may perhaps face and the instruments you are going to need to tackle them.
Decrypting HTTPS website traffic
Hypertext Transfer Protocol Safe (HTTPS), the protocol for secure on the internet conversation, has develop into a device for malware to conceal their destructive things to do. By cloaking knowledge trade between infected products and command-and-manage (C&C) servers, malware can run undetected, exfiltrating delicate information, installing further payloads, and getting guidance from the operators.
Still, with the proper software, decrypting HTTPS traffic is an easy task. For this intent, we can use a person-in-the-middle (MITM) proxy. The MITM proxy is effective as an middleman among the client and the server, intercepting their communication.
The MITM proxy aids analysts in authentic-time checking of the malware’s network targeted visitors, offering them with a apparent watch of its actions. Amongst other factors, analysts can access content material of ask for and reaction packets, IPs, and URLs to check out the particulars of the malware’s conversation and identify stolen facts. The software is significantly beneficial for extracting SSL keys used by the malware.
Use circumstance
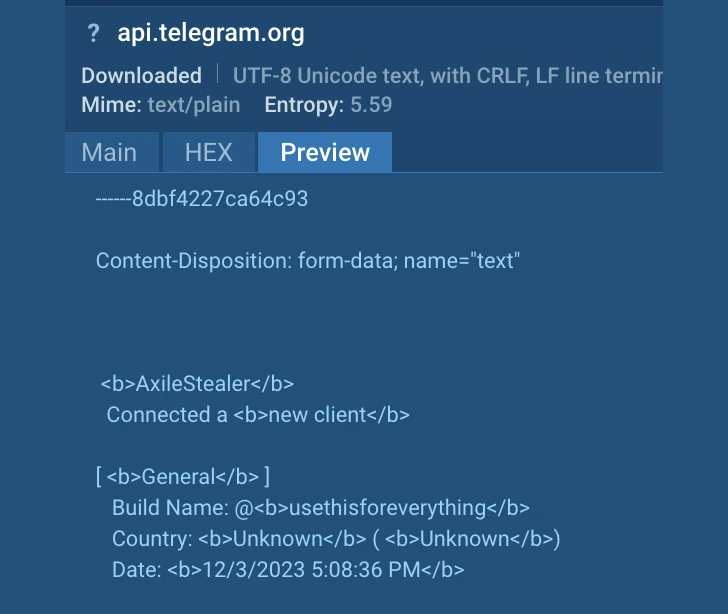 Information and facts about AxileStealer delivered by the ANY.Operate sandbox
Information and facts about AxileStealer delivered by the ANY.Operate sandbox
In this example, the original file, 237.06 KB in dimension, drops AxilStealer’s executable file, 129.54 KB in dimension. As a standard stealer, it gains access to passwords saved in web browsers and begins to transfer them to attackers via a Telegram messenger relationship.
The destructive action is indicated by the rule “STEALER [ANY.RUN] Endeavor to exfiltrate by means of Telegram”. Many thanks to the MITM proxy function, the malware’s targeted traffic is decrypted, revealing more specifics about the incident.
Malware Examination
Use a MITM proxy and dozens of other highly developed features for in-depth malware investigation in the ANY.Operate sandbox.
Request a totally free trial
Discovering malware’s household
Malware family identification is a essential aspect of any cyber investigation. Yara and Suricata policies are typically employed tools for this activity, but their performance may well be limited when working with malware samples whose servers are no for a longer period active.
FakeNET provides a resolution to this challenge by creating a fake server relationship that responds to malware requests. Tricking the malware to ship a request triggers a Suricata or YARA rule, which correctly identifies the malware family.
Use scenario
 Inactive servers detected by the ANY.Operate sandbox
Inactive servers detected by the ANY.Operate sandbox
When analyzing this sample, the sandbox factors to the point that the malware’s servers are unresponsive.
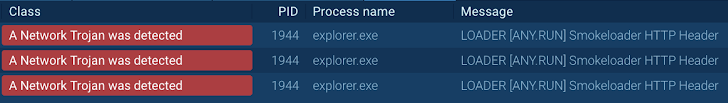 Smoke Loader malware recognized making use of FakeNET
Smoke Loader malware recognized making use of FakeNET
Yet, just after enabling the FakeNET attribute, the destructive software package instantly sends a request to a fake server, triggering the network rule that identifies it as Smoke Loader.
Catching geo-qualified and evasive malware
Many assaults and phishing strategies concentrate on certain geographic areas or nations. Subsequently, they include mechanisms like IP geolocation, language detection, or website blocking which may limit analysts’ capability to detect them.
Alongside geo-targeting, malware operators may leverage methods to evade examination in sandbox environments. A widespread tactic is to verify whether the method is utilizing a datacenter IP address. If confirmed, the destructive software program stops execution.
To counter these obstacles, analysts use a household proxy. This nifty instrument performs by switching the IP tackle of the analyst’s gadget or digital equipment to standard users’ residential IPs from distinctive pieces of the globe.
This feature empowers gurus to bypass geo-restrictions by mimicking nearby customers and analyze destructive routines without the need of revealing their sandbox environment.
Use circumstance
 Smoke Loader malware recognized employing FakeNET
Smoke Loader malware recognized employing FakeNET
Listed here, Xworm promptly checks for a hosting IP address as soon as it is uploaded to a sandbox. Nonetheless, given that the VM has a household proxy, the malware continues to execute and connects to its command-and-management server.
Check out all of these tools in ANY.Run
Environment up and employing each of the aforementioned equipment individually can just take a good deal of effort and hard work. To obtain and employ all of them with simplicity, use the cloud-centered ANY.Run sandbox.
The critical aspect of the services is interactivity, allowing you to safely and securely have interaction with malware and the infected technique just like you would on your possess laptop.
You can check out these and quite a few other options of ANY.Operate, which include personal room for your workforce, Windows 7, 8, 10, 11 VMs, and API integration totally for free.
Just use a 14-day trial, no strings attached.
Found this short article fascinating? Comply with us on Twitter and LinkedIn to go through much more exclusive content we publish.
Some parts of this article are sourced from:
thehackernews.com


 Microsoft Warns of Hackers Exploiting OAuth for Cryptocurrency Mining and Phishing
Microsoft Warns of Hackers Exploiting OAuth for Cryptocurrency Mining and Phishing