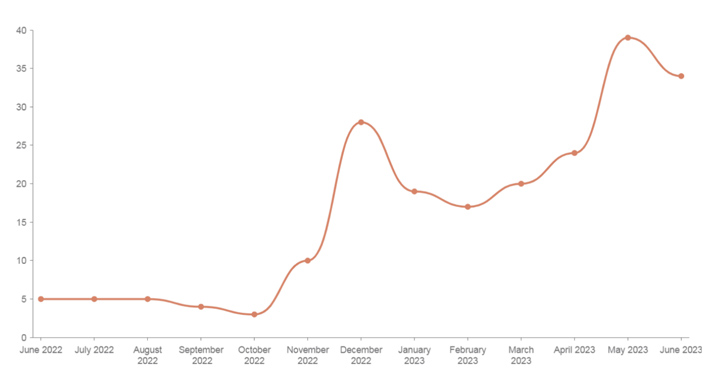
Mallox ransomware things to do in 2023 have witnessed a 174% increase when compared to the past 12 months, new results from Palo Alto Networks Unit 42 expose.
“Mallox ransomware, like many other ransomware menace actors, follows the double extortion pattern: stealing information ahead of encrypting an organization’s information, and then threatening to publish the stolen info on a leak internet site as leverage to persuade victims to shell out the ransom cost,” security researchers Lior Rochberger and Shimi Cohen explained in a new report shared with The Hacker Information.
Mallox is joined to a risk actor that’s also connected to other ransomware strains, these types of as TargetCompany, Tohnichi, Fargo, and, most lately, Xollam. It first burst onto the scene in June 2021.
Some of the outstanding sectors specific by Mallox are manufacturing, professional and legal expert services, and wholesale and retail.
A noteworthy factor of the team is its sample of exploiting badly secured MS-SQL servers by using dictionary assaults as a penetration vector to compromise victims’ networks. Xollam is a deviation from the norm in that it has been observed working with malicious OneNote file attachments for first access, as thorough by Development Micro very last thirty day period.
Upon gaining a productive foothold on the contaminated host, a PowerShell command is executed to retrieve the ransomware payload from a remote server.
The binary, for its part, attempts to halt and take away SQL-associated solutions, delete volume shadow copies, very clear procedure occasion logs, terminate security-connected processes, and bypass Raccine, an open up-source software designed to counter ransomware assaults, prior to commencing its encryption process, immediately after which a ransom note is dropped in every single listing.
Future WEBINARShield Against Insider Threats: Grasp SaaS Security Posture Management
Concerned about insider threats? We have got you covered! Be part of this webinar to examine useful methods and the techniques of proactive security with SaaS Security Posture Administration.
Join Right now
TargetCompany continues to be a compact, closed team, but it has also been observed recruiting affiliate marketers for the Mallox ransomware-as-a-company (RaaS) affiliate plan on the RAMP cybercrime discussion board.
The improvement comes as ransomware continues to be a worthwhile money plan, netting cybercriminals no considerably less than $449.1 million in the initial fifty percent of 2023 by itself, for every Chainalysis.
“The Mallox ransomware team has been much more active in the earlier handful of months, and their new recruiting attempts may allow them to attack far more businesses if the recruitment drive is thriving,” the researchers said.
Observed this post appealing? Abide by us on Twitter and LinkedIn to read through a lot more exclusive articles we submit.
Some parts of this article are sourced from:
thehackernews.com


 Apache OpenMeetings Web Conferencing Tool Exposed to Critical Vulnerabilities
Apache OpenMeetings Web Conferencing Tool Exposed to Critical Vulnerabilities