An unknown menace actor is leveraging malicious npm deals to focus on developers with an aim to steal supply code and configuration documents from sufferer equipment, a sign of how threats lurk regularly in open-source repositories.
“The risk actor guiding this campaign has been connected to malicious exercise dating back again to 2021,” computer software provide chain security business Checkmarx stated in a report shared with The Hacker News. “Because then, they have repeatedly revealed destructive offers.”
The most recent report is a continuation of the very same campaign that Phylum disclosed at the start out of the thirty day period in which a range of npm modules have been engineered to exfiltrate worthwhile information and facts to a distant server.
The packages, by style, are configured to execute instantly write-up-installation by usually means of a postinstall hook outlined in the offer.json file. It triggers the launch of preinstall.js, which spawns index.js to seize the process metadata as very well as harvest source code and strategies from particular directories.
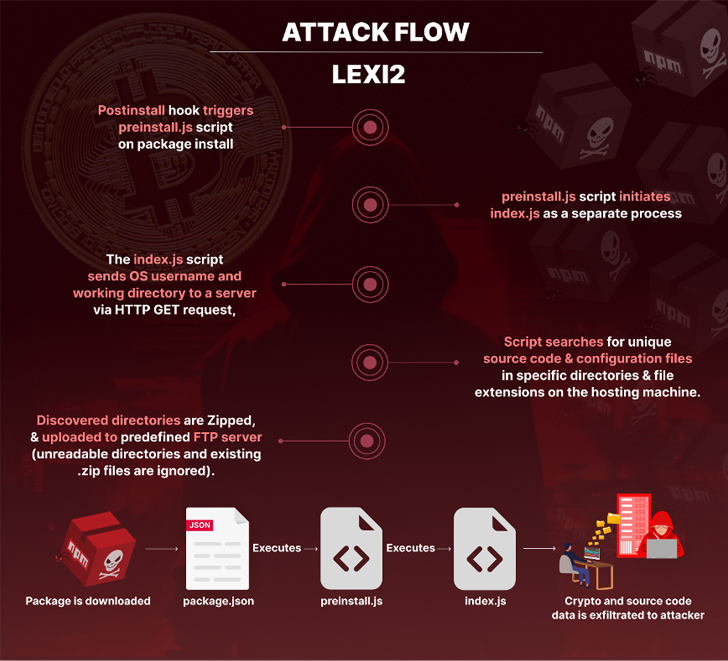
The attack culminates with the script producing a ZIP archive of the details and transmitting it to a predefined FTP server.
A prevalent trait that connects all the packages is the use of “lexi2” as the writer in the package.json file, enabling Checkmarx to trace the origins of the activity as significantly again as 2021.

Whilst the actual targets of the campaign are unclear, the use of deal names these kinds of as binarium-customer, binarium-crm, and rocketrefer recommend that the targeting is geared in the direction of the cryptocurrency sector.
“The cryptocurrency sector stays a sizzling focus on, and it is really critical to understand that we’re not just grappling with malicious packages, but also persistent adversaries whose continuous and meticulously planned assaults day back months or even many years,” security researcher Yehuda Gelb reported.
Observed this article attention-grabbing? Comply with us on Twitter and LinkedIn to read through far more exclusive content we article.
Some parts of this article are sourced from:
thehackernews.com


 Alert: Juniper Firewalls, Openfire, and Apache RocketMQ Under Attack from New Exploits
Alert: Juniper Firewalls, Openfire, and Apache RocketMQ Under Attack from New Exploits