Cybersecurity scientists have uncovered an current model of a backdoor named LODEINFO that’s distributed by way of spear-phishing assaults.
The findings occur from Japanese organization ITOCHU Cyber & Intelligence, which stated the malware “has been up-to-date with new options, as perfectly as modifications to the anti-examination (analysis avoidance) approaches.”
LODEINFO (variations .6.6 and .6.7) was 1st documented by Kaspersky in November 2022, detailing its capabilities to execute arbitrary shellcode, just take screenshots, and exfiltrate documents back again to an actor-controlled server.
A thirty day period later, ESET disclosed attacks focusing on Japanese political establishments that led to the deployment of LODEINFO.

The backdoor is the get the job done of a Chinese nation-state actor acknowledged as Stone Panda (aka APT10, Bronze Riverside, Cicada, Earth Tengshe, MirrorFace, and Potassium), which has a heritage of orchestrating assaults focusing on Japan considering that 2021.
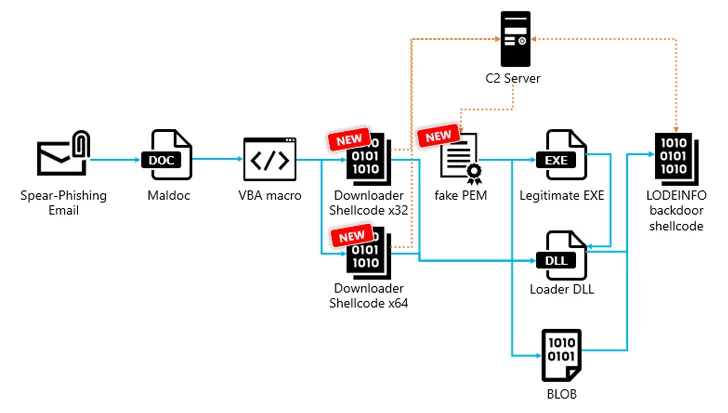
Attack chains commence with phishing emails bearing malicious Microsoft Term files that, when opened, execute VBA macros to launch downloader shellcode able of in the end executing the LODEINFO implant.
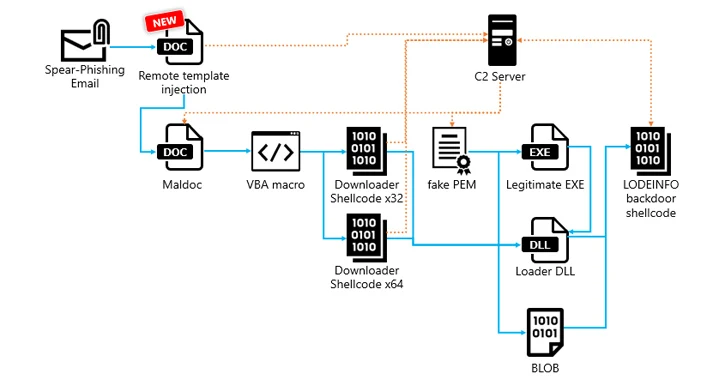
LODEINFO an infection paths noticed in 2023 have also been observed producing use of distant template injection techniques to retrieve and execute destructive macros hosted on the adversary’s infrastructure each individual time the sufferer opens a entice Phrase document containing the template.
What is more, checks are claimed to have been included to verify the language options of Microsoft Business office to confirm if it truly is Japanese someday all around June 2023, only for it be eliminated a month afterwards in attacks leveraging LODEINFO edition .7.1.
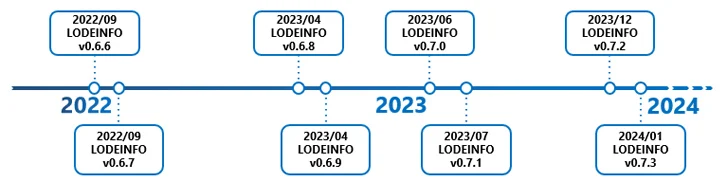
“In addition, the filename of the maldoc itself has been altered from Japanese to English,” ITOCHU pointed out. “From this, we consider that v0.7.1 was most likely made use of to attack environments in languages other than Japanese.”
An additional noteworthy modify in assaults offering LODEINFO version .7.1 is the introduction of a new intermediate stage that requires the shellcode downloader fetching a file that masquerades as a Privateness-Increased Mail (PEM) from a C2 server, which, in flip, masses the backdoor specifically in memory.

The downloader shares similarities with a acknowledged fileless downloader dubbed DOWNIISSA primarily based on the self-patching mechanism to conceal malicious code, encoding technique for command-and-handle (C2) server facts, and the composition of the details decrypted from the phony PEM file.
“LODEINFO backdoor shellcode is a fileless malware that makes it possible for attackers to remotely entry and function contaminated hosts,” the firm stated, with samples identified in 2023 and 2024 incorporating further instructions. The most up-to-date version of LODEINFO is .7.3.
“As a countermeasure, considering the fact that equally the downloader shellcode and the backdoor shellcode of LODEINFO are fileless malware, it is essential to introduce a product that can scan and detect malware in memory in purchase to detect it,” it additional.
Discovered this short article exciting? Follow us on Twitter and LinkedIn to examine much more unique material we article.
Some parts of this article are sourced from:
thehackernews.com

 China-backed Hackers Hijack Software Updates to Implant “NSPX30” Spyware
China-backed Hackers Hijack Software Updates to Implant “NSPX30” Spyware