A popular destructive cyber operation has hijacked 1000’s of web sites aimed at East Asian audiences to redirect readers to adult-themed written content because early September 2022.
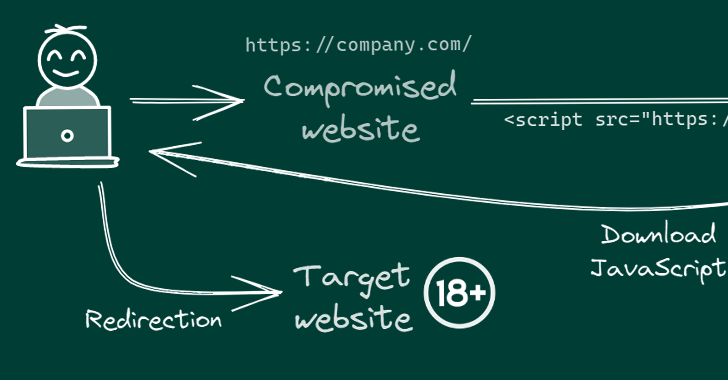
The ongoing campaign entails injecting malicious JavaScript code to the hacked websites, typically connecting to the goal web server using reputable FTP credentials the menace actor formerly received via an mysterious process.
“In several conditions, these were highly safe automobile-created FTP credentials which the attacker was somehow equipped to acquire and leverage for site hijacking,” Wiz claimed in a report posted this month.
The fact that the breached internet sites – owned by the two little firms and multinational corporations – use various tech stacks and hosting service suppliers has built it challenging to trace a common attack vector, the cloud security enterprise pointed out.
That obtaining explained, 1 of the common denominators between the websites is that a vast majority of them are either hosted in China or hosted in a distinct nation but are primed for Chinese buyers.
What is actually a lot more, the URLs hosting the rogue JavaScript code are geofenced to restrict its execution in specified East Asian nations around the world.
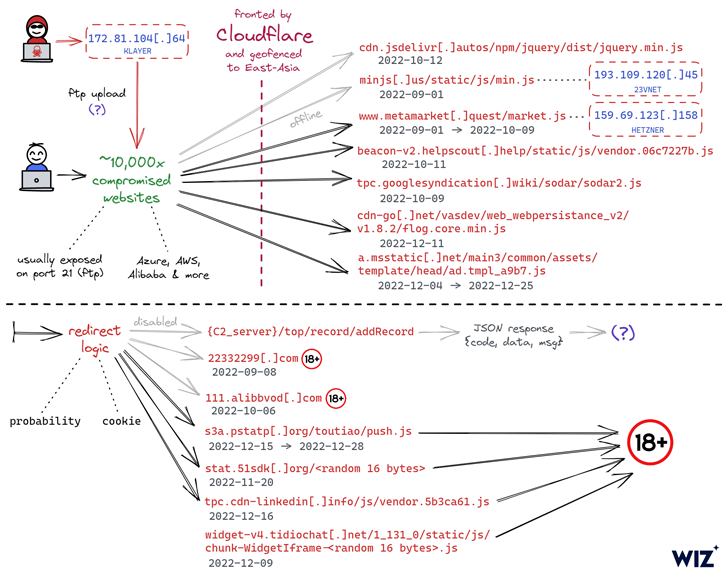
There are also indications that the marketing campaign has set its sights on Android as nicely, with the redirection script major readers to gambling internet websites that urge them to set up an application (APK deal name “com.tyc9n1999co.coandroid”).
The identity of the menace actor is unfamiliar as still, and though their precise motives are yet to be recognized, it is suspected that the goal is to have out advertisement fraud and Web optimization manipulation, or alternatively, push inorganic visitors to these web-sites.
WEBINARDiscover the Concealed Risks of Third-Bash SaaS Applications
Are you mindful of the threats associated with 3rd-bash application accessibility to your company’s SaaS apps? Be part of our webinar to discover about the varieties of permissions remaining granted and how to minimize risk.
RESERVE YOUR SEAT
A further noteworthy aspect of the attacks is the absence of phishing, web skimming, or malware an infection.
“We stay not sure as to how the menace actor has been gaining preliminary accessibility to so a lot of internet websites, and we have nevertheless to detect any considerable commonalities involving the impacted servers other than their use of FTP,” scientists Amitai Cohen and Barak Sharoni reported.
“Whilst it is unlikely that the danger actor is using a -working day vulnerability given the evidently very low sophistication of the attack, we won’t be able to rule this out as an solution.”
Found this posting attention-grabbing? Stick to us on Twitter and LinkedIn to study extra exceptional material we post.
Some parts of this article are sourced from:
thehackernews.com

 Fake ChatGPT Chrome Extension Hijacking Facebook Accounts for Malicious Advertising
Fake ChatGPT Chrome Extension Hijacking Facebook Accounts for Malicious Advertising