Cybersecurity scientists have found an attack marketing campaign that targets numerous Israeli entities with publicly-obtainable frameworks like Donut and Sliver.
The marketing campaign, believed to be highly focused in nature, “leverage goal-particular infrastructure and customized WordPress web-sites as a payload delivery system, but have an impact on a selection of entities throughout unrelated verticals, and depend on nicely-acknowledged open-supply malware,” HarfangLab said in a report final 7 days.
The French enterprise is tracking the exercise below the identify Supposed Grasshopper. It is a reference to an attacker-managed server (“auth.economy-gov-il[.]com/Meant_GRASSHOPPER.bin”), to which a initially-stage downloader connects to.
This downloader, created in Nim, is rudimentary and is tasked with downloading the 2nd-phase malware from the staging server. It’s sent by means of a virtual really hard disk (VHD) file which is suspected to be propagated through custom WordPress websites as section of a travel-by download plan.

The 2nd-phase payload retrieved from the server is Donut, a shellcode generation framework, which serves as a conduit for deploying an open up-source Cobalt Strike different termed Sliver.
“The operators also place some notable attempts in attaining focused infrastructure and deploying a realistic WordPress website to deliver payloads,” the researchers mentioned. “All round, this campaign feels like it could realistically be the function of a little crew.”
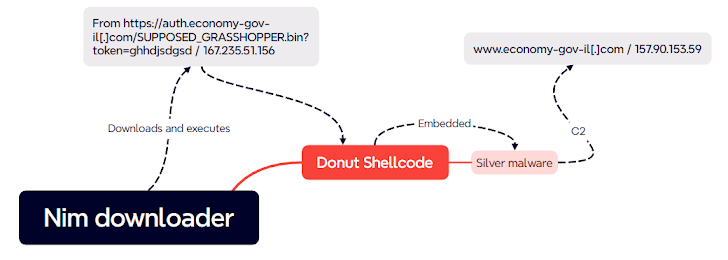
The stop intention of the campaign is presently unidentified, although HarfangLab theorized that it could also be connected with a genuine penetration screening operation, a risk that raises its very own set of questions encompassing transparency and impersonating Israeli government businesses.
The disclosure comes as the SonicWall Capture Labs menace analysis team detailed an infection chain that employs booby-trapped Excel spreadsheets as a starting place to drop a trojan recognised as Orcinius.
“This is a multi-phase trojan that is working with Dropbox and Google Docs to down load second-phase payloads and keep current,” the company explained. “It contains an obfuscated VBA macro that hooks into Windows to check running windows and keystrokes and makes persistence working with registry keys.”
Uncovered this post intriguing? Observe us on Twitter and LinkedIn to browse much more exceptional material we article.
Some parts of this article are sourced from:
thehackernews.com


 South Korean ERP Vendor’s Server Hacked to Spread Xctdoor Malware
South Korean ERP Vendor’s Server Hacked to Spread Xctdoor Malware