The loader-as-a-service (LaaS) identified as FakeBat has become one of the most prevalent loader malware family members distributed applying the push-by obtain strategy this calendar year, conclusions from Sekoia expose.
“FakeBat largely aims to obtain and execute the upcoming-stage payload, this kind of as IcedID, Lumma, RedLine, SmokeLoader, SectopRAT, and Ursnif,” the enterprise claimed in a Tuesday evaluation.
Travel-by assaults entail the use of techniques like lookup motor optimization (Search engine optimization) poisoning, malvertising, and nefarious code injections into compromised sites to entice people into downloading bogus software package installers or browser updates.
The use of malware loaders over the past number of several years dovetails with the expanding use of landing webpages impersonating authentic software program sites by passing them off as genuine installers. This ties into the larger sized element that phishing and social engineering continue to be a person of the danger actors’ primary methods to purchase preliminary accessibility.

FakeBat, also identified as EugenLoader and PaykLoader, has been provided to other cybercriminals beneath a LaaS subscription product on underground message boards by a Russian-speaking menace actor named Eugenfest (aka Payk_34) since at the very least December 2022.
The loader is intended to bypass security mechanisms and presents buyers with possibilities to make builds employing templates to trojanize respectable computer software as properly as monitor installations around time as a result of an administration panel.
Even though the previously versions created use of an MSI structure for the malware builds, current iterations noticed given that September 2023 have switched to an MSIX structure and extra a digital signature to the installer with a legitimate certificate to sidestep Microsoft SmartScreen protections.
The malware is available for $1,000 for every 7 days and $2,500 for each thirty day period for the MSI format, $1,500 for each week and $4,000 for every thirty day period for the MSIX format, and $1,800 per 7 days and $5,000 per month for the combined MSI and signature package deal.
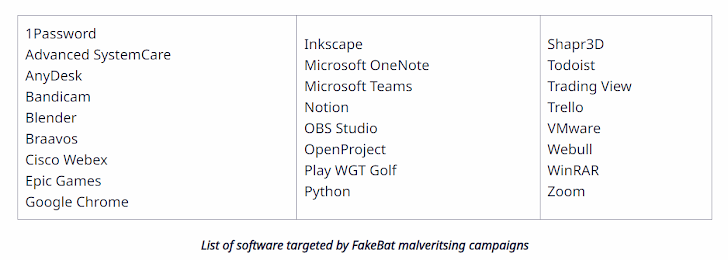
Sekoia claimed it detected unique exercise clusters disseminating FakeBat by three most important strategies: Impersonating popular software by means of malicious Google adverts, phony web browser updates by means of compromised web pages, and social engineering schemes on social networks. This encompasses campaigns most likely connected to the FIN7 team, Nitrogen, and BATLOADER.
“In addition to hosting payloads, FakeBat [command-and-control] servers highly likely filter website traffic based mostly on features these types of as the User-Agent value, the IP tackle, and the area,” Sekoia reported. “This allows the distribution of the malware to unique targets.”
The disclosure arrives as the AhnLab Security Intelligence Middle (ASEC) detailed a malware marketing campaign distributing an additional loader named DBatLoader (aka ModiLoader and NatsoLoader) as a result of invoice-themed phishing e-mails.
It also follows the discovery of infection chains propagating Hijack Loader (aka DOILoader and IDAT Loader) through pirated film down load web sites to in the long run provide the Lumma information and facts stealer.
“This IDATLOADER campaign is using a elaborate infection chain that contains numerous levels of immediate code-based mostly obfuscation together with innovative tips to even further disguise the maliciousness of the code,” Kroll researcher Dave Truman stated.

“The an infection hinged all-around utilizing Microsoft’s mshta.exe to execute code buried deep within just a specifically crafted file masquerading as a PGP Magic formula Crucial. The marketing campaign built use of novel diversifications of popular techniques and hefty obfuscation to hide the malicious code from detection.”
Phishing strategies have even further been noticed offering Remcos RAT, with a new Japanese European danger actor dubbed Unfurling Hemlock leveraging loaders and email messages to fall binary data files that act as a “cluster bomb” to unfold unique malware strains at once.
“The malware currently being dispersed utilizing this strategy is primarily comprised of stealers, these types of as RedLine, RisePro, and Mystic Stealer, and loaders this kind of as Amadey and SmokeLoader,” Outpost24 researcher Hector Garcia reported.
“Most of the very first phases had been detected being sent by means of email to diverse providers or currently being dropped from exterior web pages that have been contacted by exterior loaders.”
Observed this report intriguing? Adhere to us on Twitter and LinkedIn to browse a lot more unique articles we put up.
Some parts of this article are sourced from:
thehackernews.com

 Israeli Entities Targeted by Cyberattack Using Donut and Sliver Frameworks
Israeli Entities Targeted by Cyberattack Using Donut and Sliver Frameworks