The Iranian risk actor regarded as Agrius is leveraging a new ransomware strain referred to as Moneybird in its assaults concentrating on Israeli businesses.
Agrius, also recognised as Pink Sandstorm (previously Americium), has a monitor file of staging destructive details-wiping attacks aimed at Israel below the guise of ransomware infections.
Microsoft has attributed the menace actor to Iran’s Ministry of Intelligence and Security (MOIS), which also operates MuddyWater. It truly is identified to be lively due to the fact at minimum December 2020.
In December 2022, the hacking crew was attributed to a set of attempted disruptive intrusions that have been directed from diamond industries in South Africa, Israel, and Hong Kong.
These assaults concerned the use of a .NET-centered wiper-turned-ransomware termed Apostle and its successor known as Fantasy. In contrast to Apostle, Moneybird is programmed in C++.
“The use of a new ransomware, penned in C++, is noteworthy, as it demonstrates the group’s growing abilities and ongoing energy in establishing new instruments,” Verify Stage scientists Marc Salinas Fernandez and Jiri Vinopal mentioned.
The infection sequence starts with the exploitation of vulnerabilities inside of internet-uncovered web servers, foremost to the deployment of a web shell referred to as ASPXSpy.
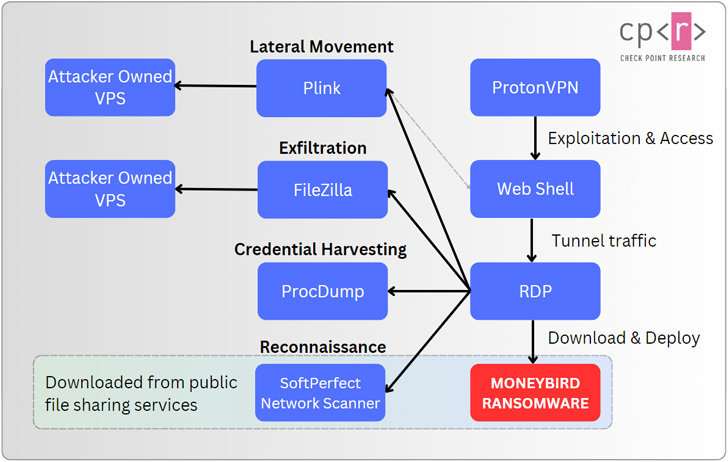
In the subsequent actions, the web shell is employed as a conduit to deliver publicly-acknowledged tools in get to carry out reconnaissance of the victim environment, transfer laterally, harvest credentials, and exfiltrate knowledge.
Also executed on the compromised host is the Moneybird ransomware, which is engineered to encrypt sensitive data files in the “F:Consumer Shares” folder and drop a ransom note urging the corporation to contact them inside 24 hrs or risk getting their stolen data leaked.
“The use of a new ransomware demonstrates the actor’s more attempts to greatly enhance abilities, as nicely as hardening attribution and detection attempts,” the scientists explained. “In spite of these new ‘covers,’ the team carries on to adhere to its standard actions and make use of similar resources and methods as right before.”
Forthcoming WEBINARZero Believe in + Deception: Learn How to Outsmart Attackers!
Explore how Deception can detect highly developed threats, stop lateral movement, and enrich your Zero Belief tactic. Be a part of our insightful webinar!
Preserve My Seat!
Agrius is considerably from the only Iranian point out-sponsored team to engage in cyber operations targeting Israel. A report from Microsoft very last month uncovered MuddyWater’s collaboration with another cluster dubbed Storm-1084 (aka DEV-1084) to deploy the DarkBit ransomware.
The results also come as ClearSky disclosed that no less than eight web sites associated with shipping and delivery, logistics, and economical companies organizations in Israel were being compromised as section of a watering gap attack orchestrated by the Iran-joined Tortoiseshell team.
In a relevant enhancement, Proofpoint disclosed that regional managed services companies (MSPs) in just Israel have been focused by MuddyWater as part of a phishing campaign developed to initiate offer chain attacks in opposition to their downstream buyers.
The organization security firm even more highlighted escalating threats to tiny and medium-sized firms (SMBs) from subtle danger groups, which have been observed leveraging compromised SMB infrastructure for phishing strategies and money theft.
Identified this short article fascinating? Adhere to us on Twitter and LinkedIn to read through more unique content we post.
Some parts of this article are sourced from:
thehackernews.com


 GUAC 0.1 Beta: Google’s Breakthrough Framework for Secure Software Supply Chains
GUAC 0.1 Beta: Google’s Breakthrough Framework for Secure Software Supply Chains