Google on Wednesday declared the .1 Beta variation of GUAC (small for Graph for Knowledge Artifact Composition) for organizations to secure their application supply chains.
To that conclusion, the look for large is creating offered the open supply framework as an API for developers to integrate their have applications and policy engines.
GUAC aims to combination software program security metadata from different resources into a graph database that maps out interactions between software, supporting organizations determine how one piece of software package influences one more.
“Graph for Being familiar with Artifact Composition (GUAC) gives you structured and actionable insights into your application supply chain security situation,” Google suggests in its documentation.
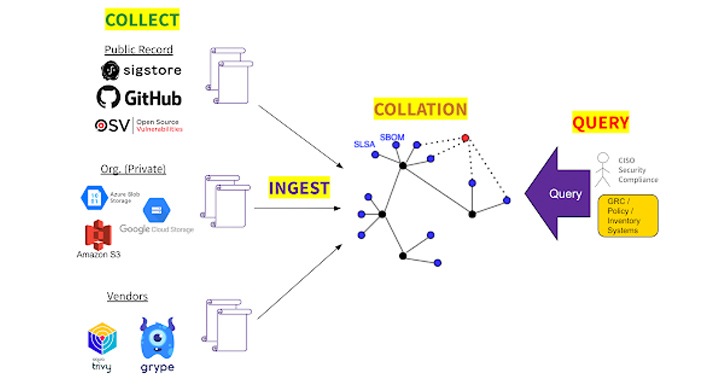
“GUAC ingests software package security metadata, like SBOMs, and maps out the connection amongst software so that you can thoroughly realize your software program security place.”
In other words and phrases, it is made to deliver alongside one another Computer software Bill of Components (SBOM) documents, SLSA attestations, OSV vulnerability feeds, deps.dev insights, and a company’s inner non-public metadata to enable build a improved photograph of the risk profile and visualize the interactions concerning artifacts, deals, and repositories.
Approaching WEBINARZero Believe in + Deception: Understand How to Outsmart Attackers!
Learn how Deception can detect advanced threats, stop lateral motion, and enrich your Zero Trust approach. Join our insightful webinar!
Conserve My Seat!
With such a setup in spot, the intention is to tackle superior-profile supply chain assaults, generate a patch plan, and quickly reply to security compromises.
“For illustration, GUAC can be used to certify that a builder is compromised (e.g., by means of credential leakage or ingestion of malware) and then question for affected artifacts,” Google claimed.
“This allows the [chief information security officer] to simply develop a coverage to forbid use of any application from within just the blast radius.”
Uncovered this write-up intriguing? Observe us on Twitter and LinkedIn to go through more unique written content we post.
Some parts of this article are sourced from:
thehackernews.com


 Lazarus Group Targeting Microsoft Web Servers to Launch Espionage Malware
Lazarus Group Targeting Microsoft Web Servers to Launch Espionage Malware