Unfamiliar malware presents a major cybersecurity risk and can cause really serious hurt to corporations and individuals alike. When remaining undetected, malicious code can get access to confidential facts, corrupt info, and permit attackers to get command of units. Uncover out how to stay away from these situations and detect unfamiliar destructive conduct competently.
Problems of new threats’ detection
Although known malware people are additional predictable and can be detected more simply, not known threats can acquire on a variety of varieties, producing a bunch of difficulties for their detection:
Detection of new threats
When analyzing acknowledged malware families, researchers can just take advantage of present information about the malware, this sort of as its conduct, payloads, and regarded vulnerabilities, in get to detect and reply to it.
But working with new threats, scientists have to get started from scratch, making use of the adhering to manual:
Move 1. Use reverse engineering to analyze the code of the malware to establish its reason and malicious character.
Move 2. Use static examination to examine the malware’s code to detect its behavior, payloads, and vulnerabilities.
Step 3. Use dynamic investigation to observe the conduct of the malware for the duration of execution.
Move 4. Use sandboxing to operate the malware in an isolated environment to observe its behavior devoid of harming the process.
Step 5. Use heuristics to determine possibly destructive code dependent on observable styles and behaviors.
Step 6. Evaluate the results of reverse engineering, static assessment, dynamic examination, sandboxing, and heuristics to identify if the code is destructive.
There are lots of resources from System Check and Wireshark to ANY.Operate to enable you go via the initially 5 methods. But how to attract a exact summary, what ought to you pay back notice to although getting all this info?
The remedy is straightforward – emphasis on indicators of destructive behavior.
Keep track of suspicious pursuits for successful detection
Various signatures are utilised to detect threats. In pc security terminology, a signature is a regular footprint or pattern involved with a malicious attack on a pc network or system.
Aspect of these signatures is behavioral kinds. It is impossible to do something in the OS and leave no tracing guiding. We can determine what application or script it was via their suspicious things to do.
You can operate a suspicious plan in a sandbox to notice the habits of the malware and detect any destructive actions, these types of as:
- abnormal file method action,
- suspicious course of action creation and termination
- irregular networking action
- reading or modifying system documents
- obtain system means
- produce new users
- connect to distant servers
- execute other malicious instructions
- exploit recognized vulnerabilities in the system
Microsoft Business is launching PowerShell – looks suspicious, appropriate? An software provides alone to the scheduled tasks – definitely pay out attention to it. A svchost process runs from the temp registry – a little something is undoubtedly mistaken.
You can always detect any danger by its conduct, even with out signatures.
Let’s show it.
Use circumstance #1
Here is a sample of the stealer. What does it do? Steals consumer details, cookies, wallets, etcetera. How can we detect it? For example, it reveals itself when the application opens the Chrome browser’s Login Details file.
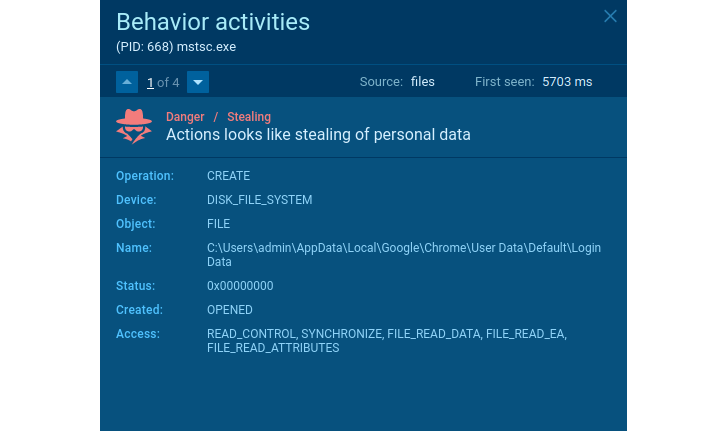 Stealer’s suspicious actions
Stealer’s suspicious actions
The action in the network site visitors also announces the threat’s destructive intentions. A legitimate application would never send qualifications, OS qualities, and other sensitive info collected domestically.
In the circumstance of visitors, malware can be detected by effectively-known characteristics. Agent Tesla in some cases does not encrypt data sent from an contaminated method like in this sample.
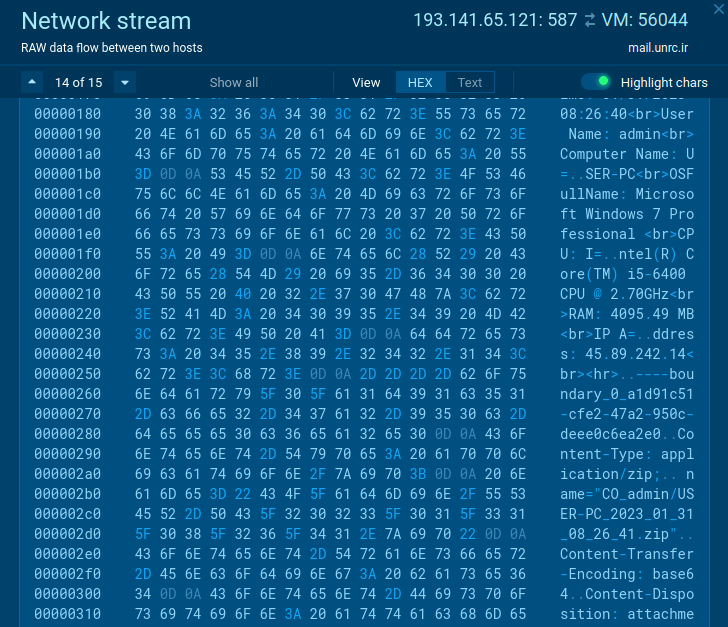 Suspicious exercise in the network website traffic
Suspicious exercise in the network website traffic
Use situation #2
There are not several genuine systems that need to end Windows Defender or other applications to shield the OS or make an exclusion for alone. Every time you come upon this form of behavior – that is a indication of suspicious activity.
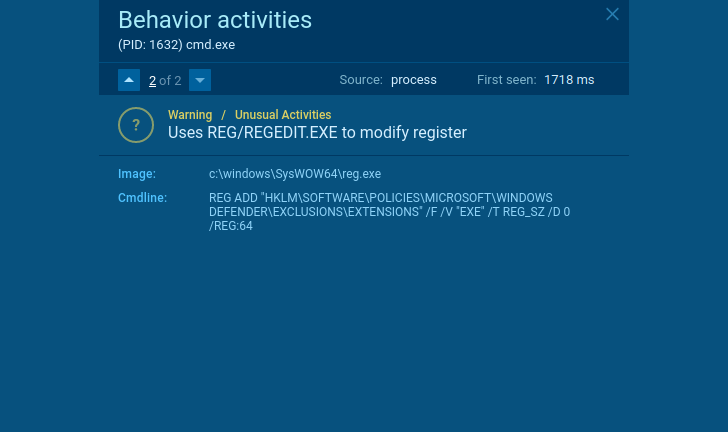 Suspicious actions
Suspicious actions
Does the application delete shadow copies? Seems like ransomware. Does it get rid of shadow copies and build a TXT/HTML file with readme textual content in each listing? It really is a single more evidence of it.
If the person facts is encrypted in the approach, we can be certain it is ransomware. Like what happened in this destructive case in point. Even if we do not know the household, we can identify what kind of security threat this software program poses and then act appropriately and just take actions to secure functioning stations and the organization’s network.
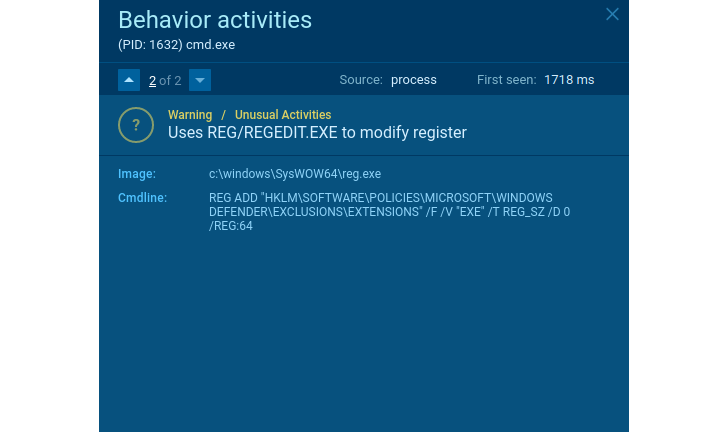 Suspicious habits
Suspicious habits
We can attract conclusions about almost all sorts of malware based on the actions observed in the sandbox. Try ANY.Operate on the web interactive services to keep an eye on it – you can get the very first results immediately and see all malware’s action in serious time. Specifically what we need to have to capture any suspicious functions.
Produce the “HACKERNEWS2” promo code at [email protected] making use of your organization email address and get 14 times of ANY.Operate premium membership for free of charge!
Wrapping up
Cybercriminals can use unfamiliar threats to extort organizations for revenue and start substantial-scale cyberattacks. Even if the malware relatives is not detected – we can often conclude the threat’s performance by contemplating its actions. Utilizing this facts, you can construct facts security to reduce any new threats. Habits assessment enhances your skill to reply to new and unknown threats and strengthens your organization’s defense devoid of additional prices.
Located this report exciting? Stick to us on Twitter and LinkedIn to read extra distinctive information we article.
Some parts of this article are sourced from:
thehackernews.com


 Google Reveals Alarming Surge in Russian Cyber Attacks Against Ukraine
Google Reveals Alarming Surge in Russian Cyber Attacks Against Ukraine