The Countrywide Institute of Benchmarks and Technology (NIST) is 1 of the common-bearers in world-wide cybersecurity. The U.S.-centered institute’s cybersecurity framework helps companies of all dimensions have an understanding of, control, and decrease their cyber-risk degrees and much better protect their info. Its worth in the combat versus cyberattacks are not able to be overstated.
Even though NIST has not instantly formulated benchmarks linked to securing the SaaS ecosystem, they are instrumental in the way we technique SaaS security.
NIST just lately produced its Guide to a Safe Enterprise Network Landscape. In it, they discuss the transformation from on-premise networks to many cloud servers. Accessibility to these servers, and the accompanying SaaS applications, is by means of the two protected and unsecured products and spots across disparate geography.
The shift to the cloud has properly obliterated the network perimeter. As a result, firms have greater their attack surface and are going through an escalation of attacks that span throughout network boundaries.
Relatively than concentration on network-centric security, security will have to just take a 3-pronged technique. The user, endpoint, and application are keys to defending data. This new paradigm emphasizes the great importance of identity, site, and contextual info connected with the person, unit, and services.
Discover how Adaptive Protect can enable implement NIST compliance.
The Applications to Fulfill Today’s Troubles
Today’s security tools have to have to scale to meet the volume, velocity, and wide variety of present day programs. They want to combine seamlessly with SaaS purposes and provide protection for the entire SaaS stack.
To be powerful, these equipment want to lessen human intervention for checking and remediation. Automation is critical for an ecosystem that needs safe configurations for each individual user account that has entry to the software. Large companies may perhaps have thousands and thousands of configurations to safe throughout their entire SaaS stack closing them manually is an unattainable undertaking.
SaaS Monitoring
SaaS security tools should be ready to integrate with all the applications on the stack and identify every software by the SaaS app’s APIs. Once connected, it need to keep an eye on the security configurations, staying inform to any improvements. This configuration drift can have intense penalties, as it exposes SaaS programs by eliminating the safeguards place in position to prevent unauthorized obtain. It wants to continuously keep track of applications, and issue alerts as risk raises.
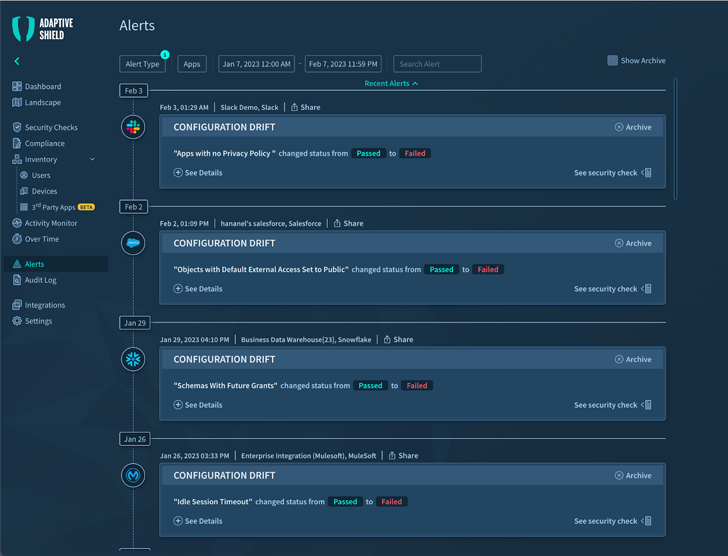 Determine 1. SaaS Checking in Adaptive Shield System
Determine 1. SaaS Checking in Adaptive Shield System
Contextual Information
Productive SaaS security resources use contextual details to detect threats to the application and its data. These threats can appear from individuals and equipment and could have accessibility to the program employing confirmed credentials.
Contextual knowledge from throughout the SaaS stack can aid identify paradoxical travel, spikes in unsuccessful authentication makes an attempt from the very same IP handle for a number of accounts, or makes an attempt wherever automated equipment take a look at weak and prevalent passwords in opposition to recognized person names. It can also realize malicious 3rd-celebration apps that are substantially overprivileged for their performance.
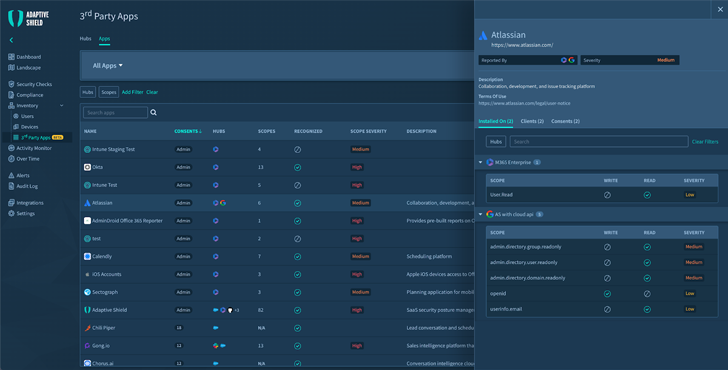 Determine 2. Contextual Knowledge as Seen in Adaptive Defend
Determine 2. Contextual Knowledge as Seen in Adaptive Defend
Get a demo of how Adaptive Protect can assist protected your SaaS stack
Device Management
In the entire world of SaaS, the gadgets represent the network perimeter. Accessing SaaS programs with gadgets that have very poor hygiene can put all the details at risk. Compromised equipment can hand over login qualifications to threat actors, who can leverage that into breaching and stealing information.
Helpful SaaS security equipment associate with endpoint security companies to guarantee that the equipment that access SaaS applications have an up-to-day running method, all computer software has been current, and any patches have been applied.
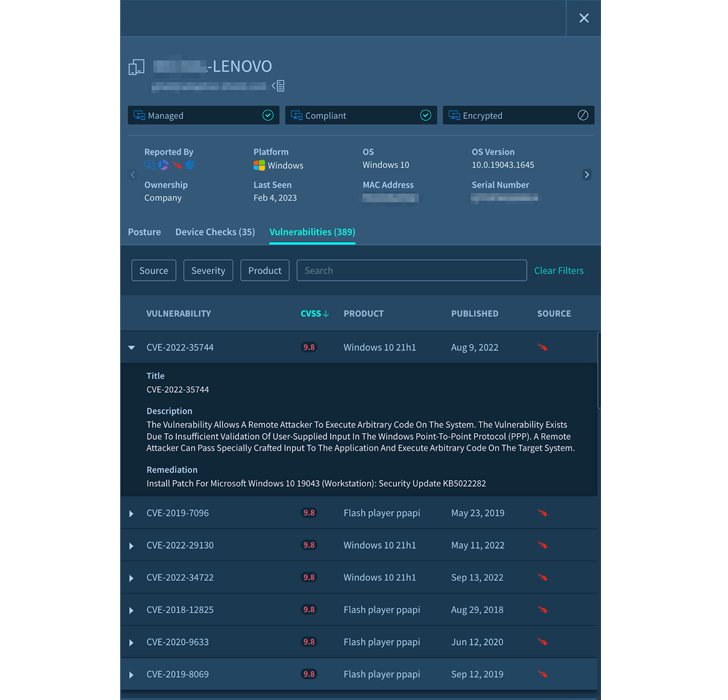 Figure 3. Unit Administration in Adaptive Defend Platform
Figure 3. Unit Administration in Adaptive Defend Platform
Consumer Authentication
Whilst devices may well be the perimeter, person ID is the barrier preventing unfettered entry to corporation details. Obtain should be presented employing a zero-belief solution. All accessibility should really be granted as a result of an SSO linked to an enterprise-managed IdP. Corporations must boost this entryway with a phishing-resistant MFA authenticator.
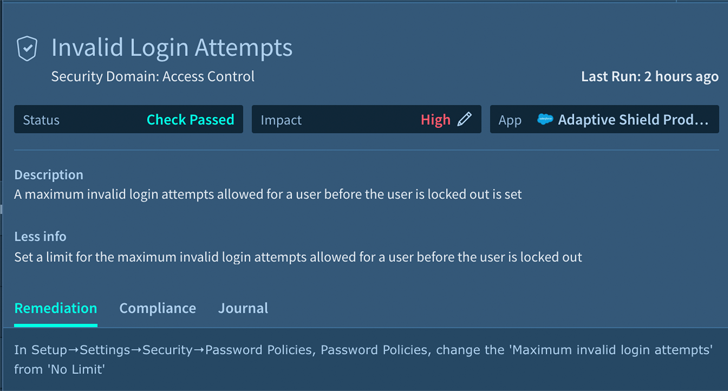 Determine 4. Invalid Login Tries Inform
Determine 4. Invalid Login Tries Inform
Meeting NIST Specifications
Successful SSPM platforms are built on sturdy security checks that evaluation each and every SaaS configuration to ensure they are optimized for protection. Usually, security placing recommendations are affected heavily by NIST’s cybersecurity method, and their guidance enables SSPM distributors to monitor and observe utilization, buyers, and behaviors, as well as determine threats.
See how Adaptive Shield’s SSPM could guard your SaaS stack
Discovered this post attention-grabbing? Abide by us on Twitter and LinkedIn to study far more special content material we submit.
Some parts of this article are sourced from:
thehackernews.com


 Blackbaud Settles $3m Charge Over Ransomware Attack
Blackbaud Settles $3m Charge Over Ransomware Attack