A governmental entity in Guyana has been focused as portion of a cyber espionage marketing campaign dubbed Procedure Jacana.
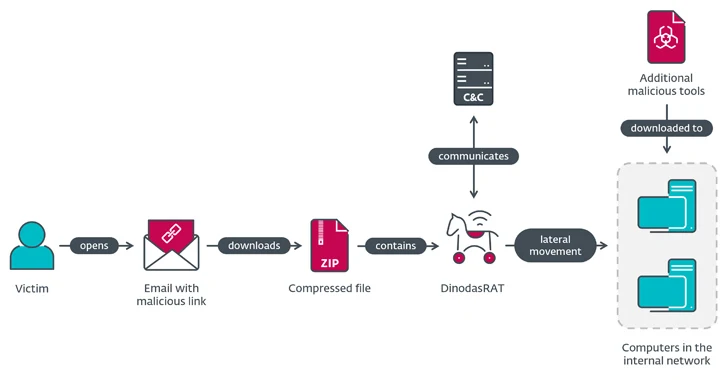
The activity, which was detected by ESET in February 2023, entailed a spear-phishing attack that led to the deployment of a hitherto undocumented implant written in C++ identified as DinodasRAT.
The Slovak cybersecurity agency mentioned it could hyperlink the intrusion to a known risk actor or group, but attributed with medium assurance to a China-nexus adversary owing to the use of PlugX (aka Korplug), a distant accessibility trojan popular to Chinese hacking crews.

“This campaign was focused, as the danger actors crafted their email messages precisely to entice their picked out sufferer group,” ESET reported in a report shared with The Hacker Information.
“Right after productively compromising an first but limited set of devices with DinodasRAT, the operators proceeded to transfer inside of and breach the target’s interior network, where they once again deployed this backdoor.”
The infection sequence commenced with a phishing email that contains a booby-trapped connection with topic traces referencing an alleged news report about a Guyanese fugitive in Vietnam.
Should a receiver click on on the link, a ZIP archive file is downloaded from the area fta.moit.gov[.]vn, indicating a compromise of a Vietnamese governmental site to host the payload.
Embedded in the ZIP archive is an executable that launches the DinodasRAT malware to accumulate sensitive details from a victim’s laptop.
DinodasRAT, moreover encrypting the information and facts it sends to the command-and-handle (C2) server utilizing the Little Encryption Algorithm (TEA), will come with abilities to exfiltrate procedure metadata, data files, manipulate Windows registry keys, and execute commands.

Also deployed are tools for lateral movement, Korplug, and the SoftEther VPN client, the latter of which has been set to use by an additional China-affiliated cluster tracked by Microsoft as Flax Typhoon.
“The attackers applied a blend of earlier unfamiliar equipment, these types of as DinodasRAT, and extra standard backdoors this kind of as Korplug,” ESET researcher Fernando Tavella stated.
“Centered on the spear-phishing e-mails used to obtain preliminary accessibility to the victim’s network, the operators are trying to keep observe of the geopolitical activities of their victims to maximize the chance of their operation’s achievements.”
Found this posting fascinating? Stick to us on Twitter and LinkedIn to go through a lot more unique written content we post.
Some parts of this article are sourced from:
thehackernews.com

 GoldDigger Android Trojan Targets Banking Apps in Asia Pacific Countries
GoldDigger Android Trojan Targets Banking Apps in Asia Pacific Countries