Today, much more malware developers are making use of unconventional programming languages to bypass sophisticated detection units. The Node.js malware Lu0Bot is a testament to this trend.
By concentrating on a platform-agnostic runtime surroundings frequent in fashionable web applications and using multi-layer obfuscation, Lu0Bot is a serious risk to organizations and people.
Although now, the malware has very low action, the attackers are likely ready for the right instant to strike.
To be well prepared for any future circumstance, a crew of analysts executed an in-depth complex evaluation of just one of the the latest samples of Lu0Bot and published an report documenting their approach.
Here’s an overview of their investigation.
Static assessment of the Lu0Bot sample
The sample less than investigation used an SFX packer, a self-extracting archive that can be opened with any archive utility. Its contents have been explored independently.
 Archive contents
Archive contents
1. BAT-file
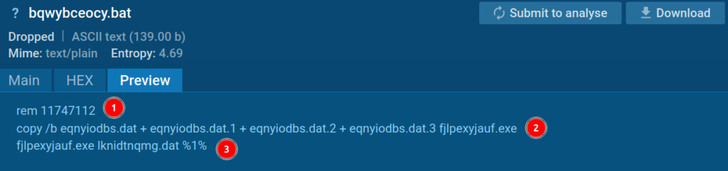 The material of the BAT file
The material of the BAT file
The 1st line in the file contained a comment that remained unclear and was not referenced afterwards.
Future, the EXE file bundled various documents, together with a Node interpreter referred to as fjlpexyjauf.exe.
Then, the interpreter acquired a file with bytes and a range (%1% in the screenshot) that probably served as the encryption critical for the byte file.
2. eqnyiodbs.dat data files
The file was divided into byte blocks, which were being then merged to produce the Node interpreter.
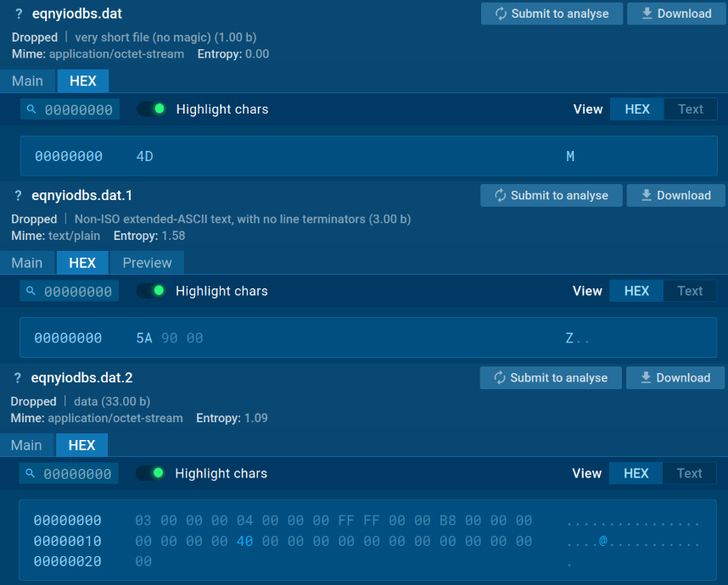 Contents of eqnyiodbs files
Contents of eqnyiodbs files
3. lknidtnqmg.dat file
This file had encrypted bytes in Base64, which could be decrypted working with the presented input variety.
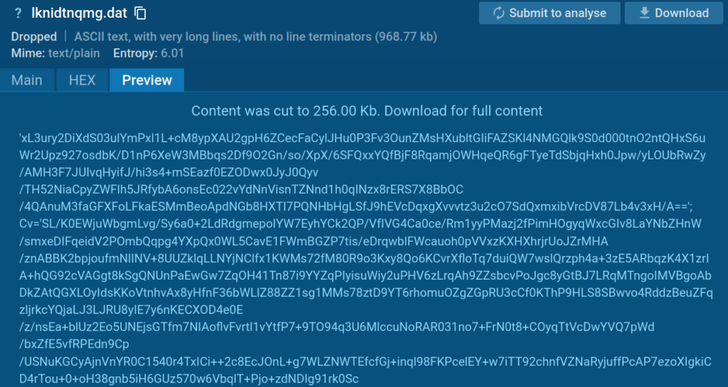 Contents of the lknidtnqmg.dat file
Contents of the lknidtnqmg.dat file
4. gyvdcniwvlu.dat file
This driver permitted 32-little bit programs on x64 techniques to change vital scan codes into Unicode characters, probably made use of for keylogging features in the primary process.
Dynamic malware investigation of Lu0Bot in ANY.Run
The upcoming step involved investigating the EXE file and lknidtnqmg.dat in the ANY.Run interactive malware sandbox to observe their conduct and possibly decrypt the bytes or identify them decrypted in the process memory.
The analysis unveiled that, upon execution, the most important method started off a BAT file that released an EXE file. The code recognized encrypted JS input and gathered process facts employing WMIC, including info about method execution place, which aligned with the T1047 MITRE approach.
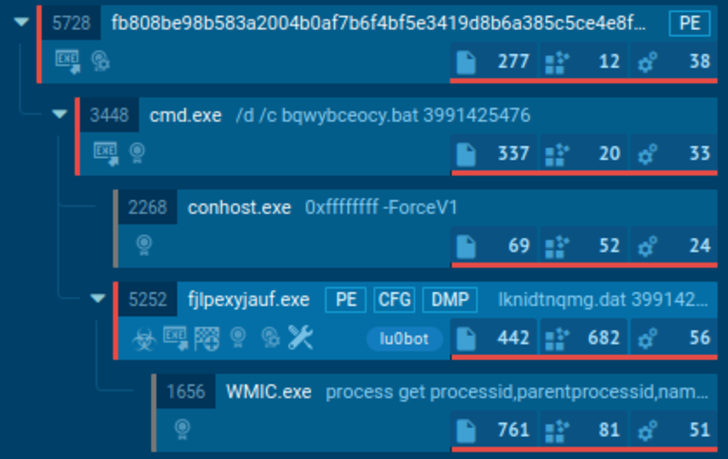 The procedure tree during sample execution
The procedure tree during sample execution
It was found out that the interpreter was copied to the startup folder. The link to the area continued right after the process restarted, allowing the bot to keep on being operational.
On top of that, the malware demonstrated a unique approach to area relationship by assembling a variety of areas into a solitary entity inside the JS code.
 DNS-requests
DNS-requests
Malware AnalysisUse a 14-working day free of charge demo to assess malware in the ANY.Run interactive sandbox.
Function with each other with your group in a private mode. Interact with data files and hyperlinks in a dedicated VM to expose their malicious behavior. Accumulate fresh new IOCs and configs in seconds.
Commence a totally free demo
Technological evaluation of Lu0Bot malware using a disassembler and debugger
To accessibility the principal JS code, the crew:
- Unpacked the SFX archive
- Ran a command to obtain the Node.js file
- Launched fjlpexyjauf.exe in x32dbg, moving into the incoming info into the command line
- Got to the position exactly where JS code execution started out
- Situated the code in memory and saved a dump
To see how the unpacking and dump extraction processes had been conducted, refer to the primary article. For this overview, let us focus on the code examination.
Examining the JS code
The at first unintelligible JavaScript code was designed obvious by getting rid of pointless bytes and utilizing a JavaScript deobfuscator.
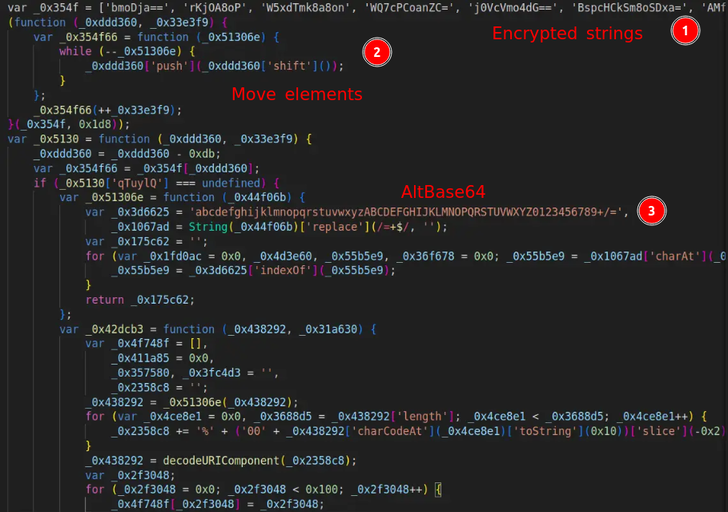 Result of code transformation
Result of code transformation
The code began with an array of encrypted strings. Then, distinct elements had been moved to the finish of the array by means of manipulation. Right after that, a perform was carried out to decrypt the array strings employing an substitute variety of Foundation64 (T1132.002), adopted by URL encode-decode, and finally, RC4.
This perform was identified as making use of two variables:
1. An component from the array.
2. The RC4 critical.
With the enable of a particular script, the strains had been decrypted, revealing that portions of the domains were difficult-coded into the sample.
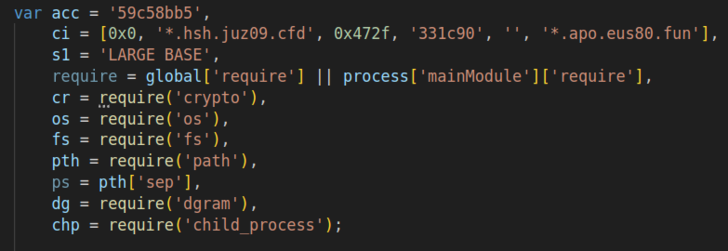 Immediately after code deobfuscation
Immediately after code deobfuscation
Next that, the area of the code accountable for assembling the area was uncovered.
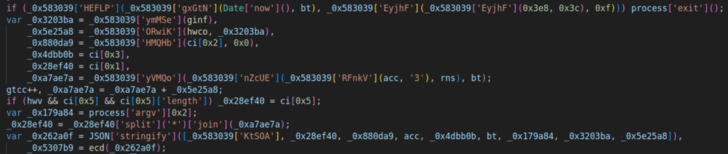 Domain development
Domain development
Debugging the JavaScript code
To debug, the group employed Node.js with its examine-brk parameter (node.exe –inspect-brk *obfuscate dump with out garbage bytes*), putting a breakpoint on the “var” key phrase and observing the output created by every single line.
It was found that the to start with function (ginf) collected procedure details and produced a 15-factor array with program aspects.
 An array that contains the output of the ginf purpose
An array that contains the output of the ginf purpose
The second functionality (hwco) applied the 15-factor array from the ginf purpose as input, which produced an output comprising the tail-conclusion of the area right up until the dot. Even more analysis unveiled that this output was a hash of the collected technique data.
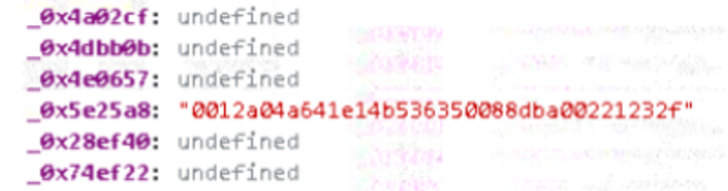 String output from the hwco operate
String output from the hwco operate
The port, number, and area phase after the dot ended up extracted from the acc array and then assigned to variables.
 Extracting elements from the acc array
Extracting elements from the acc array
A random quantity was included to the area segment after the dot. The subsequent line selected an choice domain if selected problems have been achieved.
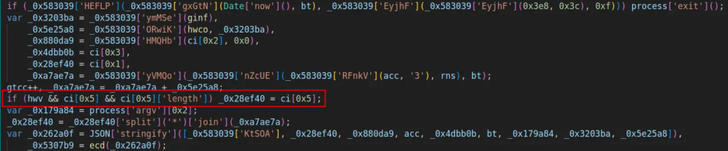 Choose area immediately after the position
Choose area immediately after the position
After various other operations, the area was completely assembled, and all needed factors had been packed into a JSON item.
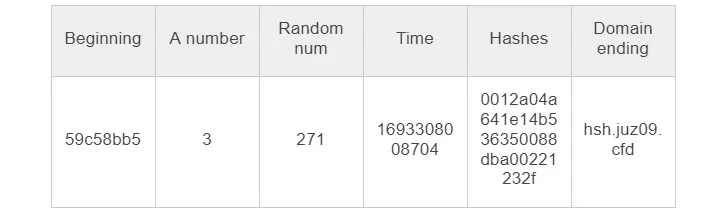
Soon after executing, the malware searched for an handle for data transmission. As soon as the server obtained the traffic, it despatched JS code.
Lu0bot detection
As part of their energy, the crew managed to uncover a wealth of intelligence and IOCs, as perfectly as wrote YARA, Sigma, and Suricata procedures. You can entry it in the write-up.
All of the results have been included into ANY.Operate, enabling the provider to speedily discover any Lu0Bot sample and expose C2 domains after decrypting strings.
Summary
Lu0bot is an uncommon malware that combines Node.js and executable JS code. It possesses a special domain framework and utilizes custom encryption methods for strings.
Whilst it currently reveals a reduced level of activity, Lu0bot can pose a significant risk if its marketing campaign scales and the C2 server commences actively responding.
Secure your business from this and other malware by employing ANY.Run to promptly assess any suspicious files or inbound links and get a conclusive verdict in seconds.
Found this report appealing? Abide by us on Twitter and LinkedIn to read through far more unique material we article.
Some parts of this article are sourced from:
thehackernews.com


 Guyana Governmental Entity Hit by DinodasRAT in Cyber Espionage Attack
Guyana Governmental Entity Hit by DinodasRAT in Cyber Espionage Attack