Google on Tuesday mentioned it can be piloting a new attribute in Chrome known as Product Sure Session Credentials (DBSC) to assistance safeguard consumers versus session cookie theft by malware.
The prototype – currently tested in opposition to “some” Google Account users managing Chrome Beta – is built with an goal to make it an open up web standard, the tech giant’s Chromium group claimed.
“By binding authentication sessions to the device, DBSC aims to disrupt the cookie theft field due to the fact exfiltrating these cookies will no extended have any worth,” the business noted.
“We believe this will significantly lessen the results fee of cookie theft malware. Attackers would be pressured to act regionally on the gadget, which can make on-machine detection and cleanup far more successful, the two for anti-virus software as very well as for company managed products.”
The progress comes on the again of studies that off-the-shelf facts thieving malware are locating techniques to steal cookies in a way that enables danger actors to bypass multi-issue authentication (MFA) defense and get unauthorized entry to on line accounts.

This kind of session hijacking tactics are not new. In October 2021, Google’s Danger Evaluation Team (TAG) in depth a phishing marketing campaign that specific YouTube written content creators with cookie thieving malware to hijack their accounts and monetize the accessibility for perpetrating cryptocurrency ripoffs.
Before this January, CloudSEK discovered that information stealers like Lumma, Rhadamanthys, Stealc, Meduza, RisePro, and WhiteSnake have updated their capabilities to hijack consumer sessions and permit constant accessibility to Google solutions even just after a password reset.
Google told The Hacker Information at the time that “attacks involving malware that steal cookies and tokens are not new we routinely update our defenses in opposition to this kind of tactics and to secure end users who fall victim to malware.”
It even further encouraged end users to help Increased Harmless Browsing in the Chrome web browser to guard towards phishing and malware downloads.
DBSC aims to slice down on this sort of destructive initiatives by introducing a cryptographic technique that ties with each other the classes to the unit this sort of that it would make it more difficult for the adversaries to abuse the stolen cookies and hijack the accounts.
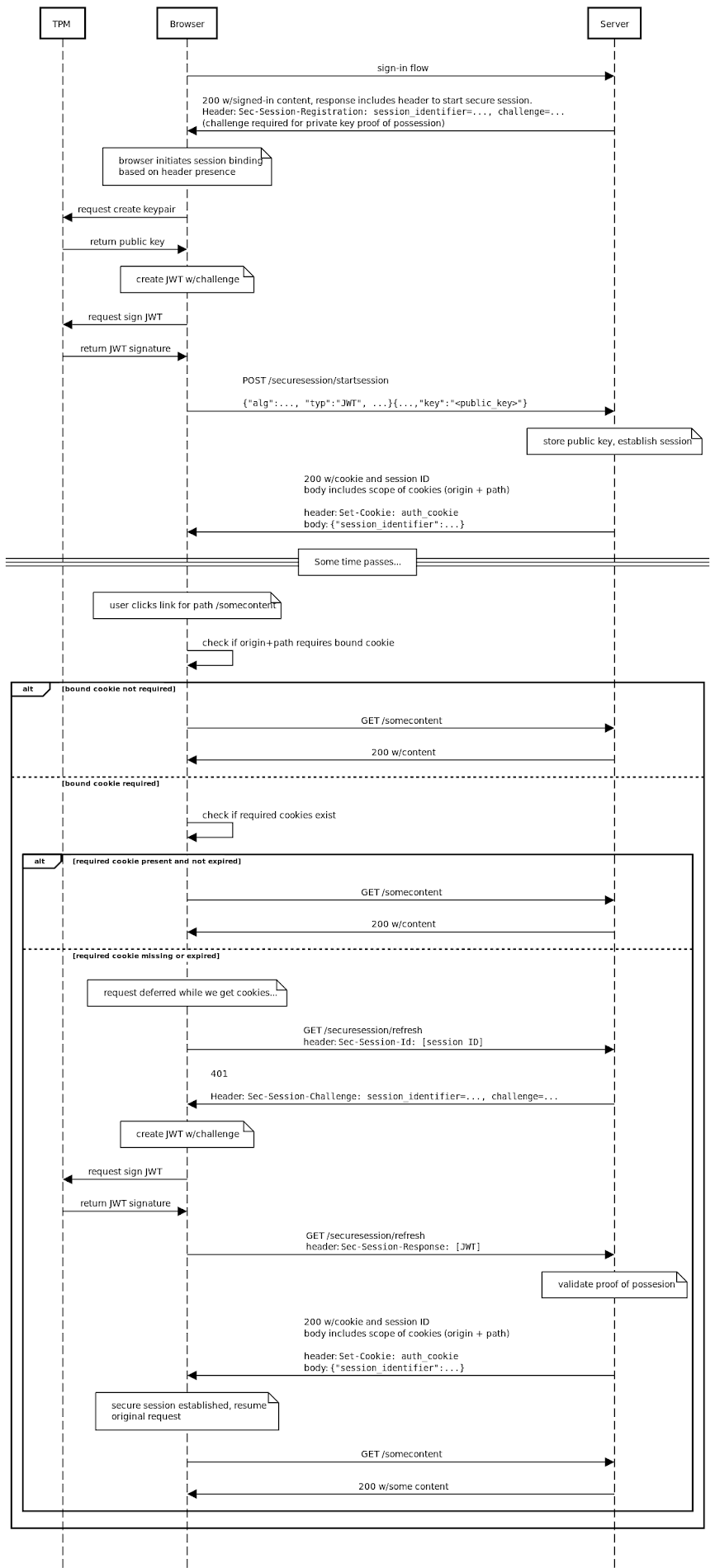
Available by way of an API, the new attribute achieves this by letting a server to affiliate a session with a general public critical made by the browser as aspect of a general public/non-public critical pair when a new session is launched.
It really is value noting that the vital pair is saved regionally on the product using Trusted System Modules (TPMs). In addition, the DBSCI API permits the server to verify evidence-of-possession of the personal vital through the session life time to ensure the session is active on the very same unit.
“DBSC gives an API for internet sites to manage the lifetime of these keys, guiding the abstraction of a session, and a protocol for periodically and quickly proving possession of people keys to the website’s servers,” Google’s Kristian Monsen and Arnar Birgisson explained.
“There is a separate vital for just about every session, and it should not be achievable to detect that two unique session keys are from just one device. By device-binding the non-public important and with suitable intervals of the proofs, the browser can limit malware’s potential to offload its abuse off of the user’s device, considerably growing the possibility that possibly the browser or server can detect and mitigate cookie theft.”

1 vital caveat is that DBSC financial institutions on person equipment acquiring a safe way of signing issues when safeguarding private keys from exfiltration by malware, necessitating that the web browser has accessibility to the TPM.
Google claimed assist for DBSC will be originally rolled out to around fifty percent of Chrome’s desktop buyers primarily based on the components abilities of their machines. The most current challenge is also envisioned to be in sync with the company’s broader plans to sunset third-bash cookies in the browser by the stop of the 12 months by way of the Privateness Sandbox initiative.
“This is to make guaranteed that DBSC does not turn out to be a new tracking vector after 3rd-social gathering cookies are phased out, although also making sure that these cookies can be fully safeguarded in the meantime,” it stated. “If the person totally opts out of cookies, 3rd-party cookies, or cookies for a distinct site, this will disable DBSC in individuals eventualities as properly.”
The business further mentioned that it can be partaking with many server companies, identity companies (IdPs), and browser vendors like Microsoft Edge and Okta, who have expressed curiosity in DBSC. Origin trials for DBSC for all supported sites are established to begin by the close of the calendar year.
Observed this short article appealing? Abide by us on Twitter and LinkedIn to study additional special written content we publish.
Some parts of this article are sourced from:
thehackernews.com


 Attack Surface Management vs. Vulnerability Management
Attack Surface Management vs. Vulnerability Management