Attack surface management (ASM) and vulnerability administration (VM) are frequently baffled, and whilst they overlap, they are not the exact. The most important distinction concerning attack area management and vulnerability administration is in their scope: vulnerability management checks a record of acknowledged property, while attack surface area management assumes you have unknown property and so starts with discovery. Let’s glimpse at each in more detail.
What is vulnerability management?
Vulnerability administration is, at the easiest amount, the use of automated instruments to detect, prioritize and report on security issues and vulnerabilities in your electronic infrastructure.
Vulnerability management works by using automatic scanners to run common, scheduled scans on belongings inside a recognized IP range to detect founded and new vulnerabilities, so you can use patches, get rid of vulnerabilities or mitigate any possible risks. These vulnerabilities are likely to use a risk score or scale – these types of as CVSS – and risk calculations.
Vulnerability scanners generally have quite a few countless numbers of automated checks at their disposal, and by probing and collecting details about your methods, they can identify security gaps which could be utilised by attackers to steal delicate data, attain unauthorized obtain to your units, or disrupt your enterprise. Armed with this expertise, you can protect your corporation and reduce prospective attacks.
 A screenshot of the Intruder vulnerability management system, which is made to perform thousands of security checks, identifying vulnerabilities in web applications, APIs, cloud programs, and outside of.
A screenshot of the Intruder vulnerability management system, which is made to perform thousands of security checks, identifying vulnerabilities in web applications, APIs, cloud programs, and outside of.
What is the vulnerability management process?
What is attack area administration?
The most important change among vulnerability administration and attack surface management is the scope. Attack surface area management (ASM) consists of asset discovery – assisting you to uncover all your digital assets and expert services and then lessening or minimizing their exposure to prevent hackers from exploiting them.
With ASM, all regarded or not known belongings (on-premises, cloud, subsidiary, 3rd-get together, or spouse environments) are detected from the attacker’s perspective from outdoors the firm. If you don’t know what you’ve got bought, how can you protect it?
Choose the case in point of an admin interface like cPanel or a firewall administration website page – these may possibly be secure against all known latest assaults right now, but a vulnerability could be identified tomorrow – when it turns into a substantial risk. If you observe and minimize your attack surface area, no matter of vulnerabilities, you turn into more difficult to attack.
So, a major part of attack area management is lessening exposure to doable long run vulnerabilities by removing avoidable companies and property from the internet. But to do this, to start with you have to have to know what is actually there.
What is the attack floor management approach?
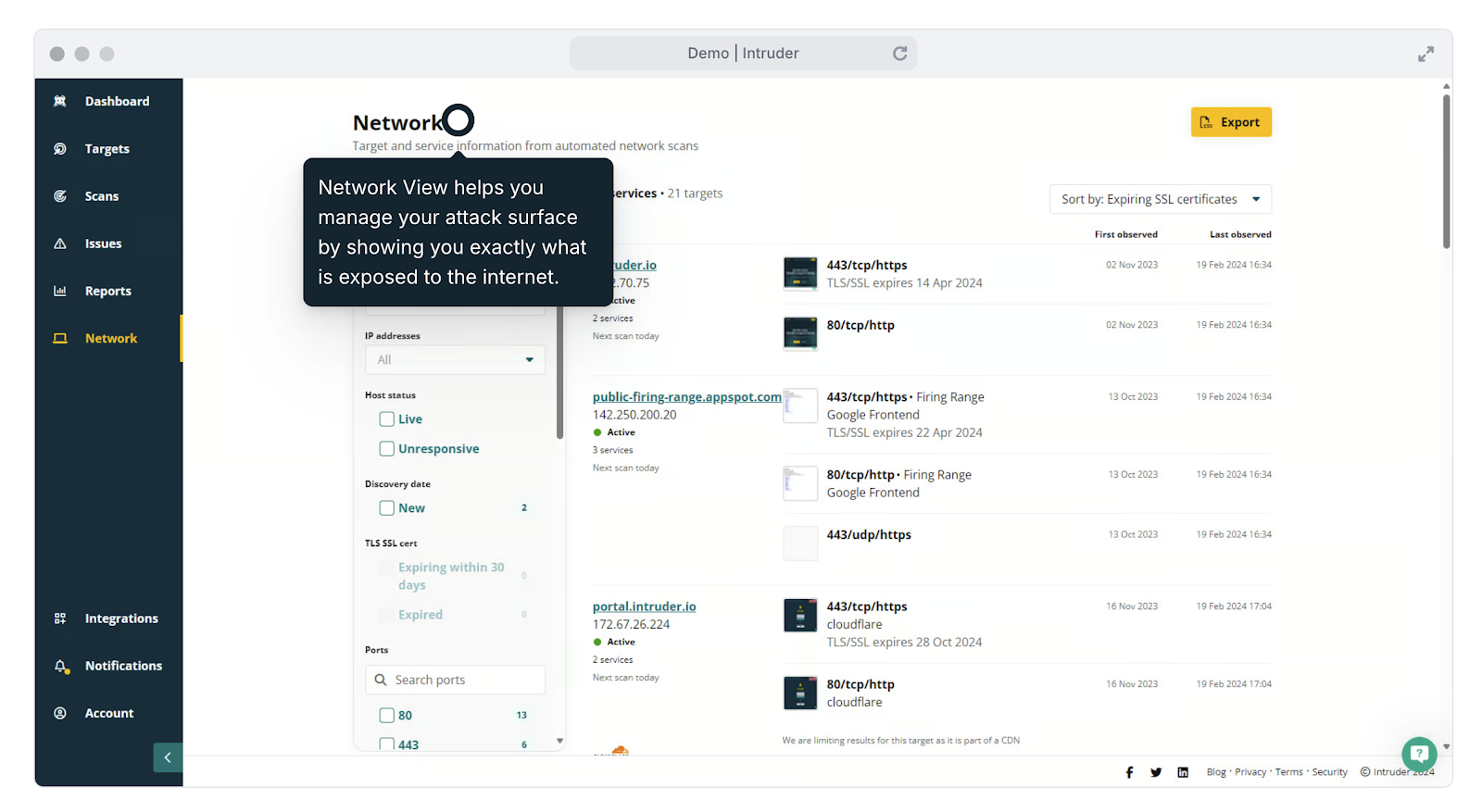 Intruder’s attack area management functions help you to keep on top of modifications in your ecosystem, these as lately opened ports and services.
Intruder’s attack area management functions help you to keep on top of modifications in your ecosystem, these as lately opened ports and services.
How does attack floor management vary from vulnerability administration?
Vulnerability administration is the course of action of figuring out and prioritizing vulnerabilities in your IT infrastructure and applications. Attack floor management goes a step further more by determining and examining your attack area – all the equipment, entry points and exposed solutions that an attacker could probably use to acquire access to your techniques or info.
Can you blend Attack Floor Management and Vulnerability Management?
Even though ASM and VM may well have unique scopes and objectives, they’re not mutually distinctive. Used in blend, they create a substantially extra holistic, robust and in depth cyber security posture. By pinpointing your assets and vulnerabilities, you can prioritize your security efforts and allocate methods more correctly – which will help you reduce the probability of a productive attack and any potential impression.
How Intruder can help with ASM and VM
In the end, you want to depart no stone unturned when it comes to cyber security. Contemporary VM and ASM alternatives like Intruder can detect vulnerabilities impacting your organization. It offers you better visibility and regulate over your attack area, screens network improvements and SSL/TLS certification expiry dates, aids you stay on major of your cloud infrastructure, and enables you to pay only for energetic targets. Why not see for oneself with a free 14-day trial?
Uncovered this article interesting? This posting is a contributed piece from one particular of our valued partners. Follow us on Twitter and LinkedIn to read extra exclusive content material we publish.
Some parts of this article are sourced from:
thehackernews.com


 Mispadu Trojan Targets Europe, Thousands of Credentials Compromised
Mispadu Trojan Targets Europe, Thousands of Credentials Compromised