Danger actors are creating bogus web-sites hosting trojanized software package installers to trick unsuspecting consumers into downloading a downloader malware named Fruity with the objective of setting up remote trojans instruments like Remcos RAT.
“Among the software in query are different devices for fantastic-tuning CPUs, graphic cards, and BIOS Laptop components-monitoring applications and some other apps,” cybersecurity vendor Medical professional Web explained in an investigation.
“These installers are applied as a decoy and have not only the software package opportunity victims are intrigued in, but also the trojan by itself with all its elements.”
The actual original access vector used in the marketing campaign is unclear but it could most likely array from phishing to push-by downloads to malicious advertisements. People who land on the pretend website are prompted to download a ZIP installer package.
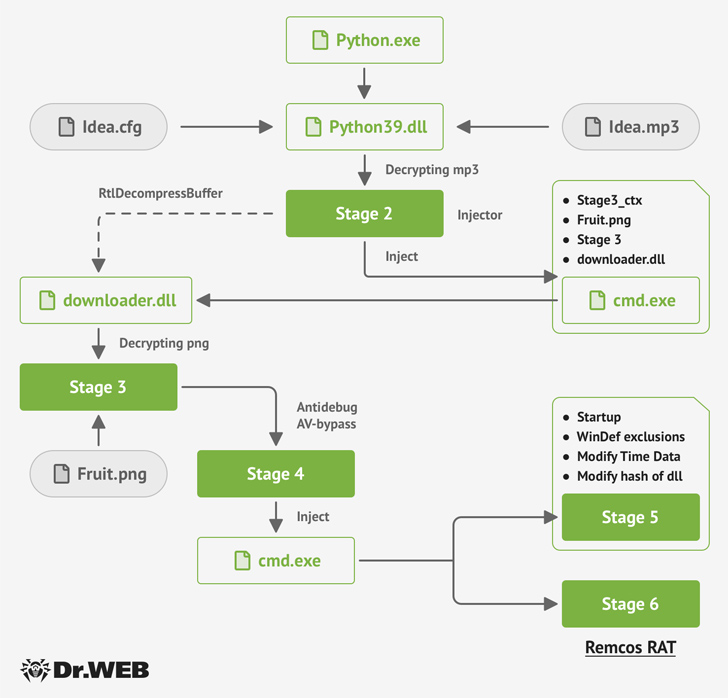
The installer, besides activating the regular set up method, stealthily drops the Fruity trojan, a Python-dependent malware that unpacks an MP3 file (“Concept.mp3”) to load an image file (“Fruit.png”) to activate the multi-stage infection.
“This image file makes use of the steganography approach to conceal two executables (.dll libraries) and the shellcode for the next-phase initialization inside it,” Medical professional Web stated.
Fruity is also intended to bypass antivirus detection on the compromised host and finally start the Remcos RAT payload employing a strategy referred to as approach doppelgänging.
That said, the attack sequence could be exploited to distribute all forms of malware, which tends to make it imperative that customers adhere to downloading software program only from reliable resources.
The improvement will come as Bitdfender disclosed aspects of a malspam campaign offering the Agent Tesla malware to harvest sensitive details from compromised endpoints.
It also follows a surge in malvertising functions that have targeted customers and enterprises with tainted software package boosted via ads on search engines.
Forthcoming WEBINARShield Towards Insider Threats: Master SaaS Security Posture Administration
Apprehensive about insider threats? We have obtained you lined! Join this webinar to examine simple procedures and the insider secrets of proactive security with SaaS Security Posture Administration.
Join Now
This involves a new wave of assaults dubbed Nitrogen in which fraudulent ISO archives are dispersed working with bogus advertisements that impersonate download webpages for apps these types of as AnyDesk, WinSCP, Cisco AnyConnect, Slack, and TreeSize.
“This malvertising campaign potential customers to the propagation of the infection immediately after initial exposure,” Bitdefender researchers Victor Vrabie and Alexandru Maximciuc claimed.
“For as prolonged as they dwell in the victim’s network, the attackers’ principal intention is to receive qualifications, established up persistence on essential programs and exfiltrate data, with extortion as the close intention.”
Observed this article appealing? Follow us on Twitter and LinkedIn to examine additional unique content material we submit.
Some parts of this article are sourced from:
thehackernews.com


 Growing bio-inspired polymer brains for artificial neural networks
Growing bio-inspired polymer brains for artificial neural networks