Extra particulars have emerged about a botnet termed AVRecon, which has been observed producing use of compromised tiny business/property place of work (SOHO) routers as part of a multi-year marketing campaign lively because at the very least May perhaps 2021.
AVRecon was initial disclosed by Lumen Black Lotus Labs before this month as malware capable of executing extra instructions and stealing victim’s bandwidth for what appears to be an illegal proxy company built obtainable for other actors. It has also surpassed QakBot in phrases of scale, possessing infiltrated over 41,000 nodes located throughout 20 nations around the world around the world.
“The malware has been employed to generate residential proxy companies to shroud destructive activity this kind of as password spraying, web-traffic proxying, and advert fraud,” the scientists stated in the report.
This has been corroborated by new findings from KrebsOnSecurity and Spur.us, which final 7 days discovered that “AVrecon is the malware engine behind a 12-calendar year-previous company identified as SocksEscort, which rents hacked household and little company units to cybercriminals hunting to conceal their legitimate area on-line.”
The foundation for the link stems from immediate correlations among SocksEscort and AVRecon’s command-and-manage (C2) servers. SocksEscort is also reported to share overlaps with a Moldovan company named Server Management LLC that offers a cell VPN solution on the Apple Store named HideIPVPN.
Black Lotus Labs informed The Hacker Information that the new infrastructure it discovered in relationship with the malware exhibited the similar characteristics as the old AVrecon C2s.
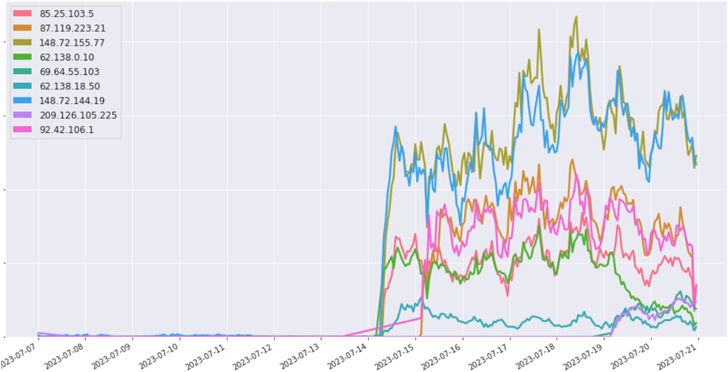
“We evaluate that the danger actors ended up reacting to our publication and null-routing of their infrastructure, and making an attempt to maintain management around the botnet,” the organization reported. “This implies the actors desire to additional monetize the botnet by protecting some access and go on enrolling customers in the SocksEscort ‘proxy as a services.'”
Routers and other edge appliances have develop into rewarding attack vectors in modern several years owing to the truth that this kind of gadgets are infrequently patched towards security issues, may well not support endpoint detection and reaction (EDR) options, and are developed to deal with increased bandwidths.
Impending WEBINARShield Against Insider Threats: Grasp SaaS Security Posture Administration
Concerned about insider threats? We have acquired you covered! Be part of this webinar to explore simple techniques and the secrets and techniques of proactive security with SaaS Security Posture Management.
Join Today
AVRecon also poses a heightened risk for its potential to spawn a shell on a compromised device, most likely enabling risk actors to obfuscate their very own destructive website traffic or retrieve even more malware for write-up-exploitation.
“When these bots are principally becoming extra to the SocksEscort proxy services, there was embedded operation inside of the file to spawn a remote shell,” the researchers stated.
“This could permit the threat actor the ability to deploy supplemental modules, so we counsel that managed security providers attempt to investigate these gadgets in their networks, whilst dwelling users must ability-cycle their devices.”
Observed this report interesting? Comply with us on Twitter and LinkedIn to study far more special articles we submit.
Some parts of this article are sourced from:
thehackernews.com


 Fruity Trojan Uses Deceptive Software Installers to Spread Remcos RAT
Fruity Trojan Uses Deceptive Software Installers to Spread Remcos RAT